Information security experts continue to warn about the dangers of the ESXiArgs ransomware: this time, Rapid7 experts have calculated that 18,581 VMware ESXi servers are still vulnerable to exploiting the CVE-2021-21974 vulnerability, which is used by hackers.
Let me remind you that thousands of VMware ESXi servers were hacked by the new ESXiArgs ransomware in early February. The attackers used the mentioned two-year-old vulnerability (CVE-2021-21974), which allowed them to execute remote commands on vulnerable servers through OpenSLP (port 427). It should be noted that the bug was fixed a long time ago, a patch for it was released back in 2021, just not everyone bothered to install it.At the same time, VMware developers have stated that hackers definitely do not use any zero-day vulnerabilities, and OpenSLP is generally disabled by default after 2021.
That is, attackers are targeting products that are “significantly outdated,” and there were quite a few of them. So, according to experts, about 3,800 organizations in the US, France, Italy and other countries have already been hacked.
Let me remind you that information security experts managed to find a number of flaws in ESXiArgs, due to which it was possible to restore encrypted VMware ESXi servers without paying a ransom.
However, the joy was premature. Bleeping Computer journalists reported that the second wave of ESXiArgs infections has begun, and now hackers are using an improved encryption procedure that encrypts much more data in large files.
For example, the malware used the encrypt.sh script and the following formula (slightly modified for readability) to determine which size_step to use: size_step=((($size_in_kb/1024/100)-1)). Now the malware encoder has not changed, but the complex size_step calculation has been removed from the encrypt.sh script. In the new version, it is simply set to “1”.
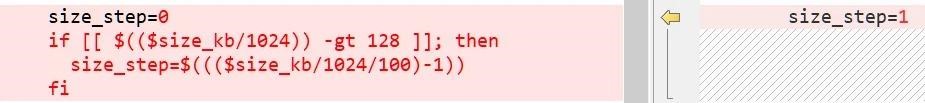
First (left) and second (right) versions of size_step
Security expert Michael Gillespie told reporters that the change will force the malware to alternate between encrypting 1MB of data and skipping 1MB of data. Thus, all files larger than 128 MB will now have 50% of the data encrypted, which will most likely make them unrecoverable.
As a result, according to the Ransomwhere project, 1,252 servers were infected with the new version of the ransomware at the end of last week, and the new version of ESXiArgs already accounted for 83% of active infections.
As Rapid7 analysts now report, successful ESXiArgs attacks do not appear to have gone unnoticed by other attackers. Experts write that they are already seeing additional attacks on CVE-2021-21974 that are not related to ESXiArgs.
We also published: US Authorities List Vulnerabilities That Chinese Hackers Attack.

