Scientists from universities in China, Singapore and Switzerland talked about a new SmashEx attack that helps to compromise Intel SGX enclaves and steal sensitive data from the most secure area of the Intel processor.
Let me remind you that with the release of the Skylake architecture, Intel introduced a technology called SGX (Software Guard Extensions). SGX is a set of CPU instructions through which applications can create protected zones (enclaves) in the application’s address space, inside which, under reliable protection, various confidential data can be stored. SGX enclaves are usually isolated at the hardware level (SGX memory is separated from the rest of the CPU memory) and at the software level (SGX data is encrypted). The developers themselves describe this technology as a kind of “inverse sandbox”.The SmashEx attack allows malware running on the same OS to abuse a feature that allows the CPU to suspend SGX operations to enter the enclave and retrieve data. Here’s how the researchers describe it themselves:
SmashEx is an attack that uses enclave SDKs that do not handle re-entrancy in their exclusive security, which is difficult for SGX. Proof-of-concept SmashEx exploits allow code reuse (for example, ROP) and achieve disclosure of confidential data in enclaves built using vulnerable runtime.
Experts conducted tests successfully to extract the RSA encryption key from the Intel SGX enclave used by the server to encrypt HTTPS traffic. They were also able to extract content processed by the Microsoft Open Enclave cURL application used by Azure servers.

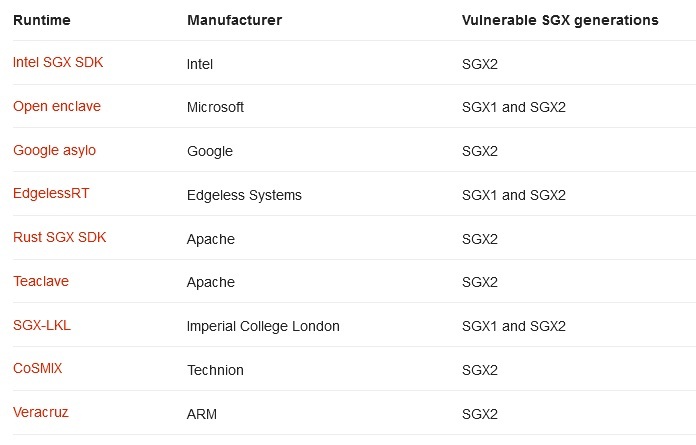
The details of the SmashEx attack were released just this week after Intel and Microsoft released fixes to address this issue in their SDKs, namely the Intel SGX SDK (CVE-2021-0186) and the Open Enclave SDK (CVE-2021-33767). At the same time, the research group states that there are many other SDKs for which the SmashEx attack is also dangerous, and their developers must now also release their own patches. This applies to SGX SDKs from Google, Apache and Arm.
Let me remind you that we also talked about the fact that Pay2Key ransomware attacked Intel-owned Habana Labs company.

