Ransomware1 in its modern shape was first detected in 2014, and since then cybercriminals have produced hundreds or even thousands of different ransomware variants. Some ransomware groups are currently shut down, and some are still going, having dozens of unsupported variants. However, ransomware is always ransomware – it will encrypt your files and ask for a ransom payment even though it was released 3 years ago, and no one will check that contact email.
Obsolete ransomware: explaining the danger
Ransomware is distributed in different ways. Primarily, those aimed at corporations do not have the exact file source – it is injected during the attack by crooks. But those aimed at individual users are usually spread through malicious email spam or as a part of an untrustworthy program. Hence, it is straightforward to find such a program or email message on the Web and click on it. The sleeping ransomware will be glad to wake up and do its filthy job, ciphering everything you have on your PC. Sure, it will not be able to connect to its servers, but no one prohibits the ransomware from using an offline key – that will be as hard as the online one.
ransomware have encrypted the user’s files
And the problem is not only in the fact that there are a lot of outdated and uncontrolled ransomware variants, which can cipher your files without any chances for getting back. Even after being encrypted with the newest ransomware variant, you may wait for the decryption tool to be released or even pay the ransom. But for the obsolete malware variants, you will likely turn old than get a free decryption tool or the answer on your email about the decryption after the ransom payment.
Analyzing the ransomware statistics
It is important to know how much ransomware and of which type is circulating nowadays. Since its appearance in 2014, ransomware was experiencing only local downtrends, having, in fact, a stable uptrend for new variants appearing. The last significant decrease in ransomware activity took place at the beginning of 2021, when a large distribution group was caught by cyber police. However, capturing the distributors is not equal to capturing the ransomware producers and vaporizing all existing ransomware variants. All malicious items produced earlier are still dangerous and can be found on the Internet, in this or that form.
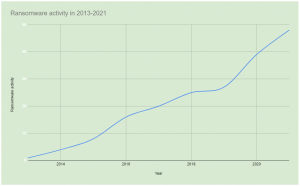
Old statistic: not so much, but still a lot
During the first 4 years of ransomware activity, cybersecurity analysts detected about 560 different ransomware variants. Those variants belong to different families, and most of them are currently not operating. Hence, if you somehow got one of these things on your PC – no one can help you. Even the early versions of ransomware used pretty tough decryption algorithms – AES-256 or RSA-1028, which are impossible to decrypt with brute force. And in those times, after the shutdown, ransomware groups did not have a habit of publishing the decryption keys. If you are getting infected, you can say “bye” to your files.
Through the last 3 years, the ransomware market became even more active. Sure, the accent was moved to corporate attacks since it is much more profitable per single attack. The biggest ransom was extorted from Acer corporation in March 2021 – the company was forced to pay $50 million. That is likely an exclusion – the majority of corporation-oriented malware groups ask for $50,000 – $1 million, depending on the size of the attacked company. To compare, the common ransom for the file decryption for the individuals is $500 – $3000.
Situation in 2019-2021
During the pandemic, crooks became extremely active. Ransomware activity surged, both companies and individuals suffered an extreme amount of attacks. Aforementioned types of ransomware by their targets got their unchanging leaders – Conti group for companies (about 28% of all submissions) and STOP/Djvu for individual users (almost 75% of all cases). While from 2014 to 2018, analysts said about one new ransomware variant each day, nowadays they can see 2-4 variants every new day. STOP/Djvu family alone publishes the new variant of its “product” each 3-4 days, even on the weekends.
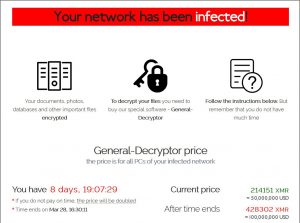
Ransom note for Acer corporation
There is no strict statistic about the total number of new ransomware variants in the 2019-2021 period. But we can try to calculate it: let’s take the number of new variants as 1.5 per day (taking into account that ransomware activity is not stable and was generally lower in 2019). Multiplying it on the 974 days (counting from January 1, 2019) and getting 1461 ransomware variants. Of course, this number is inaccurate and must be corrected, but cybersecurity analysts are now concentrating on preventing ransomware cases rather than statistics. In 2014-2018, when the computer world was horrified with this malware type, the only thing that analysts could do was collect as much information as they could to understand how crooks act and where the security breaches are. But now, it is their time to act.
But let’s finish our calculations. 1461 variants have appeared just in the last three years, and we also have ~560 variants of more old ransomware. In total, about two thousands of different ransomware variants are currently present, and you never know if one hides in the program, you are trying to download.
Things are not so bad
2000 ransomware variants is a scary number, but it is important to understand that number properly. The older the ransomware, the less the chance that you can find it wherever. Even on the torrent trackers, like ThePirateBay or Rarbg, moderators check the seedings that are reported for malicious contents and remove them if those reports are true. Other websites used to distribute ransomware are getting banned by anti-malware software and getting shut down if their maintainers are captured. For the majority of obsolete versions of currently active ransomware groups (STOP/Djvu or Xorist, for example), there are the decryption tools available for free.
It is better to concentrate on more actual ransomware hazards, that use much more tricky ways to be injected into your system. Email spam2 that mimics the messages from your bank, offers in the Discord groups to test “the new program” – all these methods are used not just because crooks have a good imagination. Users became smarter and smarter and cannot be tricked with the same hints as in 2018. Hence, to be safe from a sudden loss of all of your files, it is almost obligatory to be careful while browsing the untrusted sites and to have a good anti-malware solution on your PC.
Consider reading: How to disable or remove browser extensions?.
User Review
( votes)References
- Ransomware: https://gridinsoft.com/ransomware
- Email spam: https://en.wikipedia.org/wiki/Email_spam



