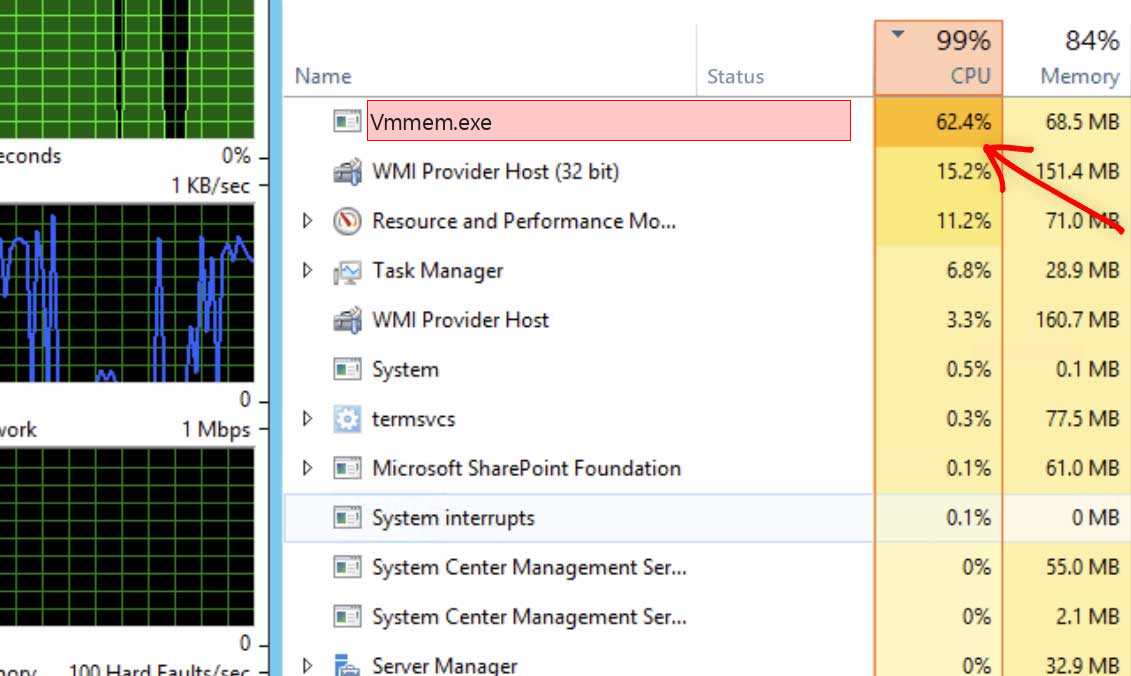
Vmmem is a process associated with the Windows Hypervisor Platform. It is typically found in systems running Windows 10 or Windows Server with Hyper-V functionality enabled. The Windows Hypervisor Platform is a feature in Windows that enables virtualization, allowing users to run virtual machines on their systems.
Vmmem, also known as the Virtual Machine Memory Process, is responsible for managing the memory usage of virtual machines running on the system. It assists in allocating and managing the memory resources required by the virtual machines, ensuring efficient utilization of the underlying hardware. During the operation of virtual machines, vmmem.exe may consume CPU and memory resources. The amount of system resources utilized by vmmem.exe depends on the number and activity of the virtual machines running on the system.
It is important to note that vmmem.exe is a legitimate Windows process and not a virus or malware. However, if you are experiencing high CPU or memory usage attributed to vmmem.exe, it could be an indication of resource-intensive virtual machines or misconfigurations that need to be addressed.
Vmmem – Is it Virus?
If you are not actively using virtual machines or if you find the resource usage of vmmem.exe to be excessive, you have a few options:
- Adjust virtual machine settings. If you are running virtual machines, you can review and adjust their settings to optimize resource allocation. This includes adjusting the amount of allocated memory and CPU cores for each virtual machine.
- Stop or suspend virtual machines. If you are not using certain virtual machines, you can stop or suspend them to free up system resources. This can be done through virtualization management software or the Hyper-V Manager in Windows.
- Disable Hyper-V. If you are not using virtualization features or virtual machines on your system, you can consider disabling Hyper-V altogether. This will prevent vmmem.exe from running and utilizing system resources. Disabling Hyper-V requires administrative privileges and can be done through the “Turn Windows features on or off” settings.
Remember that if you rely on virtual machines for your work or other purposes, reducing or disabling vmmem.exe may impact their functionality or performance. Therefore, it’s important to assess your specific requirements and make adjustments accordingly.
Vmmem.exe as Trojan Coin Miner
Cybercriminals and malware authors are constantly evolving their techniques to exploit legitimate processes for malicious purposes. In rare cases, it’s theoretically possible for malware to disguise itself as vmmem.exe or inject malicious code into the process to conduct unauthorized activities, such as cryptocurrency mining.
If you suspect that vmmem.exe is being used as a miner or exhibiting suspicious behavior, it’s important to investigate further to ensure the security of your system. Here are a few steps you can take:
- Verify the process location: The legitimate vmmem.exe file is typically located in the “C:\Windows\System32” directory. If you find vmmem.exe in any other location, it may be a sign of a malicious process.
- Scan your system: Run a thorough scan using reputable antivirus or anti-malware software to detect and remove any potential malware on your system. Ensure that your antivirus software is up to date with the latest virus definitions.
- Monitor system resources: Keep an eye on your system’s CPU and memory usage. If vmmem.exe is consistently consuming an unusually high amount of system resources even when virtual machines are not running, it could be a cause for concern.
- Enable real-time protection: Make sure that real-time protection is enabled in your antivirus software to actively monitor and prevent any malicious activities on your system.
By practicing good cybersecurity hygiene, such as keeping your operating system and security software up to date, being cautious with downloads and email attachments, and regularly scanning your system for malware, you can help mitigate the risk of malware exploiting legitimate processes like vmmem.exe for malicious purposes.
About cryptocurrency mining
Cryptocurrency mining means the operation of calculating the transaction block hash. That is a basic part of any project based on the blockchain technology. Since this action takes a lot of calculations, a high-end machine is required. Exactly, the GPU is better for this purpose, because they have more cores available. Cryptomining farms are usually constructed of tens and hundreds of graphic cards to conduct their activity effectively. Such computer systems are not usable for “usual” purposes, like gaming or browsing the Web.
Fraudsters who make a profit via this coin miner use someone’s hardware instead, even if they are used for regular activity.
List of the typical coin miner symptoms
How dangerous is the Vmmem as Coin Miner Virus?
First, Vmmem.exe virus makes your PC overloaded. It is unable to run your applications anymore because all CPU power is used by a virus. That malware does not care for your demands, all it focuses on is making money on you. Even if you are patient, and you wait until the browser is open, you will likely experience incredibly slow performance. Pages will open for years, and any sort of login will take about a minute – just a nightmare for a person who works online.
Vmmem.exe Technical Summary.
| File Name | Vmmem.exe |
| Type | Trojan Coin Miner |
| Detection Name | Trojan:Win32/CoinMiner |
| Distribution Method | Software bundling, Intrusive advertisement, redirects to shady sites, etc. |
| Similar behavior | Novpop.exe, Lykaa.exe, File.exe |
| Removal | Download and install GridinSoft Anti-Malware for automatic Vmmem.exe removal. |
“Visible” harm is not a single unpleasant thing coin miners do to your computer. Vmmem.exe coin miner also deals damage to your OS. To perform all malevolent operations properly, it wrecks the security components of your system. You will likely see your Microsoft Defender disabled – malware stops it to prevent recognition. If you check the HOSTS file, you will likely see a lot of new notes – they are brought in by this trojan miner to connect your system to a malicious mining network. All these changes are about to go back to the initial state in the process of computer recovery.
Hardware effects of coin miner activity
Besides making your PC slow, running at peak power for long times may cause damage to your machine and raise power expenses. PC elements are created to easily deal with high load, but they are good with it only when they are in good shape.
A Small and covered CPU fan is quite hard to break. Meanwhile, graphic cards have big and easy-to-access rotors, which can be easily broken if affected while running, for instance, by the user much earlier before the malware injection. Malfunctioning cooling system, together with the unusually high load caused by Vmmem.exe virus can easily lead to graphic card failure1. Graphic cards are also prone to have increased wearing when used for cryptocurrency mining. It is surely a bad case when your GPU’s performance plunges 20-30% just after 1-2 weeks of being exploited in such a way.
How did I get Vmmem.exe coin miner virus?
Coin miners are one of the most prevalent malicious programs through “severe” viruses. Adware often serves as a carrier for Vmmem.exe malware infiltration: it demonstrates the banners, which include a link to malware downloads. Yes, this abstract “malware” can belong to any kind – yet another adware, spyware, rogue, or backdoor. However, the statistics show that approximately 30% of all malware spread with malicious banners are coin miners – and Vmmem.exe is right among them.2
The example of malicious banners you can see in the Internet
An additional way you could get this thing on your computer is by downloading it from an unreliable site as a part of a program. People who spread hacked variants of popular programs (which do not require the license key) have small chances to make money. Hence, there is a huge lure to add malware to the final package of the hacked application and acquire a coin for every setup. Before blaming these individuals for hacking and malware distribution, ask yourself – is it alright to avoid paying for the program in such a way? It is more affordable to pay $20-$30 one time than to pay a much bigger figure for antivirus software as well as new parts for your PC.
How to remove the Vmmem.exe miner from my PC?
Eliminating such a virus involves making use of special app. Proper security tools must have high efficiency at scanning and also be lightweight – to create no problems with utilization even on weak computers. Furthermore, it is better to have on-run protection in your protection tool – to prevent the virus even before it launches. Microsoft Defender lacks these elements for various reasons. That’s why I’d advise you to use a third-party anti-malware program for that objective. GridinSoft Anti-Malware is a perfect choice that fits all of the specified characteristics.3
Before the virus removal, it is important to reboot your Windows into Safe Mode with Networking. Since Vmmem.exe miner consumes a lot of CPU power, it is needed to stop it before launching the security program. Otherwise, your scan will last for years, even though the GridinSoft program is pretty lightweight.
Booting the PC into Safe Mode with Networking
Press the Start button, then choose Power, and click on Reboot while holding the Shift key on the keyboard.
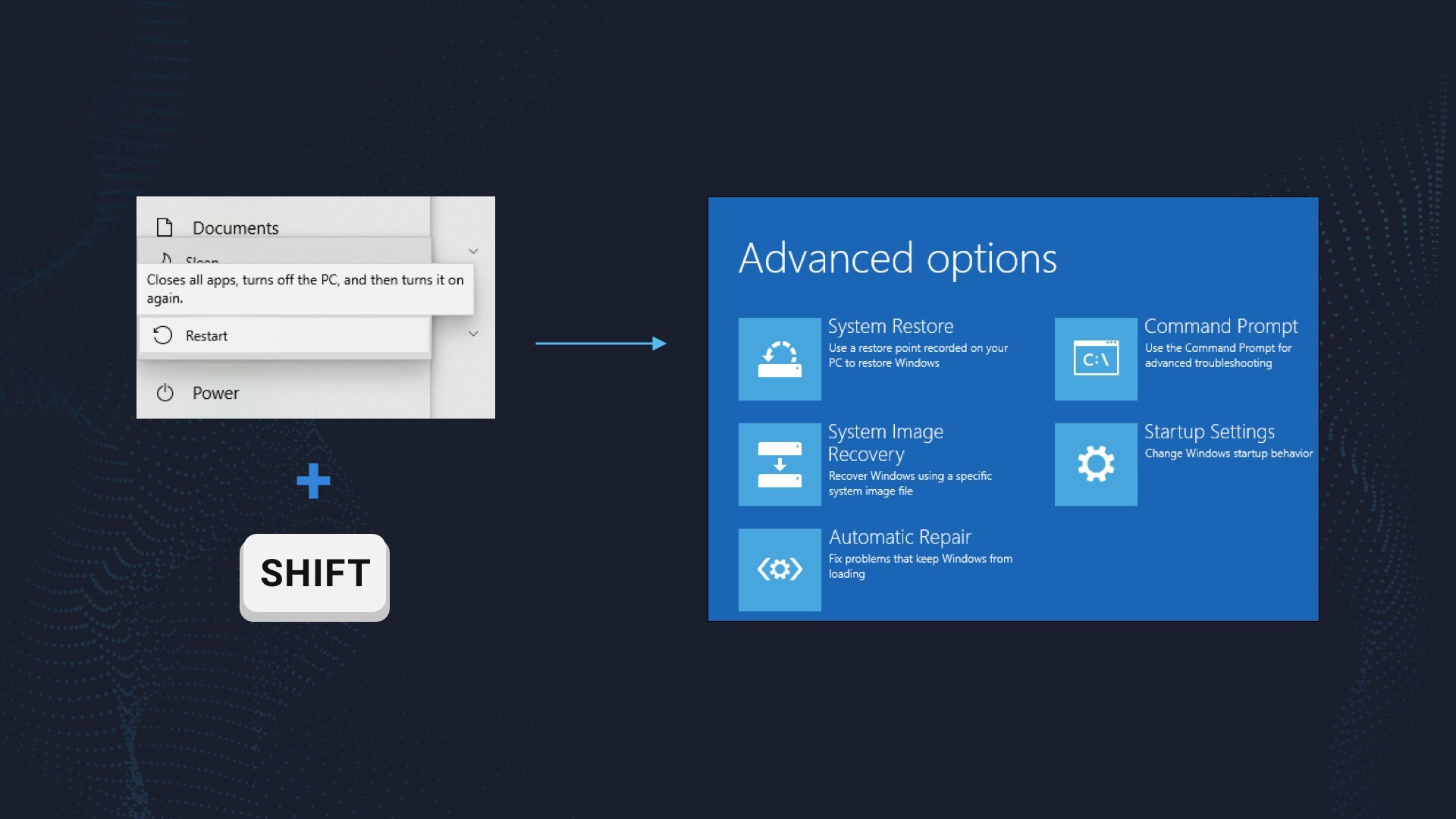
Windows will reboot into recovery mode. In that mode, choose Troubleshoot→ Startup Settings→ Safe Mode with Networking. Press the corresponding button on your keyboard to choose that option.
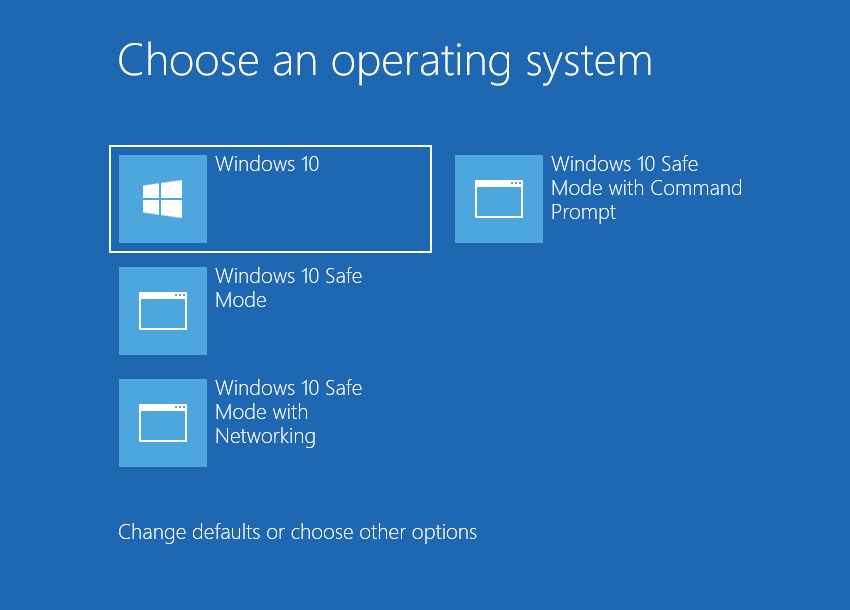
When your computer is in Safe Mode, all third-party programs, along with the majority of non-crucial Windows components, are not launched with the system start. That gives you the ability to clean the computer without dealing with the high CPU usage of the coin miner.
Remove Vmmem.exe coin miner virus with GridinSoft Anti-Malware
Download and install GridinSoft Anti-Malware. You can use this anti-malware program for free during its 6-day trial period. In that term, all functions are available, and it takes no payments to remove malware from your system.
After activating your free trial, start a Full scan. It may last up to 10 minutes. You may use the PC as usual.
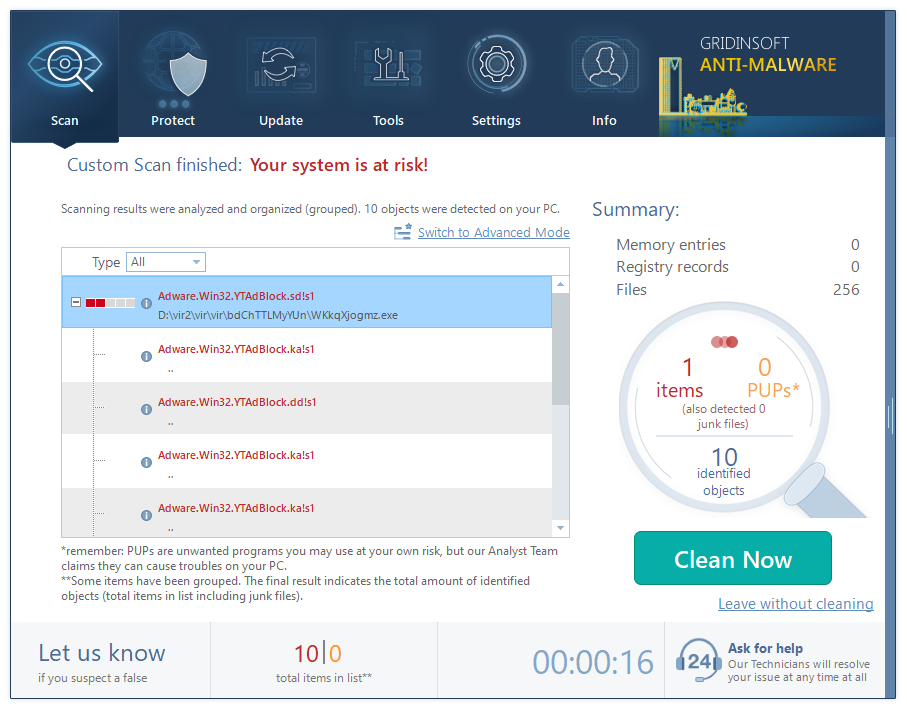
When the scan is finished, press the Clean Now button to remove all detected elements from your system. This procedure takes less than a minute.
Now, you are good to go. Reboot your PC into normal Windows mode and use it just as if there was nothing malicious.
Solutions to Vmmem High Memory and CPU Usage
Name: Vmmem.exe
Description: Vmmem.exe is a process that is associated with the Windows Hypervisor Platform and is primarily found in systems running Windows 10 or Windows Server with Hyper-V enabled. The Windows Hypervisor Platform is a feature in Windows that allows for virtualization, enabling users to run virtual machines on their systems.
Operating System: Windows
Application Category: Trojan
User Review
( votes)References
- About unwanted effects for GPUs in the process of crypto mining.
- Read more about various malware type on Cybersecurity Glossary.
- Our review on GridinSoft Anti-Malware.