ETH Zurich researchers have published a report describing numerous security issues and serious vulnerabilities in Threema, a secure Swiss messenger with end-to-end encryption.
The creators of Threema claim that the shortcomings discovered by the experts never affected the actual operation of the application.Let me remind you that we also wrote that WhatsApp Messenger Developers Eliminated Two RCE Vulnerabilities at Once, and also that Bug in Facebook Messenger for Android allowed connecting to user conversations.
The media also wrote that Vulnerability in Signal messenger allows spying on users.
Threema is a Swiss-based privacy and security-focused communications application used by the government, the military, and more than 10 million users and 7,000 organizations worldwide. The messenger is positioned as an alternative to Signal and WhatsApp.
In their work, ETH Zurich scientists describe seven attacks on the Threema protocol at once, including theft of private keys, deletion of messages, authentication hacking, server spoofing, and much more. A summary of the issues found is as follows:
- Masquerading as another user through ephemeral key compromise. An attacker can impersonate a client on a server using its ephemeral key. Worse, instead of using ephemeral keys once, Threema seems to have reused them.
- Fake voucher box. An attacker can trick users by sending them a valid vouch box and then use it by impersonating clients on the server.
- Reorder and delete messages. A malicious server can randomly forward messages from one user to another or refuse to deliver certain messages, which is tantamount to deletion.
- Replay and reflection attacks. In the Android version of Threema nonce, the message database is not transferable, which opens up the possibility of replay and reflection attacks on messages.
- Kompromat attack. A malicious server can trick a client into using the same key when communicating with the server during initial registration and when communicating with other users over the E2E protocol.
- Cloning using Threema ID export. The attacker can clone other people’s accounts on their device if the victim left their device unlocked and unattended.
- Side-channel compression. A vulnerability in Threema encryption allows attackers to extract a user’s private key by controlling the victim’s username and forcing multiple backups on Android devices. The implementation of the attack can take several hours.
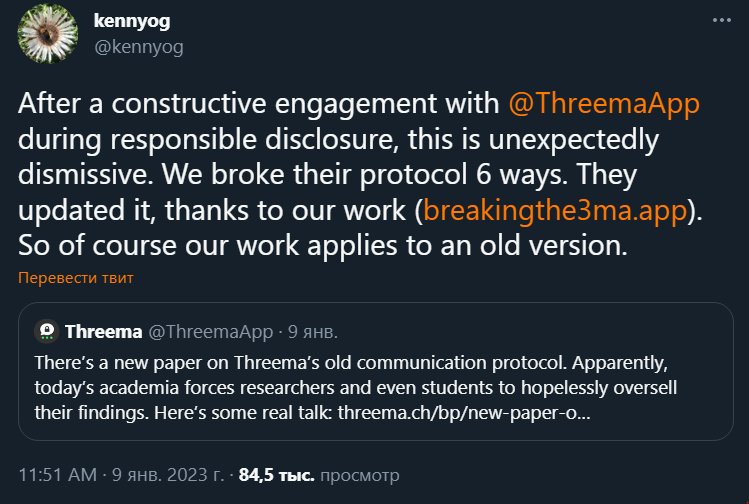
ETH Zurich analysts reported all discovered issues to Threema developers back in October 2022, provided them with recommendations for mitigating the problems, and also agreed not to make the vulnerabilities public until January 2023.
As a result, on November 29, 2022, the developers of the messenger transferred Threema to the new and more secure Ibex communication protocol. When the ETH Zurich researchers released the results of their research, the developers released a response statement in which they said that the problems found were generally insignificant and never had an actual impact on Threema. In addition, the vulnerable protocol studied by the researchers is no longer used anyway, so the vulnerabilities are called interesting only from a theoretical point of view.
In addition, the company refutes claims that the Ibex protocol was created taking into account and based on the findings of researchers from the Swiss Federal Institute of Technology Zurich, stating that the protocol has been in development for more than 1.5 years. Allegedly, the release of Ibex simply coincided with the disclosure of information about vulnerabilities.
The researchers didn’t like this snub of their work, and they retort on Twitter that the new protocol is certainly more secure, because they managed to crack the old one in six different ways, and this was taken into account when creating Ibex.