Is a VPN Software useful?
Yes, a Virtual Private Network software can be very useful for a variety of reasons
A VPN creates a secure and encrypted connection between your device and the internet, protecting your online privacy and security. When connected to a VPN, all of your internet traffic is routed through an encrypted tunnel which prevents anyone from intercepting or monitoring your activities online.
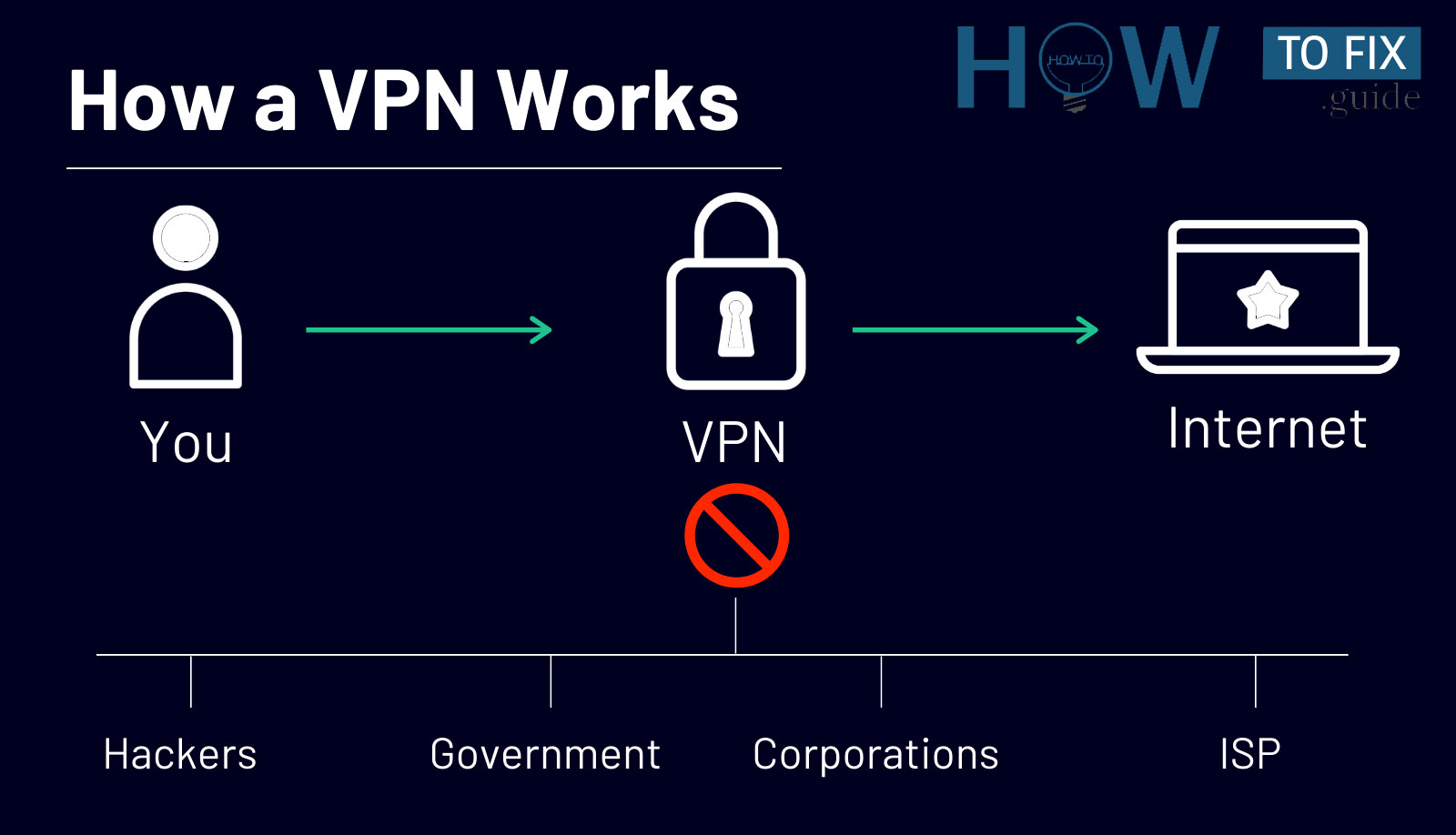
How does a Virtual Private Network work?
Some of the advantages of using VPN software include:
- Improved Online Privacy: A VPN can protect your online privacy by masking your IP address and encrypting your activities. This prevents advertisers, ISPs, and other third parties from tracking your online movements.
- Enhanced Security: A VPN can protect your device from cyber threats such as malware, phishing attacks and hacking attempts. Furthermore, the encryption provided by a VPN helps prevent unauthorized access to sensitive data and personal information.
- Access geo-restricted content: With a VPN, you can gain access to websites and content that may be blocked or restricted in your region, such as streaming services or social media sites.
- Secure Remote Access: A VPN can offer secure remote access to your company’s network or enable you to access personal files and documents from anywhere in the world.
However, it’s essential to remember that not all VPNs are created equal and some may not offer adequate security or privacy protections. Therefore, when selecting a reliable VPN provider that prioritizes user privacy and security, make sure they use strong encryption and security protocols.
Virtual Private Network & Online Security
Virtual Private Networks can be a key element in increasing your online security by creating an encrypted and secure connection between your device and the internet.
Here are some ways a VPN can boost your protection:
- 🟢 Encryption: A Virtual Private Network encrypts your internet traffic, shielding it from anyone intercepting or eavesdropping on your online activities. This is especially crucial when using public Wi-Fi networks which are often unprotected and vulnerable to hacking attacks.
- 🟢 Anonymity: Utilizing a VPN can mask your IP address and location, protecting your privacy while blocking tracking by advertisers, ISPs, and other third parties.
- 🟢 Protection Against Cyber Threats: A VPN can shield your device against various cyberattacks such as malware, phishing scams and hacking attempts. This is especially essential if you frequently access sensitive information or perform financial transactions online.
- 🟢 Bypassing Censorship and Geoblocking: With a Virtual Private Network, you can access websites and content that may be blocked or restricted in your region, such as social media sites or streaming services.
However, it’s essential to select a trustworthy VPN provider that prioritizes user privacy and security with strong encryption and security protocols. Furthermore, using a VPN should only be one component of an overall online security strategy; other essential measures include using strong and unique passwords, keeping software and security tools up-to-date, as well as being vigilant against phishing attacks and other social engineering tactics.
How to use VPN?
Setting up and using a Virtual Private Network is an intuitive process.
Here are the basic steps for setting up and using your Virtual Private Network:
- Select a Reputable VPN Provider: With so many available, it’s essential to pick one that prioritizes user privacy and security. Popular providers include NordVPN, ExpressVPN, and CyberGhost; each provides excellent options for those seeking online privacy protection.
- Once you’ve selected a Virtual Private Network provider, download and install their software onto any devices – desktops, laptops, smartphones or tablets. Most providers offer software for various platforms so this step should be relatively painless for you.
- Connect to a VPN Server: Once the software has been installed, you’ll need to connect to a VPN server. Most software will let you select a server location so that you can pick one in an area that best meets your needs (e.g., for accessing content that may be restricted in your region).
- Utilize the internet normally: Once connected to a VPN server, you can utilize the internet as usual. All of your traffic will be encrypted and routed through the VPN server for extra privacy and security.
Some additional tips for using a Virtual Private Network include:
- 👌 Select a server location close to your physical location to minimize latency and optimize connection speeds.
- ⚠️ Avoid free VPN services that may not offer adequate security or privacy protections.
- 😋 Maintain your VPN software and operating system by applying the latest security patches and updates.
- 🚫 Disconnect from the Virtual Private Network when not in use to save bandwidth and improve connection speeds.

