An infamous Zloader malware is back, according to the most recent report of malware sandbox ANY.RUN. The researchers not only detected the rise in activity of the before-offline malware, but also managed to analyze the new sample and find some interesting changes.
Zloader Malware Is Back Online
Back in April 2022, Microsoft managed to stop and dismantle the entire network of command servers that were used to control vast botnets led by Zloader. This was what looked like the end of this malware: even though C2 dismantlement is not leaders’ detainment, the recovery process may be both protracted and costly. And since there were no signs or resurrection for almost 2 years, analysts considered that Zloader is no more.
It looks like they were mistaken though. The latest ANY.RUN report covers a significant surge in Zloader activity that is hard to confuse with anything else than a comeback. Sure, it is not as massive as you can expect, but such recoveries never go fast. And nonetheless, the renewed malware version has some serious changes to be concerned about.
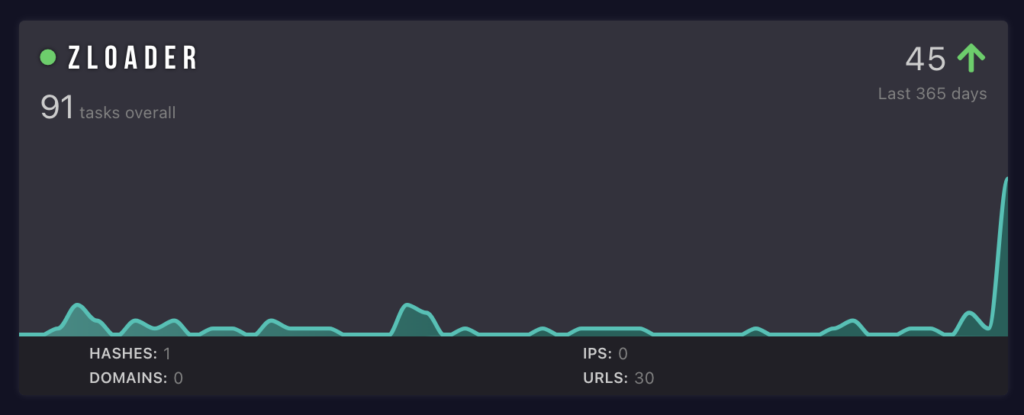
Surge in Zloader activity graph. Data by ANY.RUN
Being a loader malware, Zloader mainly bears on 2 things – stealthiness and wide payload deployment functionality. In the new version, changes are concentrated around the former. In particular, malware now has random junk code inserts across the binary; the code itself is more obfuscated and encrypted with RC4. With the hardcoded decryption key and the check for a proper file name, the new Zloader is also much harder to analyze.
Analysis additionally underscores that these new versions of malware have the info about the campaign and C2 servers hidden. Such a change though only restricts static analysis of the sample, while all this info is easy to collect under dynamic testing.
What is Zloader Malware?
Zloader, as it comes from its name, is a loader malware that was originally detected in 2015 under the name of Terdot. Being an offspring of an infamous Zeus malware, it was first an infostealer that at some point got the ability to deploy additional payloads. This determined the further fate of the malware: stealer capabilities became secondary, while the majority of its attacks were intended to deploy other malware.
Throughout its activity, Zloader was used to deliver various ransomware and backdoors, particularly Cobalt Strike. Malware itself could act as a backdoor, adding the remote VNC capability. At some point, the botnet of Zloader was big enough for its masters to start offering anyone to deploy the needed malware to this network. Eventually, such activity led to the increased attention from law enforcement, which ended with the shutdown I’ve mentioned above.
How to Protect Yourself?
The ways to avoid malware may look complicated, but most of them are rather easy to follow. The key here is to follow all rules simultaneously; by sticking to one or two of them, you leave enough room for malware to enter.
Be careful of email messages. Phishing emails remain the primary malware spreading vector. Hackers rely on making these emails as similar to originals as possible, but some things are impossible to spoof. Check the email addresses and be vigilant to the topic: frauds tend to use the most generic ones.
Avoid cracked programs. Cracked apps were and still remain a perfect breeding ground for malware. As their installation often requires disabling antivirus software, injecting malware into the package becomes a major temptation. License for a program may be much cheaper than dealing with malware consequences.
Use a reliable anti-malware program. Anti-malware program acts as a gatekeeper, catching what has passed through. Malware constantly seeks for new spreading approaches, so it is always a great idea to have such a backup option. GridinSoft Anti-Malware is a great option for such a case.

