To stay in touch with the modern environment, malware should receive corresponding updates. Cybercriminal world has even more harsh rules than the legitimate one, thus it is an all-or-none game. Recent changes to IceID bot confirm that thesis — they switched a full-fledged banking stealer to malware delivery.
What is IceID Malware?
IceID is known as a banking Trojan malware that first emerged in 2017. It is also known as BokBot, Botovod, and Koler. IceID is designed to steal sensitive information, primarily banking credentials and personally identifiable information, from infected machines. Once installed on a victim’s computer, the malware can also perform a range of malicious activities, modifying system settings, and monitoring user activity.
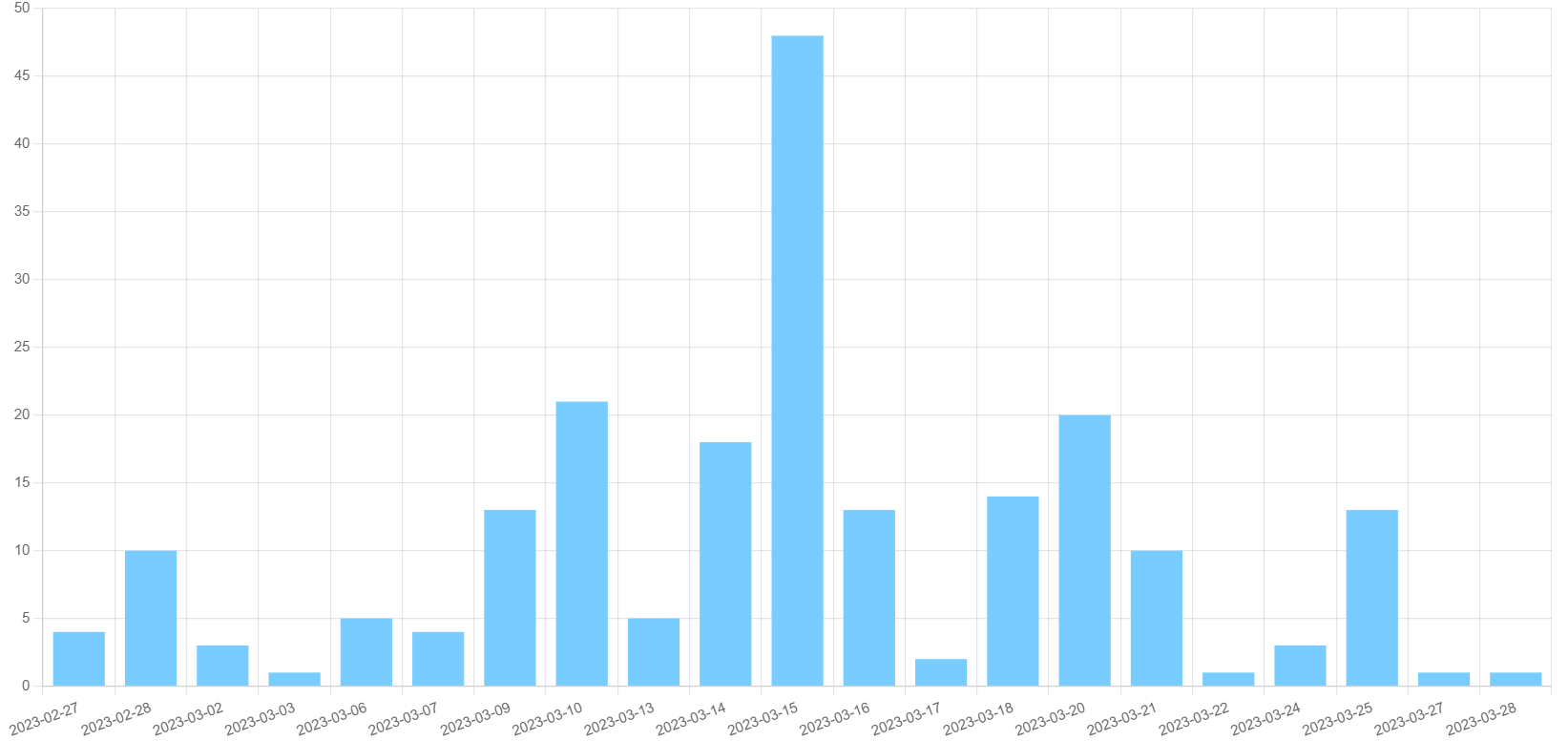
Chart of recent IceID activity
IceID is primarily distributed via spam emails, often with malicious attachments or links to websites hosting the malware. Once the victim clicks on the attachment or link, the malware is downloaded onto their computer and begins its malicious activities.
One of the key features of IceID is its ability to evade detection by traditional antivirus software. The malware uses a variety of techniques to hide its presence on the infected machine, including encryption and obfuscation of its code. It also has the ability to detect and evade virtual machines and sandboxes used for malware analysis.
IceID Moves to Dropper Functionality
The ability to deliver other malware to infected systems – the definitive for dropper malware – was present in IceID almost from the beginning. It is a useful function that may see a lot of applications in cyberattacks. It works especially well when the crook established a large enough botnet, grabbed all the valuable data with stealer functions, and then wants to have slightly more profit. The rascal goes on the Darknet marketplaces, and offers to deliver malware to his network for reasonable pay.
However, IceID variants that popped out in late 2022-early 2023 appear to have no stealer functionality at all. Samples collect only the most basic information needed to fingerprint the system. Instead, the malware offers the ability to drop other malware – as genuine droppers like Amadey do. The reasons for such a shift are not disclosed. Moreover, these samples appear to be forks of an original IceID, not the officially offered update. Even more, confusion is added by the fact that the modified samples were already used by several threat actors associated with an original one in the past.
Emotet Story Repeated?
Emotet is an older malware sample, that originated in 2014. It initially had only banking stealer functionality but received dropper capabilities later on. At some point, its stealer capabilities became shadowed by the ability to drop other malware. Since then, Emotet was primarily used to unite attacked systems into botnets and deliver malware – without missing a chance to steal something valuable. Despite such prioritising, it did not lose its stealer capabilities. The double-action nature of this malware made it a serious pain in the neck of law enforcement. Despite a couple of arrests of actors related to Emotet development and spreading, it still runs smoothly.
The parallels between the story of Emotet and current things with IceID are obvious. For sure, the latter did not receive as much attention and ill fame as Emotet did. But it is probably to come – and only time will uncover the truth. These days, in 2023, the need for good anti-malware software is obvious. Aside from reactive solutions, it is also recommended to apply preventive measures.
How to protect your system?
Main way to spread malware over the past 3 years was email spam. Messages that mimic the genuine mailing from Amazon, FedEx or govt organisations contain the file which triggers malware deployment. Fortunately, detecting whether it is a fraud is not a problem: crooks cannot use genuine email addresses. Additionally, they sometimes have poor English – thus the email body will be full of mistakes. These signs should be your red flags.
The typical example of a bait email. The attached file contains malware
Update software as often as possible. Most issues that make malware deployment and lateral movement easier are addressed steadily in minor patches. It may be inconvenient to install them right away, but try to pick the time for that operation. Another great approach is to monitor whether the upcoming update is fixing some critical vulnerabilities.

