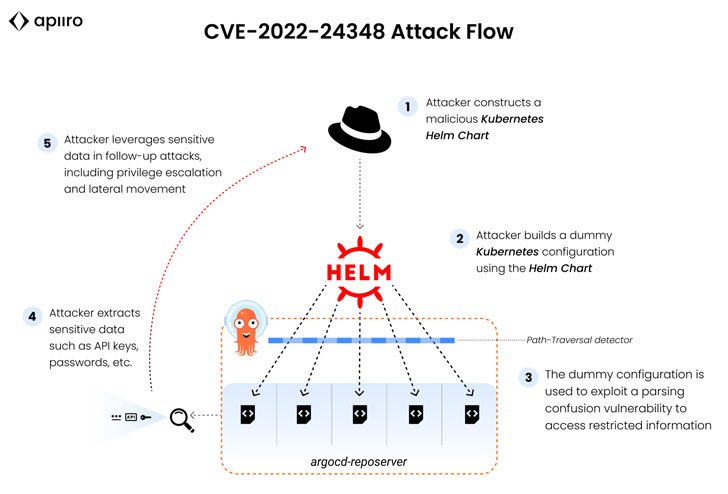
A vulnerability in the Argo CD tool, used by thousands of organizations to deploy applications to Kubernetes, could be used for lateral movement, privilege escalation, and to steal sensitive data, including passwords and API keys.
It is worth noting that Argo CD is officially used by many large companies, including Alibaba Group, BMW Group, Deloitte, Gojek, IBM, Intuit, LexisNexis, Red Hat, Skyscanner, Swisscom and Ticketmaster.The problem, discovered at the end of January by Apiiro specialists, is CVE-2022-24348 (CVSS score 7.7) and affects all versions of Argo CD. The bug has already been fixed in the latest versions 2.3.0, 2.2.4 and 2.1.9.
The vulnerability is of type path-traversal (directory traversal) and allows attackers to download specially crafted Helm Chart YAML files, “leaving” their application ecosystem and gaining access to other applications’ data, which should be outside the user’s scope.
The creators of Argo CD recommend that everyone update to the fixed versions as soon as possible, as there are no workarounds to fix this problem.
Let me remind you that we also wrote that Apache Vulnerability May Lead to Remote Code Execution, and also that VMware Alerts That Critical Vulnerability Has Been Found In vCenter Server.

