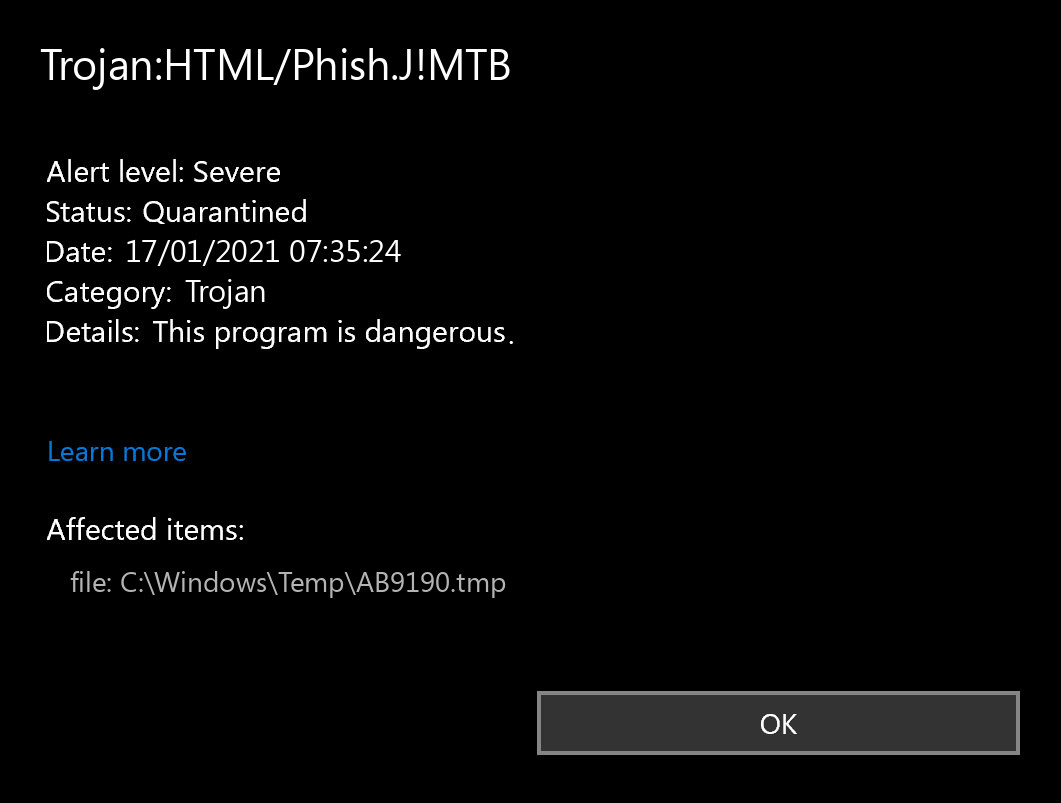
The Trojan:HTML/Phish.J!MTB notification, is a sign that your system has a problem. Allowing it to keep running may lead to really bad consequences. Phish grants the crooks an easy access to your computer, or perhaps connects it to the botnet.
Backdoors like Phish are versatile viruses that are able to act as self-sufficient malware, or be used in multi-stage attacks. Their main target is creating a remote connection to the target computer, that functions without the owner’s knowledge. To avoid any interruptions, this malware type aims at staying as stealthy as possible.
Trojan:HTML/Phish.J!MTB Detection Overview
The Trojan:HTML/Phish.J!MTB detection you can see in the lower right side is demonstrated to you by Microsoft Defender. That anti-malware application is pretty good at scanning, however, prone to be generally unreliable. It is defenseless to malware attacks, it has a glitchy interface and bugged malware clearing capabilities. For this reason, the pop-up which states concerning the Phish is simply an alert that Defender has detected it. To remove it, you will likely need to use another anti-malware program.
The exact Trojan:HTML/Phish.J!MTB malware is a very nasty thing. This malware is designed to be a sneaky burglar, which functions as a remote-access tool. When you provide somebody remote access willingly, it is alright, but Phish will not ask you if you want to grant it. After connecting to your system, crooks are free to do whatever they want – snatching your files, examining your messages, gathering personal info, and so on. Backdoors commonly carry a supplementary stealer – the virus that is created to pick up all possible information about you. However, a lot more prevalent use of the backdoors is creating the botnet. After that, the network of corrupted systems can be used to conduct DDoS attacks or to inflate the poll results on different sites.
Backdoor Summary:
| Name | Phish Backdoor |
| Detection | Trojan:HTML/Phish.J!MTB |
| Damage | Gain access to the operating system to perform various malicious actions. |
| Similar | Trojan Msil Mamut, Hupigon, Luadream Malware, Pysilon Rat Malware, Sponsor Malware, Bladabindi, Loda Rat Malware, Rukap |
| Fix Tool | See If Your System Has Been Affected by Phish backdoor |
Shortly about backdoors
Backdoors are viruses that may acquire both separated and built-in forms. One time you may find that an official program from a widely known company has a capability that makes it possible for someone to connect to your computer. Will it be somebody from the creators or a 3rd party – no one knows. But the scandal when this feature is discovered in a legitimate program is pretty much impossible to miss. There is also chatter that there is a hardware-based backdoor in Intel CPUs1.
Is Trojan:HTML/Phish.J!MTB dangerous?
As I have specified before, non-harmful malware does not exist. And Trojan:HTML/Phish.J!MTB is not an exclusion. This backdoor does not deal a many damage exactly after it releases. Nonetheless, it will be a really bad surprise when an occasional online forum or website in the Web will not let you in, since your IP-address is disallowed after the DDoS attack. But even if it is not crucial for you – is it pleasurable at all to understand that somebody can simply access your PC, check out your discussions, open your files, and spectate what you do?
The spyware that is frequently present as a supplement to the Trojan:HTML/Phish.J!MTB malware will likely be just one more argument to remove it as fast as you can. Nowadays, when users’ information is valued remarkably high, it is too illogical to provide the crooks such a chance. Even worse if the spyware will in some way handle to steal your banking information. Seeing zeros on your financial account is the most awful headache, in my thoughts.
How did I get this virus?
It is hard to line the origins of malware on your computer. Nowadays, things are mixed up, and distribution methods utilized by adware 5 years ago can be utilized by spyware nowadays. However, if we abstract from the exact spreading way and will think of why it works, the answer will be very basic – low level of cybersecurity understanding. People click on advertisements on strange websites, click the pop-ups they get in their browsers, call the “Microsoft tech support” assuming that the odd banner that says about malware is true. It is essential to recognize what is legit – to stay away from misconceptions when trying to determine a virus.
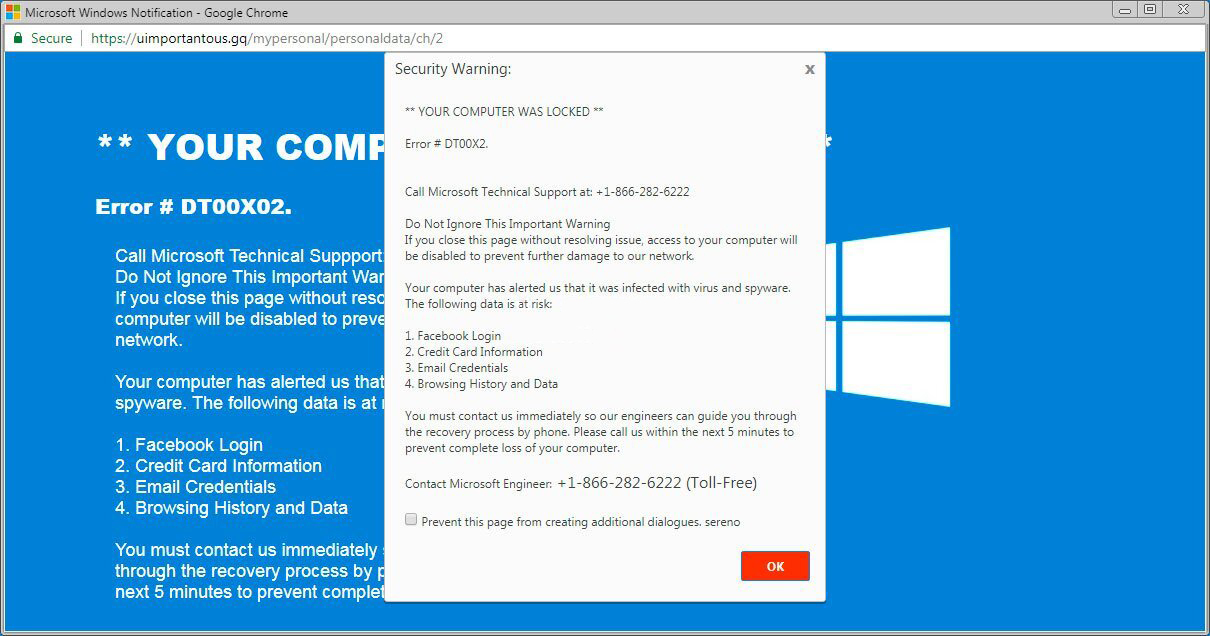
The example of Microsoft Tech support scam banner
Nowadays, there are two of the most extensive tactics of malware spreading – lure e-mails and injection into a hacked program. While the first one is not so easy to stay away from – you need to know a lot to understand a counterfeit – the 2nd one is very easy to address: just don’t use cracked programs. Torrent-trackers and other sources of “free” applications (which are, actually, paid, but with a disabled license checking) are just a giveaway place of malware. And Trojan:HTML/Phish.J!MTB is just amongst them.
Remove Phish with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Backdoors as shown from our tests with the software, and we assure you that it can remove Phish as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
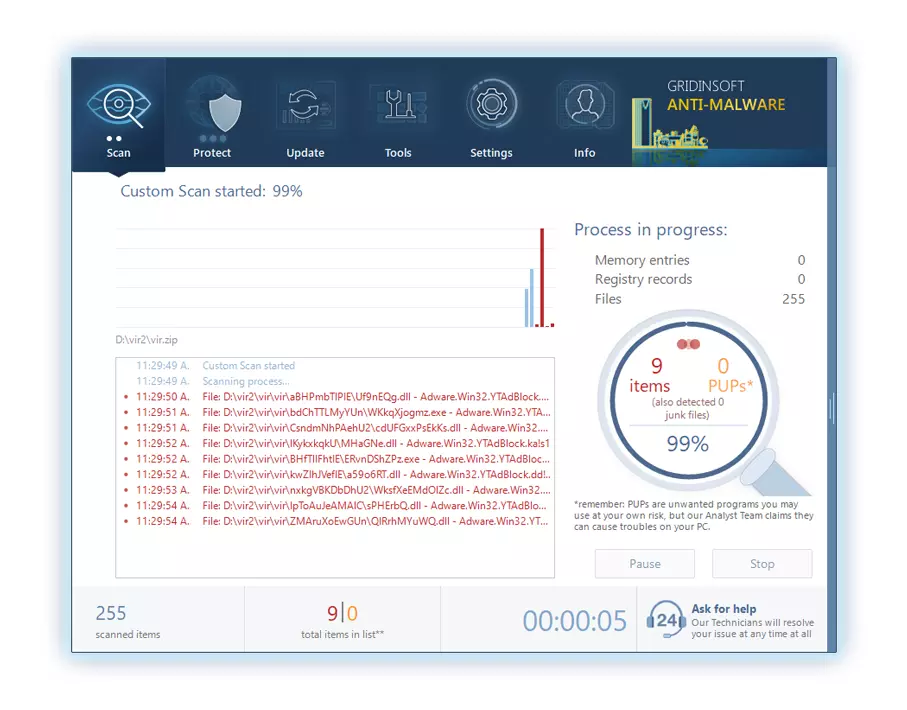
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
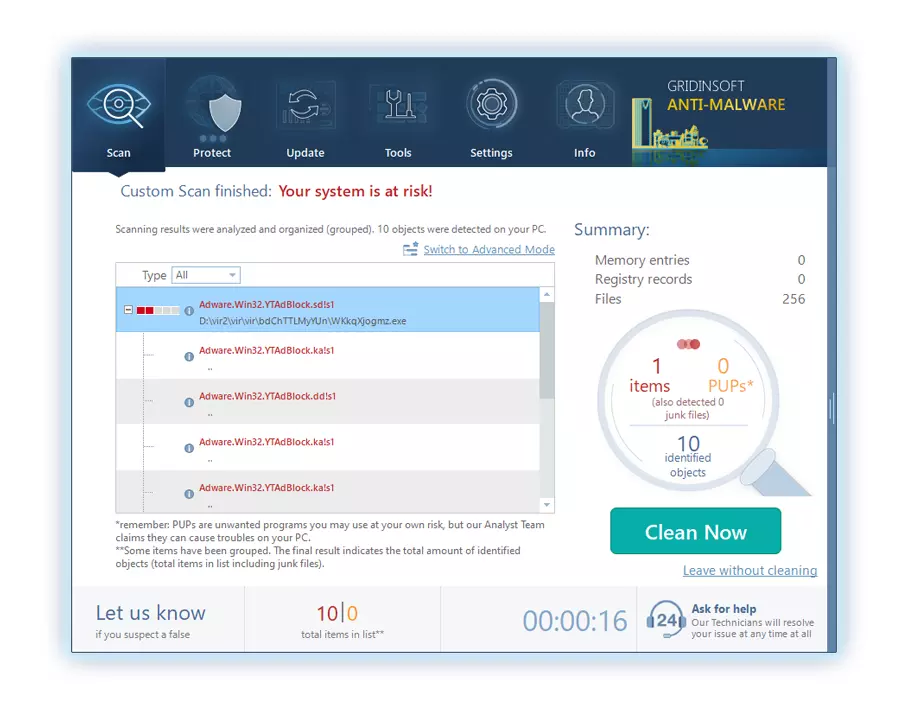
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
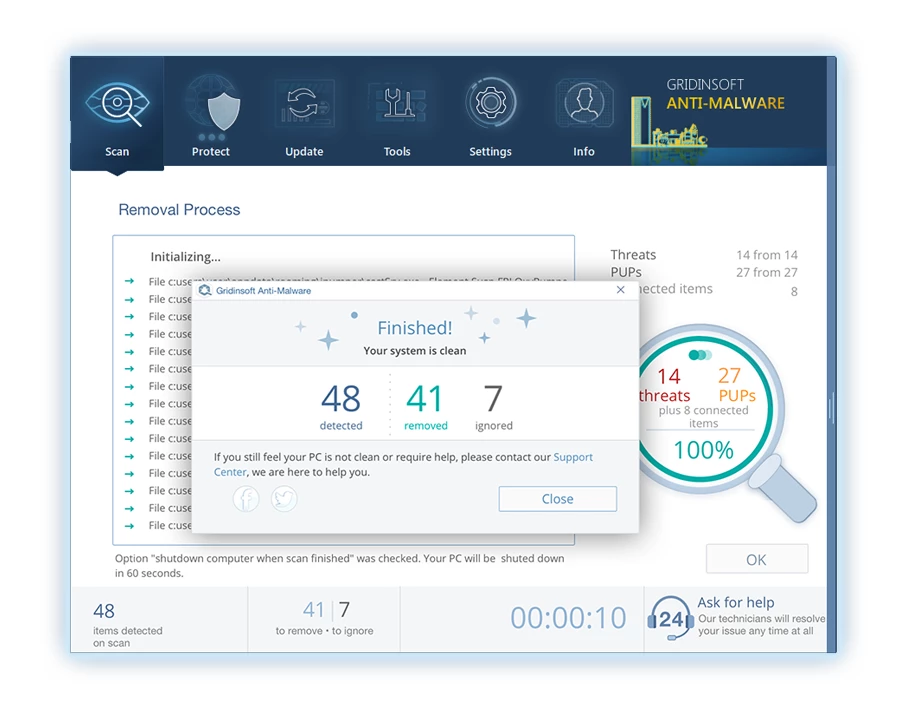
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “Phish” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
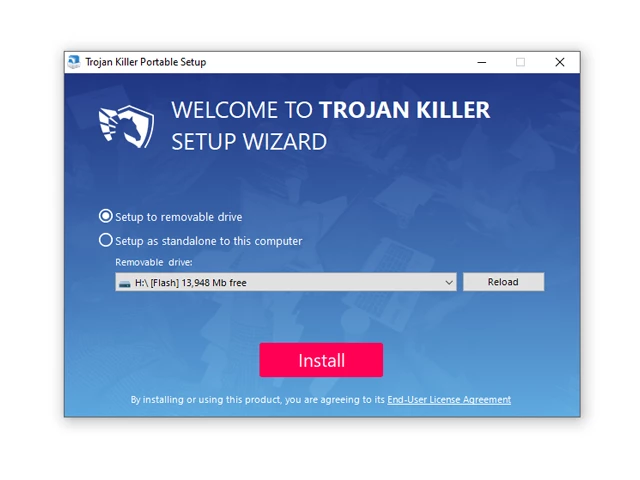
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
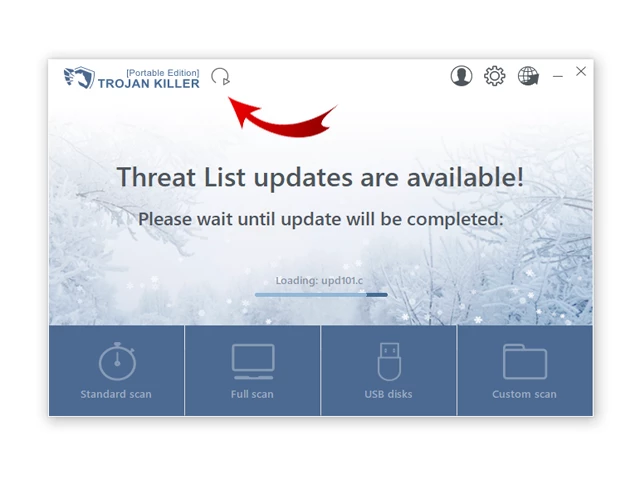
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
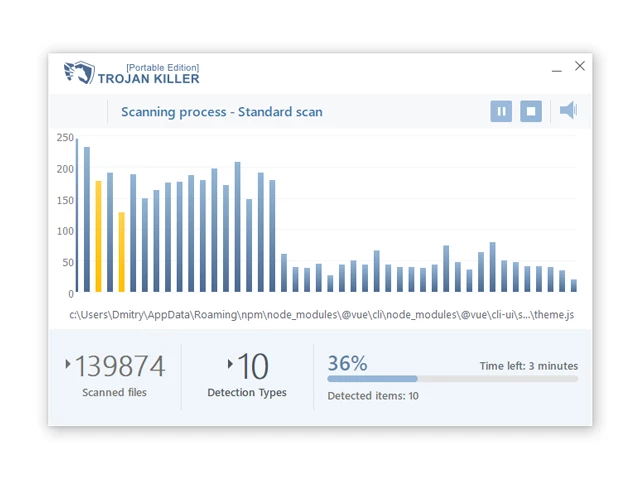
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
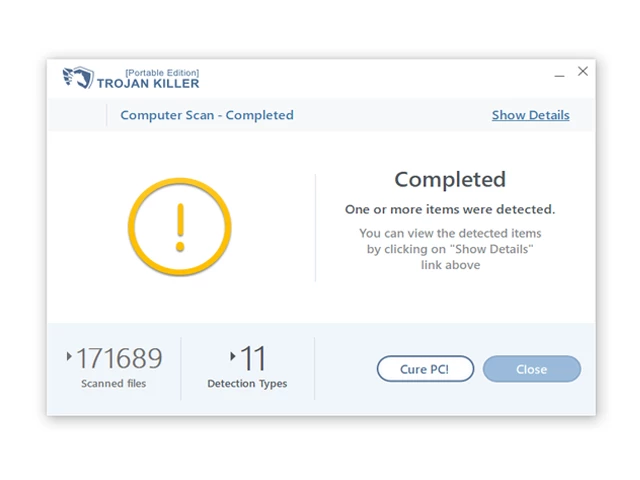
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
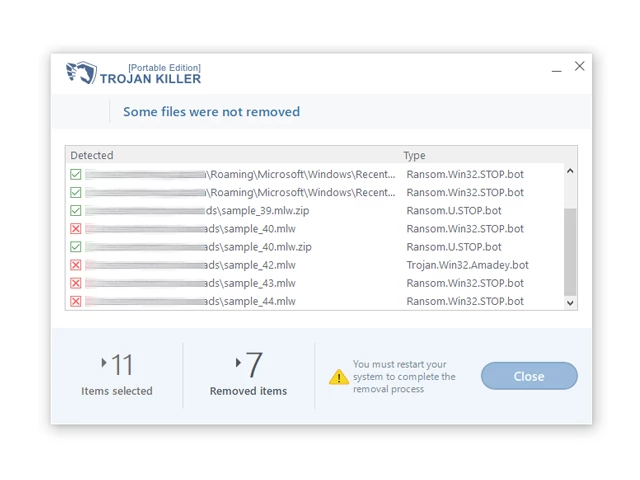
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing Phish and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions
There are many ways to tell if your Windows 10 computer has been infected. Some of the warning signs include:
- Computer is very slow.
- Applications take too long to start.
- Computer keeps crashing.
- Your friends receive spam messages from you on social media.
- You see a new extension that you did not install on your Chrome browser.
- Internet connection is slower than usual.
- Your computer fan starts up even when your computer is on idle.
- You are now seeing a lot of pop-up ads.
- You receive antivirus notifications.
Take note that the symptoms above could also arise from other technical reasons. However, just to be on the safe side, we suggest that you proactively check whether you do have malicious software on your computer. One way to do that is by running a malware scanner.
Most of the time, Microsoft Defender will neutralize threats before they ever become a problem. If this is the case, you can see past threat reports in the Windows Security app.
- Open Windows Settings. The easiest way is to click the start button and then the gear icon. Alternately, you can press the Windows key + i on your keyboard.
- Click on Update & Security
- From here, you can see if your PC has any updates available under the Windows Update tab. This is also where you will see definition updates for Windows Defender if they are available.
- Select Windows Security and then click the button at the top of the page labeled Open Windows Security.
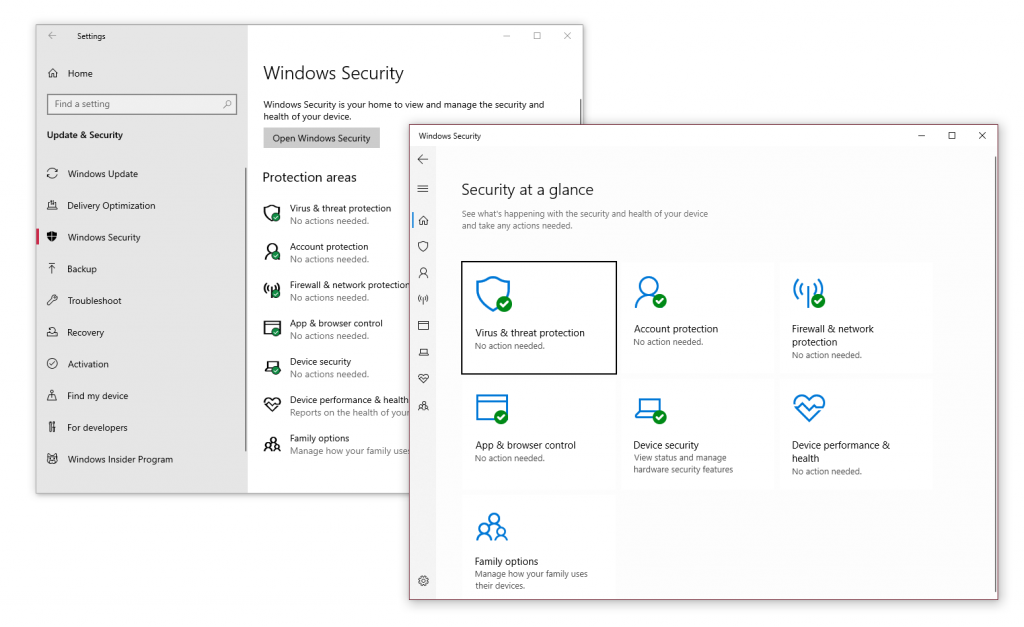
- Select Virus & threat protection.
- Select Scan options to get started.
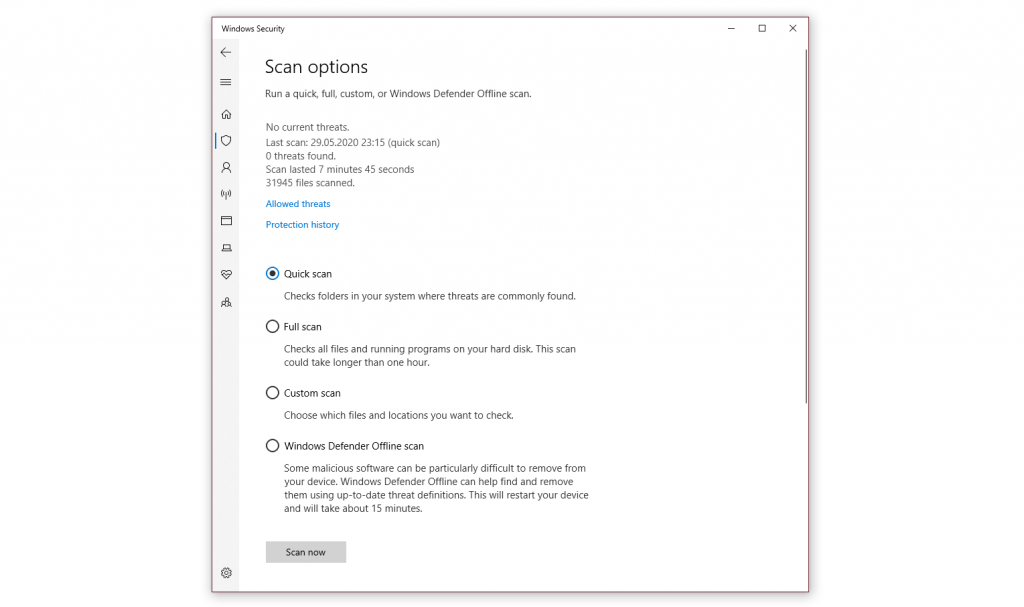
- Select the radio button (the small circle) next to Windows Defender Offline scan Keep in mind, this option will take around 15 minutes if not more and will require your PC to restart. Be sure to save any work before proceeding.
- Click Scan now
If you want to save some time or your start menu isn’t working correctly, you can use Windows key + R on your keyboard to open the Run dialog box and type “windowsdefender” and then pressing enter.
From the Virus & protection page, you can see some stats from recent scans, including the latest type of scan and if any threats were found. If there were threats, you can select the Protection history link to see recent activity.
If the guide doesn’t help you to remove Trojan:HTML/Phish.J!MTB virus, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help.
How to Remove Trojan:HTML/Phish.J!MTB Malware
Name: Trojan:HTML/Phish.J!MTB
Description: Trojan:HTML/Phish.J!MTB is a sneaky type of malware. It usually spreads through harmful email attachments or unsafe websites. Once it gets in, it lets cybercriminals control your computer, which is bad for your privacy. It can steal important stuff like personal and financial info. Plus, it might use your computer for harmful things like DDoS attacks.
Operating System: Windows
Application Category: Trojan
User Review
( votes)References
- Gossip about the backdoor in Intel processors on Reddit.