What is Ransomware Attacks?
Ransomware is a type of malware designed to encrypt files and demand payment in exchange for the decryption key. In other words, ransomware attacs as digital extortion by cybercriminals against individuals, businesses, and organizations alike.
Ransomware typically infects a victim’s computer or network through various methods, such as phishing emails, malicious websites and software vulnerabilities. Once on board, the ransomware will encrypt all files on that machine or network – making them unaccessible to the victim.
Once encrypting files, ransomware will display a message demanding payment in exchange for a decryption key. In some cases, the message may even threaten to delete encrypted data if not paid within an agreed upon timeline.
Ransomware attacks can be devastating for victims, resulting in the loss of important data and files as well as financial losses due to ransom demands. To protect against ransomware attacks, individuals and organizations need to take proactive measures such as keeping software up-to-date, using anti-malware software, and practicing good cybersecurity hygiene.
In the meantime, according to the United States Computer Emergency Readiness Team (US-CERT), between June and October 2022, thousands of organizations were hit with ransomware. In another survey, Gartner Inc says the number of ransomware attacks will explode in 2024.
And it was true – 2022 has been a wake-up call for all organizations and companies which have experienced ransomware attacks. This year, companies have seen various attacks including the Dharma ransomware attack, which in particular, wreaked havoc across 150 countries. Another major ransomware attack that dominated headlines was the STOP/Djvu ransomware attack. The attack most affected individuals in India and Asia.
The incidence of ransomware attacks went up.
It is expected that the rise of ransomware is due to the online anonymity factor of the dark web as ransomware is mostly a crime involving huge amounts of money.
Ransomware attacks have seen a meteoric rise in recent years and it appears likely they will remain an ongoing risk into the foreseeable future.
Ransomware attacks have grown more sophisticated and targeted, with attackers employing various methods to infiltrate computer systems and networks, such as phishing emails, software vulnerabilities, and brute-force attacks. Furthermore, ransomware attacks have become more profitable for cybercriminals by increasingly targeting high-value targets like businesses, governments, and healthcare organizations.

Another major reason for ransomware is the prevalence of common loopholes in many programming languages, which attackers can take advantage of to build ransomware and send it to the targets while targeting the Windows operating system.
What is Ransomware Attacks and how does it work?
A ransomware attack works like this: The attacker sends a malicious link to a victim that, when clicked, allows the hacker to infect the victim’s computer. The ransomware then encrypts all the files on the victim’s hard drive and asks for a ransom to be paid. The ransom is paid in Bitcoin or Monero.
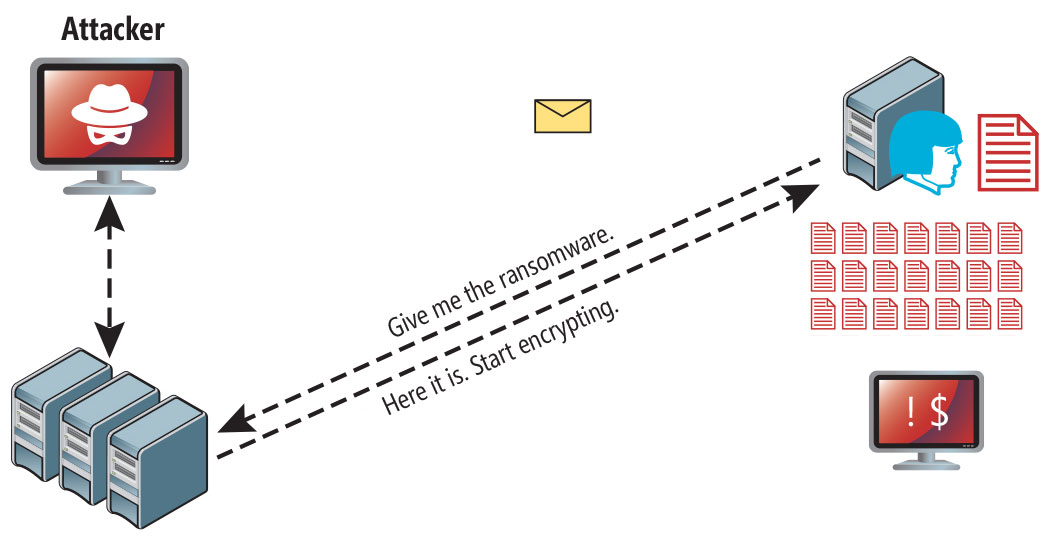
Ransowmare attack following a successful phishing attempt.
If you are targeted with a ransomware attack, you will need to take preventive steps to avoid infection.
Report the infection immediately to the IT department and ensure that the user has no suspicious files, such as pirated games or office software, on the computer.
The IT department will need to perform a complete forensic investigation on the device that was infected with ransomware and take appropriate steps to remove it.
Infection caused by applications such as Office macros can be avoided by ensuring that no software is running on the system that is not intended to run on the system.
Steps to help prevent & limit the impact of Ransomware:
- Don’t download apps from suspicious sites.
- Back up important files on a regular basis and remember to make regular backups.
- Watch out for spam messages and emails that claim to be from Microsoft and warn you of important problems or viruses.
- Restrict access to your apps by creating a separate password for each app.
- Do not allow the apps to access your phone’s or computer’s location services.
- Ensure that you have security software and antivirus apps installed.
- Create different passwords for every app.
A large number of apps are fraudulently posted on the App Store, Google Play Store and other stores. A few good examples are Google Docs or Gmail, which may not really be legitimate. These apps try to get your personal information or infect your device with malware to steal data from your device.
NO! It is safest not to download apps from suspicious sites. Also, make sure that the page where you are downloading the app is safe and has no malware inside. When in doubt, don’t trust what you see.
You can try to find a copy of an original file that was encrypted:
- Files you downloaded from the Internet that were encrypted and you can download again to get the original.
- Pictures that you shared with family and friends that they can just send back to you.
- Photos that you uploaded on social media or cloud services like Carbonite, OneDrive, iDrive, Google Drive, etc)
- Attachments in emails you sent or received and saved.
- Files on an older computer, flash drive, external drive, camera memory card, or iPhone where you transferred data to the infected computer.
Also, you can contact the following government fraud and scam sites to report this attack:
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In India, go to Indian National Cybercrime Reporting Portal.
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Poland: KOMENDA GŁÓWNA POLICJI;
- In Portugal: Polícia Judiciária;
- In Italy: Polizia di Stato;
- In Spain: Cuerpo Nacional de Policía;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
To report the attack, you can contact local executive boards (A full list you can find here). For instance, if you live in USA, you can have a talk with FBI Local field office, IC3 or Secret Service.
Ransomware removal
If your computer has been infected with ransomware, you’ll need to regain control of your machine. Here has a great video demonstrating how to do this on a Windows PC:
The video has all the details, but the important steps are to:


