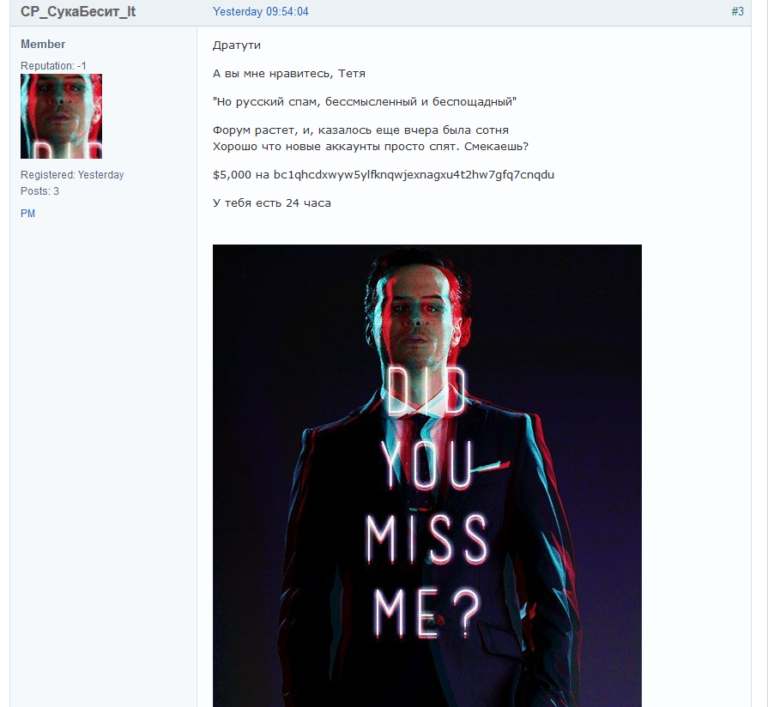
The Record journalists noticed that last weekend the forum of the Babuk ransomware operators was bombarded with the gay porn gifs and flooding and could not work normally.
The fact is that at the end of last week, an unknown extortionist demanded a ransom of $ 5,000 from the forum owners, but the Babuk operators just laughed and deleted the extortionate post.After that, hundreds of topics were created on the forum, and journalists noticed that the accounts they registered disappeared twice, that is, the owners of the resource were forced to wipe the entire forum at least twice, trying to fight the wave of spam that swept over them.
At the same time, the hackers flatly refused to pay the ransom, and the blackmailer’s Bitcoin wallet is still empty, while the announcement about its temporary closure and the development of a new engine is now posted on the forum.
The publication notes that this incident will negatively affect the reputation of Babuk.
Let me remind you that earlier this year, Babuk Locker operators announced that they would stop working (after an infamous attack on the Washington police department).
Journalists note that the hackers’ message has changed several times. So, in one of the versions, noticed by the analysts of Recorded Future, the criminals stated that hacking “PD was our last target”, referring to their latest victim – the Central Police Department of the District of Columbia.
In another version of the report, the police were not mentioned at all, and it was vaguely reported that the group intends to cease operations for the foreseeable future.
In this case, one part of the message always remains unchanged:
It is believed that the hackers renamed their “leak site” to Payload.bin, and were ready to provide it to other criminals as a third-party hosting, where someone’s files can be leaked without starting their own site for this purpose, as well as a platform on which ransomware, access brokers and other criminals will be able to “meet”. Indeed, recently, almost all major hack forums have banned any discussion related to ransomware and ransomware.
Journalists note that the attempt clearly failed, and the forum was unable to gain popularity, but was subjected to DDoS attacks, suffered from various bugs, and the current incident is likely to put a final cross on it.