Zscaler experts have published a report on the InnfiRAT malware, which specializes in stealing cryptocurrency and steals data from Litecoin and Bitcoin wallets.
Information security specialists first noticed this malware in 2017, but only now, researchers have subjected it to a detailed analysis. This .NET-written threat is known to spread through phishing emails containing malicious attachments or links to downloaded files.Having penetrated the victim’s machine, InnfiRAT copies itself to %AppData% under the mask of NvidiaDriver.exe, and then puts the PE file (Base64) in the memory, which is decoded into the binary directly involved in malicious activity. The system also creates a scheduled task for daily execution of the payload from the NvidiaDriver.exe file (in case of detection and elimination of infection).
Before starting work, the Trojan checks whether it is running in the sandbox and on the virtual machine. If everything is in order, the Trojan determines the HWID of the machine and the user’s country of residence. This data is transferred to the management server, and the Malware waits for further instructions.
Read also: Attackers can hack smartphones Samsung, Huawei, LG and Sony via SMS
Malicious operators may order InnfiRAT to search for certain processes and terminate them, including the Chrome, Yandex, Kometa, Amigo, Torch, Orbitum, Opera, and Mozilla browsers. Obviously, this is done in order to unlock user profiles and simplify data collection. In addition, the malware detects monitoring tools such as Taskmgr, Process Hacker, Process Explorer and Process Monitor, and also terminates their work.
InnfiRAT is able to use additional payloads, steal files and capture browser cookies to collect stored credentials.
“In addition, this RAT has ScreenShot functionality so it can grab information from open windows. For example, if the user is reading email, the malware takes a screenshot. It also checks for other applications running on the system, such as an active antivirus program”, — say Zscaler specialists.
However, the main goal of the Malvare remains cryptocurrency, including Bitcoin and Litecoin. In search of wallets and wallet.dat files, the Trojan scans %AppData%\Litecoin\ and %AppData%\Bitcoin\ and immediately transfers all the information it finds to the management server.
In addition to the above, InnfiRAT operators can also send their malvari the following commands:
- SendUrlAndExecute(string URL) – download the file from the specified URL and execute it;
- ProfileInfo() – collect and filter information about the network, location and equipment;
- LoadLogs() – write files to specific folders;
- LoadProcesses() – get a list of running processes and transfer to a remote server;
- Kill(int process) – eliminate a specific process on the victim’s computer;
- RunCommand(string command) – execute an arbitrary command on the victim’s computer;
- ClearCooks() – clear cookies for a specific browser.
How to protect yourself from InnfiRAT?
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes.2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
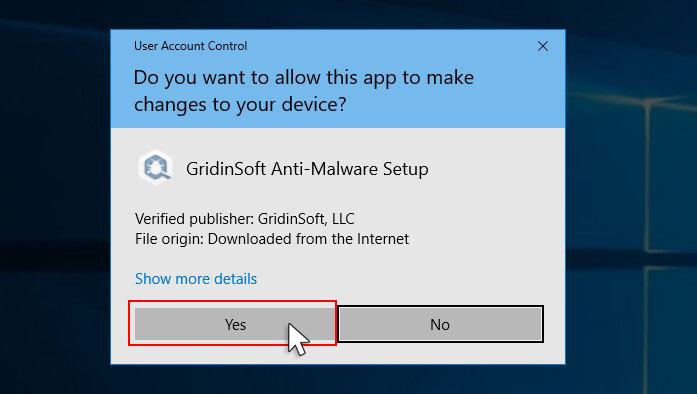
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Generic PUA GC files and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
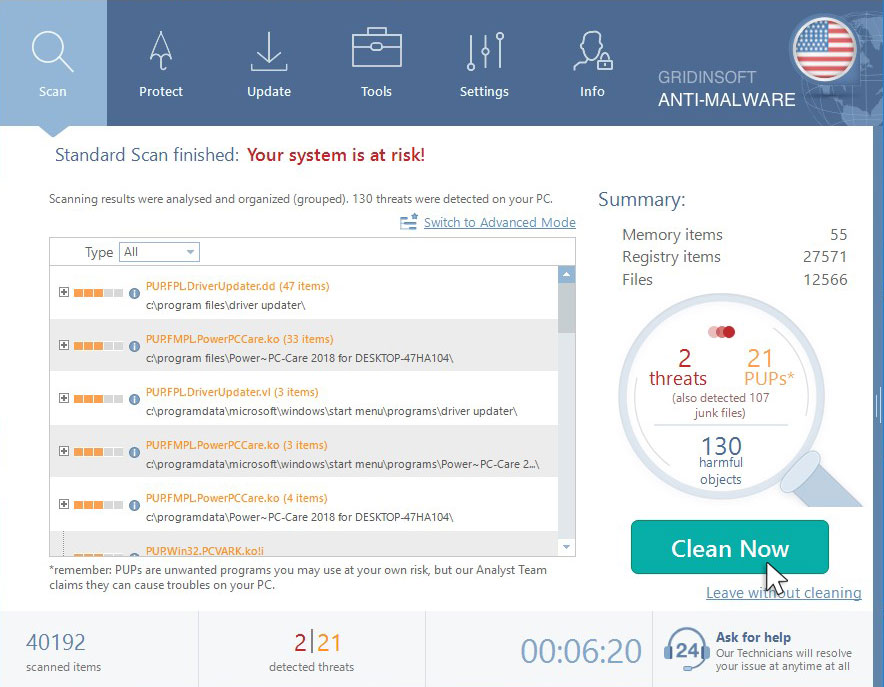
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison