FireEye analysts warn that from December 2020 to January 2021, there were massive hacks on Accellion clients. About 100 companies and organizations around the world were attacked through the file-sharing service Accellion FTA (File Transfer Application). Experts attribute this activity to the FIN11 hacker group.
According to the report, for attacks, hackers used four vulnerabilities in FTA (CVE-2021-27101, CVE-2021-27102, CVE-2021-27103 CVE-2021-27104), installed the DEWMODE web shell, and then used it to steal files, stored on victims’ FTA devices.The problem is that Accellion FTA is a legacy service that is deployed locally to exchange large files that cannot be sent by email. In the early 2000s, when FTA appeared, Dropbox, Google Drive and other similar solutions were not yet available.
As a result, the developers of Accellion released several “waves” of fixes, but each time they emphasized that FTA has long been an outdated product, and urged their customers to migrate to the new Kiteworks platform. This month, the company announced that it would finally stop supporting the FTA on April 30, 2021.
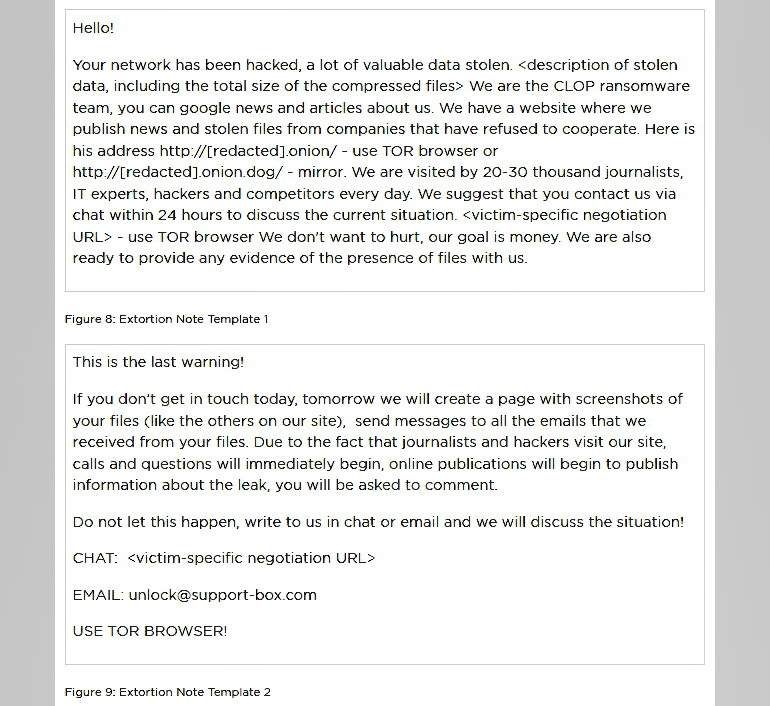
According to the own data of the Accellion company representatives, out of about 300 FTA clients, “less than 100” have become victims of attacks, and among them less than 25 have suffered from data theft. FireEye clarifies that some of these 25 clients are being blackmailed, and hackers are demanding a ransom from them. Attackers contact their victims by email and demand a ransom in bitcoins, otherwise they threaten to publish the stolen information on the Clop ransomware website.
Interesting fact: despite the data of the victims is published on the Clop website, the affected companies did not have a single segment of their internal networks encrypted. That is, they became victims of the classic extortion, not the ransomware.FireEye analysts split these attacks into two distinct clusters of activity, which the company tracks as UNC2546 (exploiting zero-day vulnerabilities on FTA devices) and UNC2582 (sending ransomware emails). At the same time, it is now reported that the infrastructure of both groups intersects with a large hack group FIN11, which FireEye discovered last year.
Victims
Even before the release of the FireEye report, Risky Business researchers found data from the affected companies on the Clop operators’ website. So, hackers have already published information of the following victims:
- geodata company Fugro;
- IT company Danaher;
- Singapore’s largest telecommunications company Singtel;
- Jones Day Law Firm.
Also, other companies and organizations were also notified about the compromise of their systems due to the Accellion FTA hack, although their data did not appear on the hackers’ website.
Among them:
- Reserve Bank of New Zealand;
- Australian Securities and Investment Commission (ASIC);
- Allens Law Firm;
- University of Colorado;
- Washington State Audit Office;
- Berghofer Medical Research Institute QIMR;
- Kroger retail chain.
Let me remind you that The RIPE NCC says unknown hackers tried to attack it.