NVIDIA has released a security update for a wide range of graphics card models that resolves four critical and six moderate vulnerabilities in its GPU drivers.
The update fixes security issues in earlier versions of drivers that could lead to “denial of service, information disclosure, or data tampering.”
Recall that we have already reported that Nvidia specialists have fixed a number of serious vulnerabilities in GeForce Experience, and also that Nvidia halves mining performance of RTX 3080, 3070 and 3060 Ti.
Nvidia has also released a security update for Kepler series GPUs that are no longer supported by the manufacturer. The company has stopped servicing most GTX 600 and GTX 700 Kepler series products in 2021. The first Kepler-based graphics cards were released by Nvidia in 2012. Legacy models can still be used, but Nvidia will no longer release Game Ready drivers for unsupported products.
The security bulletin lists a total of ten vulnerabilities in Nvidia’s GPU display drivers. Most of these are kernel-mode vulnerabilities on Windows and Linux devices, while some address security issues in the Windows DirectX11 user-mode driver or ECC-level vulnerabilities.
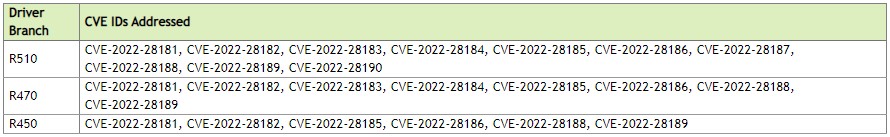
Updates are available for Tesla, RTX/Quadro, NVS, Studio, and GeForce software products, covering the R450, R470, and R510 driver branches.
Fixed CVE for each driver branch (NVIDIA)
Four dangerous vulnerabilities were fixed this month:
- CVE-2022-28181 (CVSS v3 score: 8.5) – this vulnerability allows out of bounds writing of a kernel mode level caused by a specially crafted shader sent over the network, which may result in code execution, denial of service, privilege escalation, information disclosure and falsification of data.
- CVE-2022-28182 (CVSS v3 score: 8.5) is a bug in the DirectX11 user-mode driver that allows an unauthorized attacker to send a specially crafted share over the network and cause denial of service, privilege escalation, information disclosure, and data falsification.
- CVE-2022-28183 (CVSS v3 score: 7.7) is a kernel mode vulnerability when an unprivileged user could cause an out-of-bounds read that could lead to a denial of service and information disclosure.
- CVE-2022-28184 (CVSS v3 score: 7.1) – is a vulnerability in kernel mode level handler (nvlddmkm.sys) for DxgkDdiEscape where an unprivileged user can access registers with administrator privileges, which could lead to a denial of service, disclosure information and falsification of data.
The vulnerabilities found require low privileges and no user interaction, so they can be embedded in malware, allowing attackers to execute commands with higher privileges.
The first two can be used over the network, while the rest can be accessed locally, which can be exploited by malware that infects a system with low privileges.
Cisco Talos, which discovered CVE-2022-28181 and CVE-2022-28182, also released a post today detailing how they caused memory corruption vulnerabilities by providing a malformed compute shader.
Since attackers can use a malicious shader in the browser using WebAssembly and WebGL, Talos warns that attackers can remotely exploit the discovered vulnerability.
For more information on all fixes and each software and hardware product reviewed this month, please see the NVIDIA Security Bulletin.
All users are encouraged to apply the released security updates as soon as possible. Users can download the latest driver for their GPU model from NVIDIA’s central download section, where they can select the specific product and the OS they are using.
Updates can also be applied through the NVIDIA GeForce Experience package.
However, unless you need special software to save game profiles or use streaming features, we recommend that you do not use NVIDIA GeForce Experience, as the program introduces unnecessary security risks and wastes resources.

