Experts at INRIA, a French research institute working in computer science, control theory and applied mathematics, report that law enforcement agencies often forget to remove sensitive data from PDF documents they publish on their websites.
As a result, a lot of confidential information can be gleaned from these files, which can then be used for attacks.Experts came to such conclusions after studying 39 664 PDF-files published on 75 websites of law enforcement agencies from 47 countries. It found that only 38 agencies have strict software policies and regularly update their software.
Thus, it was possible to recover confidential data from 76% of the analyzed files.
Specifically, the researchers found:
- name of the author;
- the name of the PDF application;
- information about the operating system;
- device data;
- e-mail of the author of the document;
- information about the path to the file;
- comments and annotations.
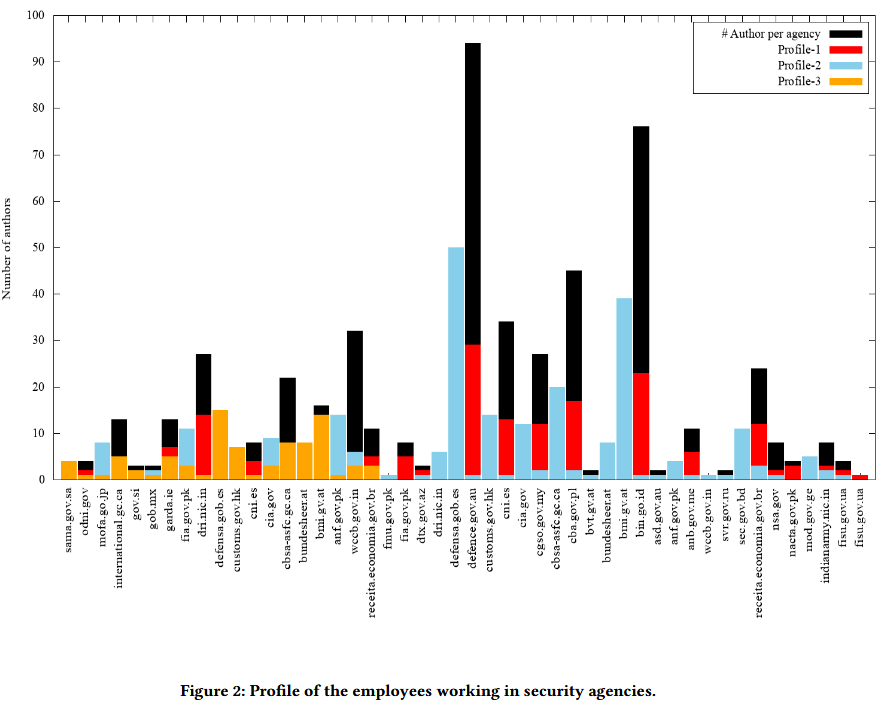
Researchers warn that attackers can specifically collect such documents from the websites of law enforcement agencies and create profiles for both individual employees and departments.
Even when law enforcements try to clean up metadata and artifacts from their PDFs, clean-up rarely meets standards and usually leaves usable data behind. According to the researchers, only 7 out of 75 agencies generally tried to clean up PDF documents, but in fact only 3 of them removed all sensitive data from the files.
Let me remind you that we also wrote that Google developers promised not to track users using cookies and not to trace them in any other way for targeted advertising. And that the NSA published conference service guide.
