The majority of email security filters are exceptionally helpful at making sure that spam emails never sneak into the inbox. Nevertheless, they’re far less efficient when it comes to blocking phishing, which is known as a more complex problem to resolve. Current phishing methods are pretty much tricky, they’re able to bypass email security filters, and they’re attacking your customers and staff.
A well-tailored phishing email in many cases looks almost identical to a real email from a well-known company. Often people click on phishing links, thinking they’re related to well-known giants, such as Microsoft and PayPal, believing they’re logging into a genuine account. In certain phishing attacks, victims unintentionally transfer their credentials to online frauds. More often it happens that the victims click a phishing link or attachment that leads to the malware or ransomware injection on their devices.
The below-said phishing methods are extremely sophisticated obfuscation approaches that online frauds use for the purpose of bypassing Office 365 security. Most likely, they’re extremely difficult to be discovered by the customer and thus can bypass Exchange Online Protection (EOP) and secure email gateways (SEGs) without any substantial complications.
Applying genuine links
The majority of email filters regularly analyze known harmful URLs. To avoid identification, phishers insert genuine links to their phishing emails. A lot of email filters will scan a range of decent links and come to the conclusion that the email is safe. In latest Microsoft Office 365 phishing1 emails revealed by HowToFix.Guide, the phisher pasted a decent reply-to email address and genuine links to Microsoft’s community, legal, and privacy pages. They also added a link to Microsoft’s contact preferences webpage, where customers can update their chosen communications parameters for programs like SharePoint and OneDrive.
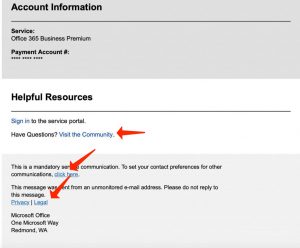
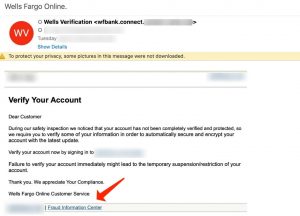
In the below-given case of a Wells Fargo phishing email identified by Vade Secure, the phisher even pasted a link to the bank’s fraud data center.
Mixing genuine and malicious codes
A known phishing email or malware infection has got a signature that can be identified by EOP. One method for obfuscating the signature is to mix genuine and malicious code. Sophisticated Microsoft phishing webpages, for instance, have got CSS and JavaScript from real Microsoft pages, such as the Office 365 sign-in webpage. Other methods may involve encoding characters at random, providing invisible text, pasting white spaces, and specifying random parameters to HTML attributes. The purpose of mixing decent and malicious code is to make sure that each email is deemed to be unique to the filter.
Applying redirections and link shorteners
Time matters a lot when it comes to phishing. To trick potential victims into believing that nothing is out of the square, phishers tend to redirect them to a decent webpage after the phishing attack. For instance, once a victim provides the Office 365 login details on a dangerous webpage, they are forwarded to Office 365.com or another Microsoft-owned resource.
Another example of redirect abuse, “time-bombing” is a phishing approach that is related to elaborating a URL redirect from a legitimate resource to a phishing webpage. Time-bombing is extremely effective due to the fact that the email includes a decent Microsoft link at the moment of delivery when it is in first place scanned by an email filter; the redirect to the phishing site is only formed after the email has successfully reached the victim’s device.
In another method applied for the purpose of obfuscating a well-known phishing link, phishers refer to the help of URL shorteners, for instance, to TinyURL and Bitly. Such cost-free utilities modify long URLs into shortened links—aliases that have no similarity with the initial URL. The majority of email filters that are examining a signature would fail to recognize it in a shortened phishing URL.
Obfuscating company logos
Similar to other components of well-known phishing pages, logos may have certain HTML attributes that can be identified by an email filter that is searching for signatures. To prevent detection, phishers modify company logos to make sure that they are invisible to a human eye but unique to a filter. For instance, by amending an HTML parameter, such as color or shape by a single character, the signature will be almost identical to a known phishing page, thus absolutely unique. This insignificant modification is sufficient to deceive an email filter that inspects for malicious data but fails to analyze the display of an image as a human would.
Deluding the filter with little content or excess noise
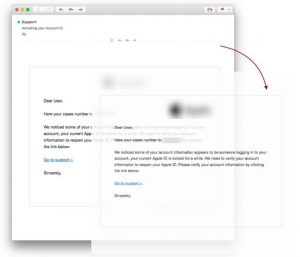
Certain online frauds avoid detection by adding little to no content into their phishing emails. One kind of this attack that we’re revealing quite often is the application of an image instead of text, even though this is not often clear to the customer. This is a common approach applied in sextortion2 emails, with its massive campaign revealed in 2018. With no content to research, the filter could be tricked into believing the email doesn’t represent any risks at all. In the below-given case, the text you see is in reality an image.
The opposite method is to load an email with excessive content or “noise.” This approach is often successful due to the randomness of the code.
What can you do to defend your customers?
The ever-growing sophistication of phishing campaigns requires more sophisticated reactions. Common email filters are no longer sufficient enough. Customers using Office 365 have to layer additional security with EOP3.
User Review
( votes)References
- Anti-phishing protection in Microsoft 365: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-phishing-protection?view=o365-worldwide
- Sextortion: https://en.wikipedia.org/wiki/Sextortion
- Anti-phishing protection in EOP: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-phishing-protection?view=o365-worldwide#anti-phishing-protection-in-eop


![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian

