This summer, Bleeping Computer journalists reported about the new AgeLocker ransomware, which uses the Age (Actually Good Encryption) algorithm to encrypt the files of its victims. Now it turned out that AgeLocker attacks Qnap devices.
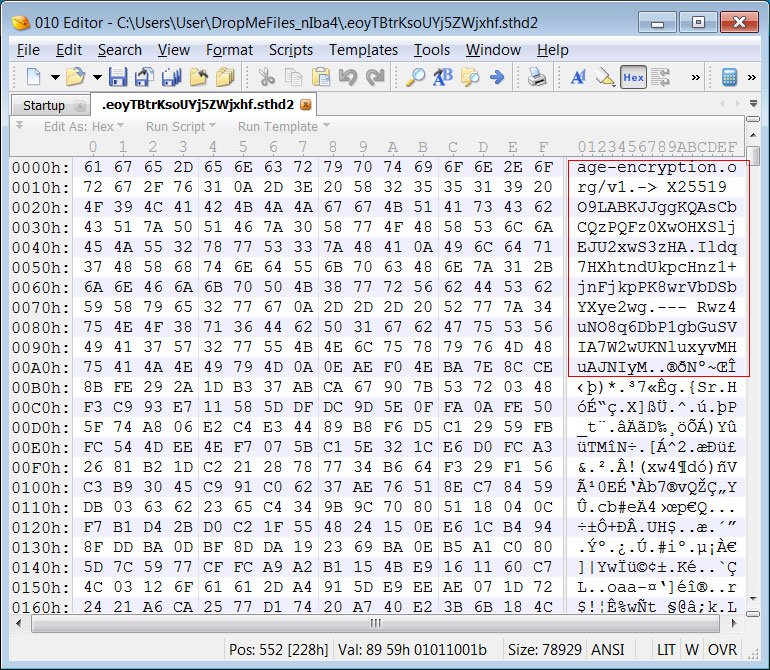
When encrypting, the malware adds a text header to the encrypted data, which begins with the age-encryption[.]org URL as shown in the figure below:The URL age-encryption.org brings user to a GitHub repository for an encryption utility called ‘Age’ created by Filippo Valsorda, cryptographer, and Go security lead at Google.
And this encryption is considered to be pretty strong – which is pretty bad news for AgeLocker victims.
Now the publication’s specialists have noticed that since the end of August 2020, AgeLocker or another ransomware using the same encryption has begun to attack Qnap NAS devices accessible via the Internet and encrypt data on them.
Thus, one of the victims from the Bleeping Computer forums shared the encrypted file with the analysts of the ID Ransomware project, after which information security expert Michael Gillespie was able to determine that the file was encrypted using Age. Gillespie also confirmed that AgeLocker was indeed active by the end of August.
The specialist also notes that in a ransom note, AgeLocker operators state that before encryption began, they stole user’s files, which contain “medical data, scanned images, backups, and so on.”
It is not yet known how much the hackers are demanding as a ransom or exactly how the attackers gain access to QNAP devices.
The publication also warns that, unfortunately, it is impossible to recover files encrypted by AgeLocker for free.
This is perhaps the most interesting case after the massive attacks on QNAP NAS by the QSnatch malware.
To enhance device security, QNAP invites all owners to complete the following checklist:
- Change all passwords for all accounts on the device
- Remove unknown user accounts from the device
- Make sure the device firmware is up-to-date, and all of the applications are also updated
- Remove unknown or unused applications from the device
- Install QNAP MalwareRemover application via the App Center functionality
- Set an access control list for the device (Control panel -> Security -> Security level).