In this tutorial, we will provide you with instructions on “How to disable NTLM Authentication in Windows 10“. You will be guided through simple steps to accomplish this task. Let’s get started.
What is the purpose of ‘NTLM Authentication’ in Windows 10?
NTLM1 Authentication in Windows 10: NTLM is a New Technology LAN Manager. It is a special package for security protocols provided by Microsoft to authenticate customers’ identity and safeguard the integrity and confidentiality of their actions. This technology is based on a Challenge-response protocol to confirm the customer without the need to provide a password.
NTLM authenticates customers through a challenge-response method. This process involves three messages: the Negotiation message from the customer, the Challenge message from the server, and the Authentication message from the user. Despite its known vulnerabilities, NTLM is still widely deployed, even on new systems, to ensure compatibility with legacy customers and servers.
NLTM is, nevertheless, supported by Microsoft, however, it has been substituted by ‘Kerberos’2 as the main authentication protocol in Windows 2000 and all further Active Directory (AD) domains. In case you haven’t heard about it, ‘Kerberos’ is authentication protocol that substituted NTLM as the main/common authentication utilities on Windows version 2000 and all further versions. The common difference between ‘Kerberos’ protocol and ‘NTLM’ protocol is whether passwords are hashed or encrypted. NTLM is grounded on ‘Password hashing’ – one-way feature that generates a string of text on an input file, however, ‘Kerberos’ rests on encryption – two way feature that scrambles and unlocks data by means of encryption & decryption keys.
Issues with NTLM protocol:
- Kept password Hash in memory of LSA service can be easily obtained by means of various utilities like mimikatz, and then the hash password may be applied for subsequent attacks.
- Weak or trivial passwords are another factor for NTLM protocol issues.
- The lack of mutual authentication between server and customer that leads to the data interception attacks and unauthorized access to the network data.
- Other NTLM leaks or troubles.
Furthermore, NTLM is grounded on three-way handshake between customer and server in order to authenticate customer while Kerberos rests on two-way procedure that is delivered by means of a ticket generating service or key distribution facility. NTLM protocol was exposed before certain security risks and known security leaks or problems related to password hashing and salting.
NLTM protocol, instead, makes sure that passwords on the server and domain controllers are not ‘salted’. It implies that you can’t add any random string of characters to the hashed password in order to eventually prevent it from cracking attempts. Such vulnerability could let attackers or online frauds crack password via multiple login attempts, and because of weak or trivial password, they could eventually manage to access the account.
Guide to deactivate NTLM Authentication Windows 10 by means of the Group Policy Management Editor.
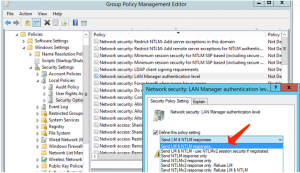
In the first place, the domain administrator would like to be sure that NTLM and LM protocols are not permitted to be applied for authentication in domain. You can define the requested authentication method by means of the domain (or local) policy.
- Apply the ‘Windows + R’ hotkey on keyboard, specify ‘gpmc.msc’ in the opened ‘Run’ dialog box and click on the ‘Ok’ button to launch ‘Group Policy Management Editor’.
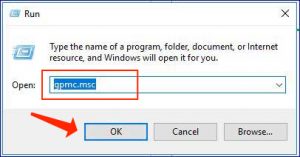
- Proceed to ‘Computer Configurations -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options’.
- Locate ‘Network Security: LAN Manager authentication level’ policy, then double-click on it.
- Choose ‘Send NTLMv2 response only. Refuse LM & NTLM’ feature under ‘Send LM & NTLM responses’ area/dropdown to deny all LM and NTLM requests.
Guide to deactivate NTLM Authentication Windows 10 by means of the Registry Editor.
- Apply the ‘Windows + R’ hotkey on keyboard, specify ‘regedit’ in the revealed ‘Run’ dialog box and click on the ‘Ok’ button to launch ‘Registry Editor’ 3.
- Proceed to below-given destination
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
- At this point, right-click on empty area in right section and choose ‘New > DWORD’ and nominate it to ‘lmCompatibilityLevel’, define its parameter to ‘0 to 5’ and press ‘Ok’ to save your choice.
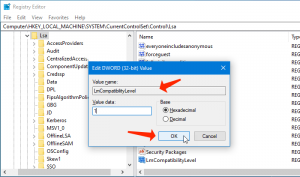
- At this point, option 5 As value data corresponds to ‘Send NTLM response only, refuse LM and NTLM’. Save all the amendments.
Pay attention to this guide: How do I remove Advanced Windows Manager?
Guide to activate NTLM Authentication Audit Logging.
You need to be convinced there are no programs left in the domain that demand application of the NTLM, before deactivating NTLM fully in domain and getting to ‘Kerbeors’ protocol.
- Start ‘Group Policy Management Editor’ by following the above-said recommendations, then proceed to ‘Computer Configurations -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options’ path.
- Locate and activate ‘Network Security: Restrict NTLM: Audit NTLM Authentication in this domain’ policy, and define its value to ‘Enable All’.
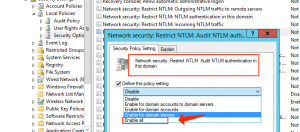
- Repeat the same process to activate ‘Network Security: Restrict NTLM: Audit Incoming NTLM Traffic’ policy.
Guide to examine events of applying NTLM Authentication.
You can find the NTLM Authentication come up in the application and services logs.
- Proceed to ‘Services Logs’ and refer to ‘Microsoft > Windows’.
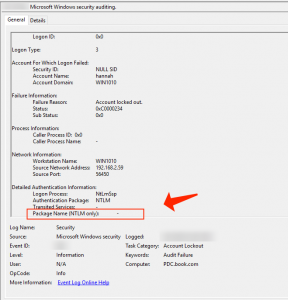
- Take NTLM area of Event Viewer. At this point, you may analyze the events on each server or bring them to central Windows Event Log Collector.
- Locate the apps that are using NTLM in domain, and you have to switch them to apply ‘Kerberos’ possibly by means of SPN.
Consider reading: Parental Controls in Windows 10. Guide to Establish.
Guide to restrict NTLM in Active Directory Domain fully.
The authentication without NTLM will operate differently for each program in our domain, we can add customer accounts to ‘protected users’ Domain group. As soon as the verification is over, you can fully deactivate NTLM Authentication in your Windows domain.
Summary
I am positive this tutorial helped you on How to deactivate NTLM Authentication Windows 10 with the range of simple solutions/approaches. You can read & follow our guidelines to make it possible. In case the tutorial definitely helped you, then you can share the article with other customers to assist them. In case you’ve got any proposals or questions, feel free to share them in the comments section below.
User Review
( votes)References
- NT LAN Manager: https://en.wikipedia.org/wiki/NT_LAN_Manager
- Kerberos (protocol): https://en.wikipedia.org/wiki/Kerberos_(protocol)
- Windows Registry: https://en.wikipedia.org/wiki/Windows_Registry



