Attackers who introduced the Maze encryptor in the Pensacola, Florida network published some of the stolen data. Extortionists said that they wanted to prove in media how serious are their intentions.
The cyberattack on Pensacola city services occurred in early December. As a result, were disrupted e-mail, payment services, and telephone communications; the city’s IT service was forced to disconnect part of the infrastructure in order to block the invasion.Attackers showed a peculiar nobility and did not interfere in the work of emergency services, including 911, the police and the fire department.
We don’t attack hospitals, cancer centers, maternity hospitals and other socially vital objects, up to the point that if someone uses our software to block the latter, we will provide a decrypt for free”, — said cybercriminals that stand behind the Maze attack.
It soon was reported that the criminals demanded a million dollars from the city as a ransom for returning data. The ability to copy information before encrypting files is one of the characteristic features of Maze. It provides criminals with an additional leverage over the victim, who has to assess the risks of publishing classified material.
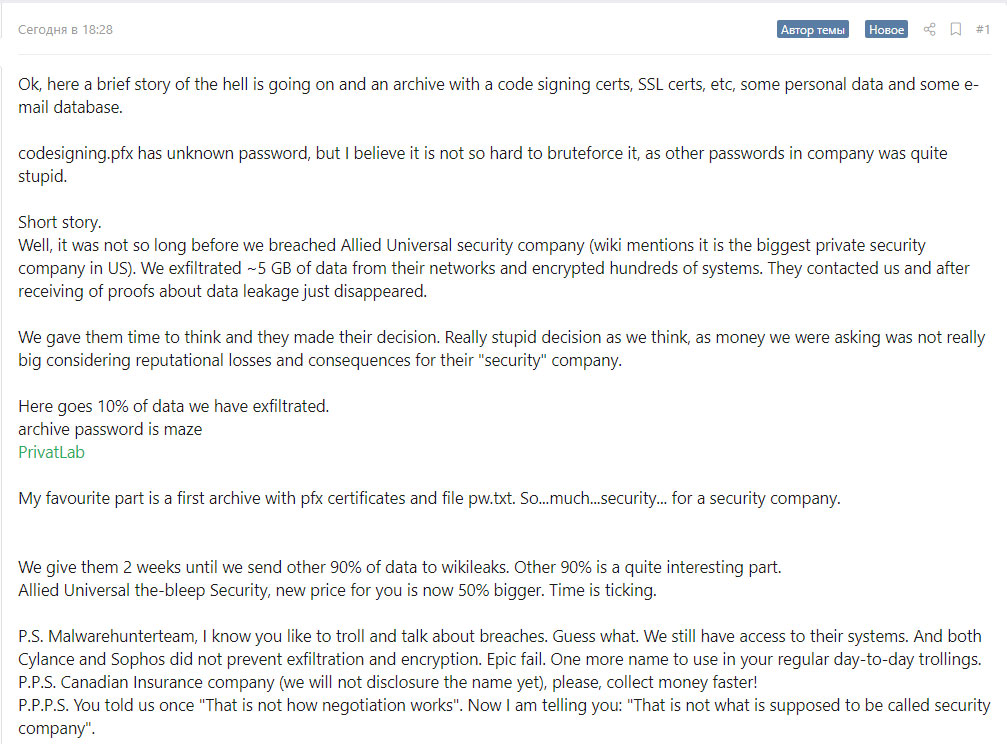
Maze operators are not the first criminals to make money this way. However, unlike many others, they bring their threats to life. In November, cybercriminals made publicly available Allied Universal materials: legal and medical documents, technical data, Active Directory user lists.
In their correspondence with Bleeping Computer, criminals also threatened to conduct a spam campaign using Allied Universal certificates.
The company’s IT specialists stored critical data in the open access, and the defense systems they used were unable to prevent the attack”, – said the cybercriminals.
In the case of Allied Universal, the criminals demanded to pay them 300 BTC. When asked about guarantees, they replied that the data itself does not matter to them, though it would be harmful for the business to publish materials after receiving the ransom.
The Pensacola administration has not yet commented on the publication. It is known that two of 32 GB of data stolen from the city went to the Network. What exactly information contained the dump is not reported.
Recently, American cities and government organizations often become victims of ransomware. In August, more than 20 Texas departments were hit by an unknown cryptographer. A few months earlier, RobbinHood attacked the city of Baltimore, using the EternalBlue exploit stolen from the NSA.
In 2018, in Alaska, a cyberattack paralyzed the administration infrastructure of one of the largest districts for several days.
Cybercriminals can use popular applications to spread malware. For example, Zeppelin ransomware operators used the ConnectWise Control remote desktop took that is used by companies in business processes.
Causes of data leaks:
According to experts, the root causes of all these incidents are the personnel problems of state organizations and their outdated computer park.
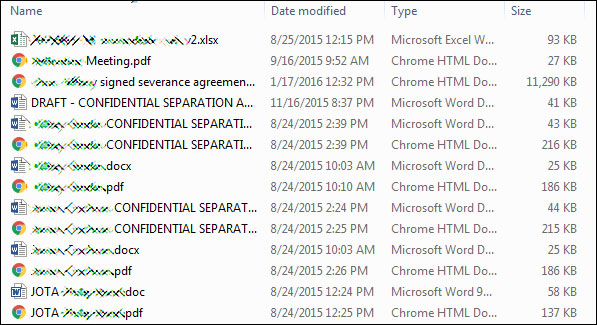
Leaked files
In a later email to bleepingcomputer they shared a link to a post on a Russian hacker and malware forum that once again describes the breach and also contains a link to the leaked data. They also stated that they will distribute the other 90% of the leaked data to WikiLeaks if an increased ransom of $3.8 million dollars is not paid.