Trend Micro analysts have prepared a detailed report on the Void Balaur hacker group. These cyber mercenaries have been hacking companies and individuals for over five years, stealing mails and confidential information, and selling data to their clients for both financial gain and spyware.
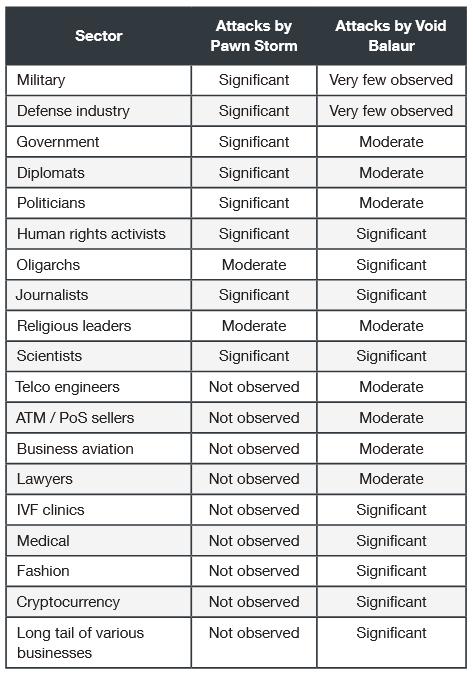
According to researchers, since the mid-2010s, the group has attacked 3,500 targets around the world, including IT companies, telecommunications companies, activists, journalists and religious leaders. At the same time, unlike other mercenary hackers, Void Balaur simply advertises its services on Russian-language hacker forums, but not at specialized exhibitions and conferences, as their “colleagues” do.Initially, Trend Micro experts considered Void Balaur to be a subgroup of APT28 (aka Fancy Bear, Sednit, Sofacy, Strontium and PawnStorm), which IS specialists have long associated with the GRU and Russian special services.
However, upon closer examination of the facts, the researchers concluded these cybercriminals may not be linked to APT28.
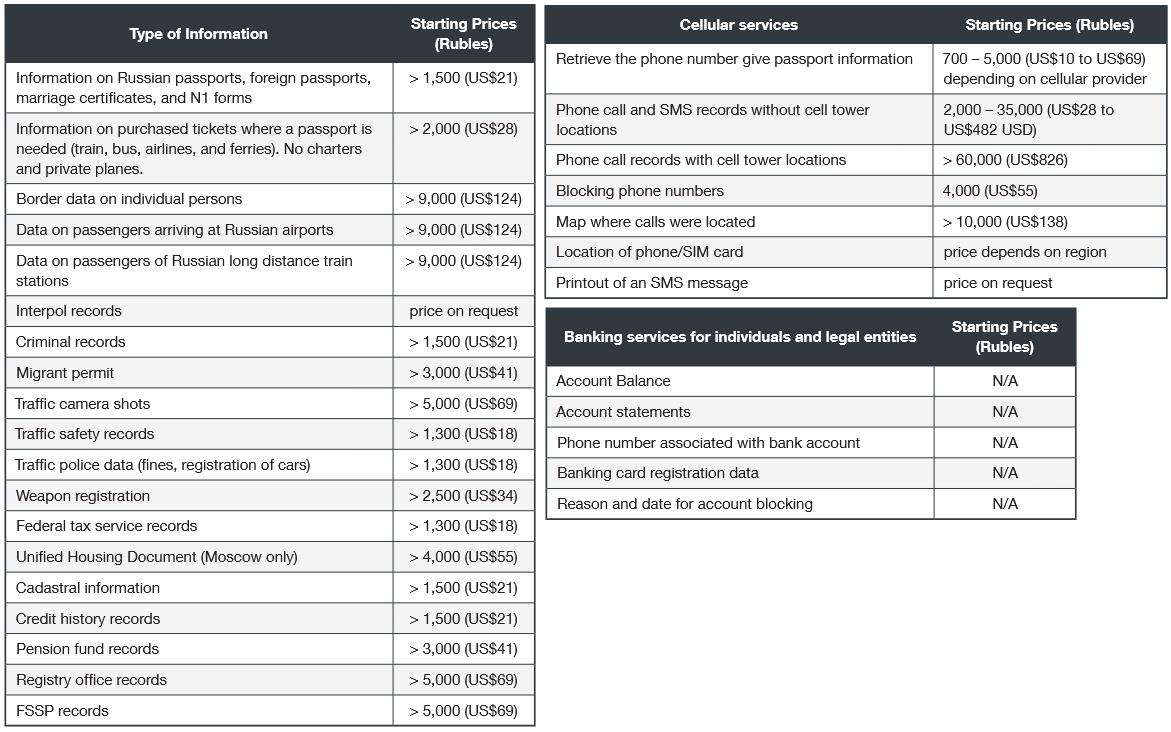
The fact that in 2019 the group began to advertise the sale of personal and confidential data of Russia, including data on passports, driver’s licenses, personal telephone conversations, pictures from road cameras, information on the registration of weapons, criminal convictions, credit history, tax service data and much more, forced to change the conclusions about the connection between Void Balaur and APT28 experts. Researchers do not know how the hackers gained access to so much confidential data, but they speculate that all of this could have been used to cover up more serious crimes.
As mentioned above, experts have identified more than 3,500 targets that the group has attacked over the past few years. Many of these attacks targeted telecommunications companies in Russia and the United States, but the group also targeted individuals, including activists and journalists. For example, Trend Micro states that attacks on journalists and human rights defenders in Uzbekistan in 2016 and 2017, described in the eQualitie report, were result of Void Balaur operation.
The group was also engaged in other political goals. So, in 2020, hackers attacked presidential candidates in Belarus. In August 2021, the group also targeted politicians and government officials from Ukraine, Slovakia, Russia, Kazakhstan, Armenia, Norway, France, and Italy.
It is reported that most recently, in September 2021, the group also tried to access the mailboxes of “the former head of the intelligence agency, five current ministers (including the Minister of Défense) and two members of the national parliament of the Eastern European country.”
But, in addition to politicians, private companies also became targets of Void Balaur. For example, an expert report states that the group targeted members of the board of directors, executives and heads of one of the largest corporations in Russia (the name was not disclosed).
Among other targets of Void Balaur were companies that have access to vast amounts of sensitive data. According to the researchers, the hackers were primarily interested in the opportunity to sell this data on underground forums.
It is also noted that since 2018, Void Balaur has operated several phishing sites that appear to target cryptocurrency users. It is unclear if these sites were created on the group’s own initiative or one of the group’s clients needed them.
Based on information gathered by Trend Micro, Void Balaur sells personal data to anyone willing to pay. These mercenaries simply don’t care what their clients do with the information they acquire.
Let me remind you that we also talked about the fact that Russian hackers tried to steal COVID-19 research data.

