The team of exerts has published a description of a theoretical Raccoon attack on TLS that can be used for decrypting HTTPS connections and reading traffic.
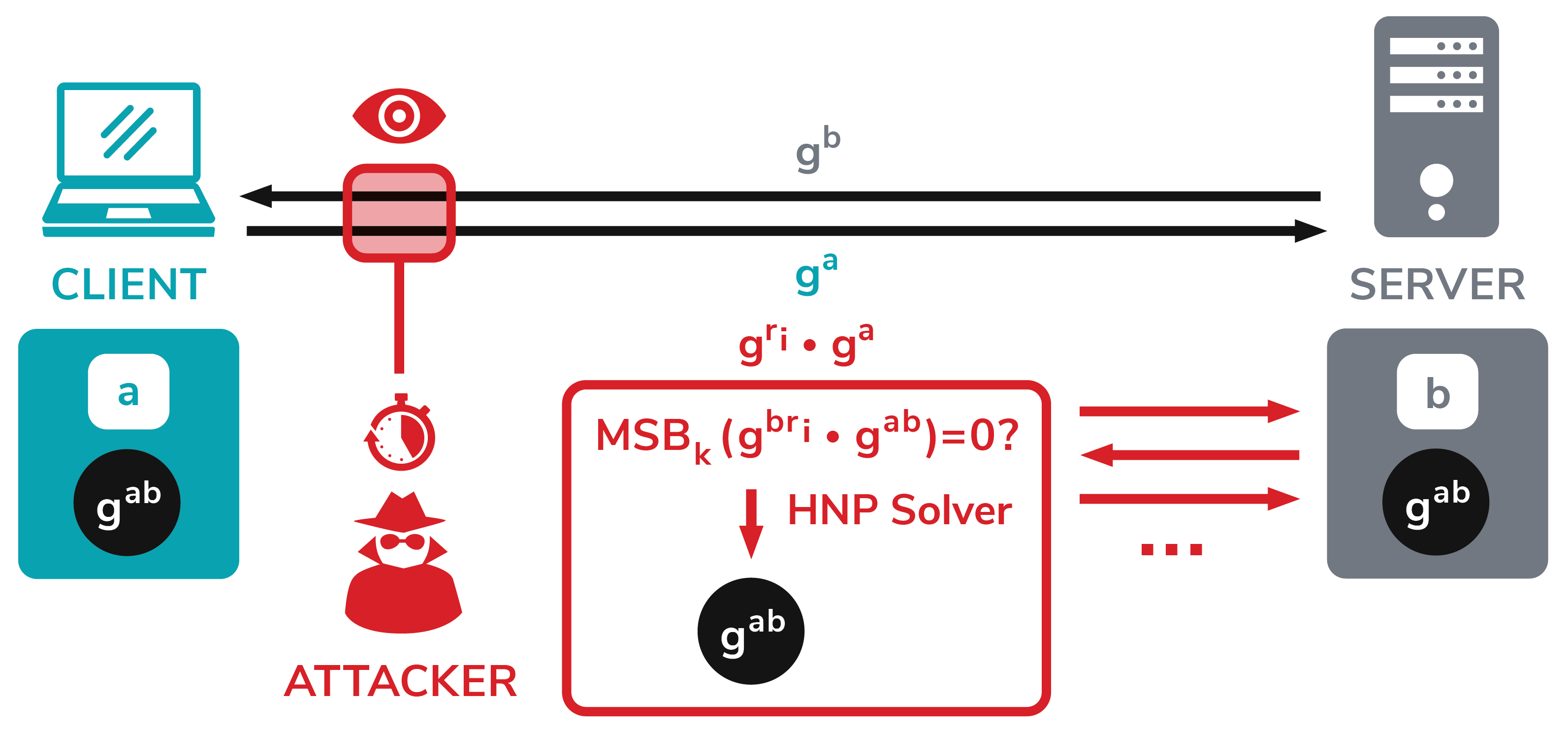
However, the researchers admit that the Raccoon attack is theoretical and extremely difficult to execute.Raccoon is a classic timing attack, it is a side-channel attack in which a criminal tries to compromise a system by analyzing the time it takes to execute certain cryptographic algorithms. In the case of Raccoon, the attacker observes key exchange and Diffie-Hellman protocol in order to recover several bytes of information.
This helps an attacker create a system of equations and then use a Hidden Number Problem (HNP) solver to compute the pre-master secret between the client and server”, — the researchers say.
All servers using the Diffie-Hellman protocol for key exchange and TLS connections (TLS 1.2 and below) are vulnerable to this problem. The vulnerability also affects DTLS. Only TLS 1.3 was considered safe by experts.
Diffie-Hellman (DH) key exchange is a well-established method for exchanging keys in TLS connections. When using Diffie-Hellman method, both TLS peers generate private keys at random (a and b) and compute their public keys: ga mod p and gb mod p. These public keys are sent in the TLS KeyExchange messages. Once both keys are received, both the client and server can compute a shared key gab mod p – called premaster secret – which is used to derive all TLS session keys with a specific key derivation function.
The Raccoon attack has to be done on the server side and cannot be done from the client side, for example through browsers. In addition, the attack must be performed on every single client-server connection and cannot be used to recover the server’s private key and decrypt all connections at the same time”, – say the researchers.
As mentioned above, the Raccoon attack is extremely difficult to implement in practice. Researchers believe that real hackers would rather use other, simpler and more effective attack vectors than Raccoon.
Although the authors call their attack theoretical, some vendors have nevertheless released patches to protect against Raccoon, including Microsoft (CVE-2020-1596), Mozilla, OpenSSL (CVE-2020-1968) and F5 Networks (CVE-2020-5929).
Note:
Don’t confuse Raccoon attack with Raccoon malware (aka Legion, Mohazo, and Racealer), that steals data from 60 different applications, including popular browsers, email clients, and cryptocurrency wallets.