Stealers are a type of malware whose name speaks for itself. Their main goal is to steal confidential user data. By gaining access to the victim’s machine, they can steal logins and passwords from social networks, banks, electronic wallets, email, cryptocurrency wallet data, etc. Today, let’s look at Raccoon Stealer, which recently attracted some attention.
What is a Raccoon Stealer?
Raccoon stealer is an example of malware that specializes in stealing sensitive information from infected computers. Once installed, Raccoon can collect a wide range of data, including browser history, passwords, cookies, credit card information, and cryptocurrency wallet information. This information is then sent to a remote server controlled by the malware operators.
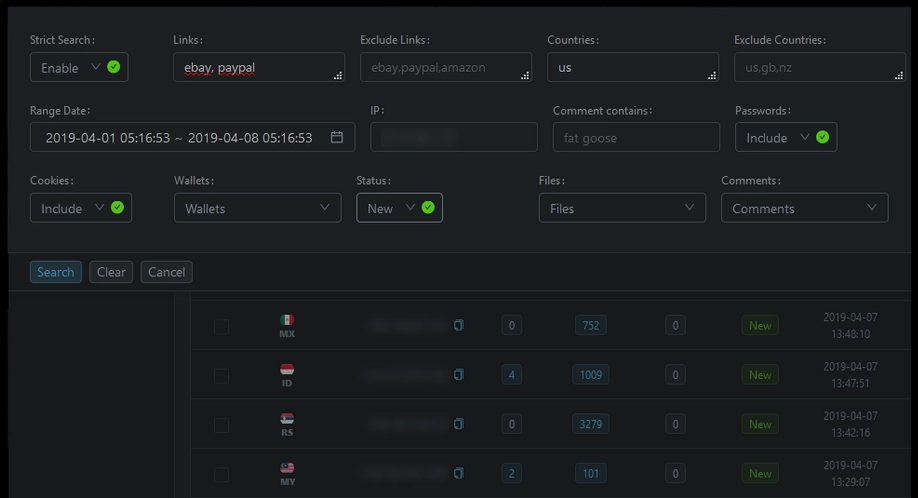
Raccoon v1 panel
Beginning 2019, Raccoon has been involved in numerous high-profile attacks on organizations worldwide. Its success is partly due to its use of advanced anti-detection techniques, such as sandbox bypass and code obfuscation, making it difficult for security researchers to analyze and detect it. In addition, malware is constantly evolving. It can work as standalone or complementary malware, and developers of this malware publish extensive messages on relevant forums where they advertise their brainchild.
Raccoon Stealer v2
In March 2022, a message appeared on a hacker forum announcing the temporary closure of Raccoon Stealer due to the death of a key developer and administrator during the early days of Russia’s invasion of Ukraine. The post also warned that anyone attempting to sell Raccoon before announcing the next release be considered a scammer. However, on June 30, 2022, a Telegram channel dedicated to distributing and advertising Raccoon Stealer announced version v2. The malware will sell by subscription for $150 per week or $275 monthly (the previous version cost $75 and $200, respectively) and has administrative access to the malware builder. However, the developers caution buyers against sharing the malware with anyone, including malware analysts.
The report described the advantages of the new version over the previous one, one of which was the redesigned code base written in C. As a result, the malware became even more stealthy than during the last version, which was written in C++. It also changed how malware communicates with the C&C server and the data-stealing mechanism. According to reports, the first sample of Raccoon v2 was detected in action within a week. By the end of 2022, the number of victims of Raccoon Stealer reached about a million. The main channel for spreading the malware are the Darknet hacker forums and a dedicated Telegram community.
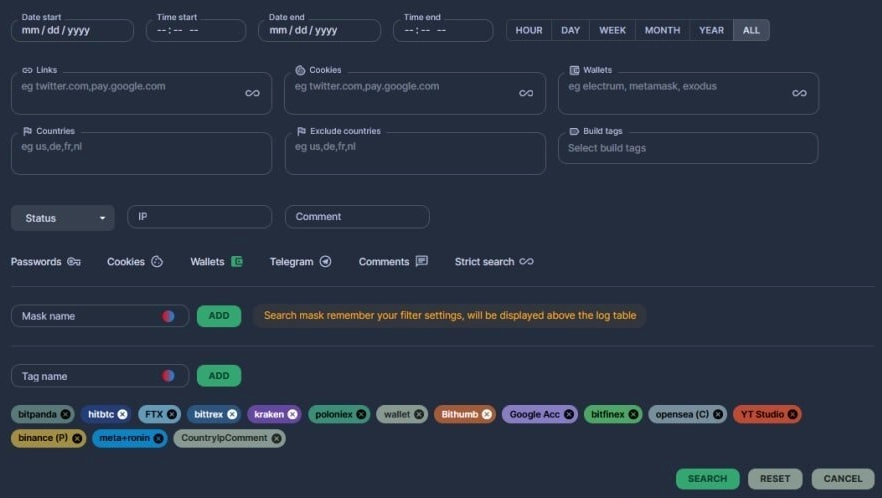
Raccoon v2 panel
How does it work?
In addition to its primary purpose, Raccoon Stealer can act as a downloader, making it versatile for downloading specific files to a victim’s system and using a botnet of Raccoon-infected PCs. Furthermore, each malware sample is uniquely built, making it difficult for security tools to detect. Although both versions use base64 encoding, version 2 includes RC4 encryption with a hard-coded decryption key in the malware executable. The new version also inserts several unnecessary codes into the malware code, making reverse-engineering analysis difficult. In addition, the malware requires additional dynamic link libraries, which it receives from the command and control server during the initial data exchange to decrypt and save data.
The latest version of Raccoon Stealer has a packaging and encryption feature by default. In contrast, the previous version did not have these detection protections. In addition, the new version includes anti-VM and anti-sandboxing features. However, despite the implementation of these measures, there were cases where the latest version arrived on target systems in unpacked form, indicating that it is possible to disable these features when generating samples.
C2 communication
Raccoon Stealer uses a predefined list of IP addresses to connect to its command and control server. However, obtaining these IP addresses was different in the first version than in the second: the first version of Raccoon Stealer sent a request to the Telegram messenger and got a list of C2 addresses from there. The new version contains a list of hardcoded C2 addresses, which is added at the stage of malware generation. When Raccoon Stealer first contacts the command and control server, it receives DLLs and configuration files. The malware then resets the collected information and sends a POST request with the parameters bot_id and config_id. The libraries of the first version are slightly different from the second. However, listed below are similar and different libraries:
- v1
- Shell32.dll
- User32.dll
- Advapi32.dll
- Crypt32.dll
- Shlwapi.dll
- Ole32.dll
- Kernel32.dll
- WinHTTP.dll
- Userenv.dll
- Gdi32.dll
- GdiPlus.dll
- Bcrypt.dll
- Ktmw32.dll
- v2
- Shell32.dll
- User32.dll
- Advapi32.dll
- Crypt32.dll
- Shlwapi.dll
- Ole32.dll
- Kernel32.dll
- WinInet.dll
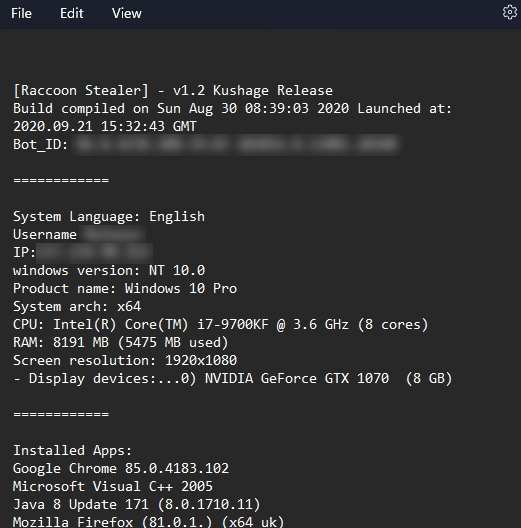
System fingerprint captured by Raccoon
Launching
After obtaining the necessary libraries, Raccoon Stealer decrypts its code lines with a hard-coded key and performs its dirty work. Although these libraries are generally not malicious, the malware uses them to perform decryption operations and steal data. However, the previous version of Raccoon Stealer did not use many sandbox protections; it even contained lines of code that were not encrypted.
Execution
The differences between the old and new versions of Raccoon Stealer become more evident when the malware is downloaded and runs on an infected system. For example, in the first version, Windows API functions were loaded statically, making the code less stealthy. In contrast, API functions are loaded dynamically in the second version using the LoadLibrary and GetProcAddress functions, making it very difficult to block the malware by blocking the entire API.
In addition, Raccoon creates a mutex to prevent multiple copies from running on the same machine and checks whether it is running as a SYSTEM or LocalSystem user. Depending on the result, it uses different methods to enumerate system processes. In the end, the most typical procedure, which every malware created in post-Soviet countries has to perform, is checking the system’s localization. It scans the system language parameters for Russian, Belarusian, Uzbek, Kazakh, Kyrgyz, Armenian, Tajik, or Ukrainian. It suspends execution if any of them is detected.
Data collection
Once the initial preparation is complete, Raccoon Stealer scans the infected device for data. By default, it saves in the /%Username%/Temp folder (although an updated version allows changing this location). Next, the malware fingerprint the system by accessing the registry and retrieving the MachineID and username.
As shown by reverse engineering, the malware then collects general information about the infected system, which includes the following data:
- OS version, revision, build
- System language
- A list of user profiles
- Number of CPU cores
- RAM capacity
- Screen resolution
- GPU model
- System IP address
- List of installed applications
Next, it also searches for information, primarily targeting browser cookies and files containing passwords. To do this, it looks at both popular and not-so-popular browser files. Here are some of them:
- Firefox
- Pale Moon
- SeaMonkey
- Chrome
- Opera
- Amigo
- Torch
- MS Edge
- Bromium
- Xpom
- Kometa
- GO!
In particular, the malware checks browsers for the following cryptocurrency wallet extensions:
- Coinbase
- Brave
- TON
- Liquality
- Phantom
- WavesKeeper
- Solflare
- GuildWallet
- MetaMaskExtension
- ICONex
- CloverWallet
- MetaX
- Sollet
- KHC
- Ronin
- AuroWallet
- SaturnWallet
- Keplr
- CyanoWallet
- JaxxLibertyExtension
- Coin98
- Goby
- NeoLine
- PolymeshWallet
- Coinbase AuroWallet
- Temple
- Rabby
- BitKeep
- GameStop
- EzBox
- Cosmostation
- Stargazer
- XDEFI
- JaxxLiberty
After scanning browsers, Raccoon Stealer looks for cryptocurrency-related items. For directories of specific cryptocurrency wallets, by checking the drive, and if it finds them, the malware steals files that can store wallet data and registration information. It is interested in the following wallets:
- Binance
- Guarda
- Exodus
- Coinomi
- Wasabi
- Electrum-LTC
- JaxxLiberty
- BlockstreamGreen
- Atomic
- Electrum
- MyMonero
- Monero
- Ledger Live
- ElectronCash
Additional payload
The updated version allows you to send additional malicious files to an infected computer, i.e., to perform the function of a dropper. Although it can send any malware, the creators suggest using a keylogger and clipboard capture. The malware uses one of the specified IP addresses to receive the malicious file. When the malicious file arrives, it is often disguised as a system file. However, it has a random name, usually consisting of strings of numbers. Sometimes, it may also impersonate an MS Office file with a similarly random name.
Exfiltration
Once Raccoon has finished collecting essential data from the infected computer, it proceeds to prepare the stolen information for retrieval. Although this malware can send all retrieved information, it can only send preliminary results, such as password files and cookies. As for the rest of the data – it saves it in the archive that was specified when the malware was created. Since the first version of Raccoon did not provide a centralized log download function, the operator had to download files from different servers manually. However, the second version of Raccoon Stealer already allows the operator to set up notifications via Telegram, including snippets of stolen information. In addition, the admin panel automatically categorizes the files.
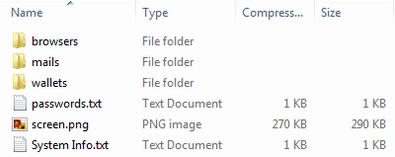
All data is collected and ready to be sent.
Spreading ways
The most common way to deliver Raccoon malware in 2022 was via email spam. This method is time-tested, as it is designed for something other than avoiding powerful antivirus software but for gullible users. Scammers can use classic and targeted phishing, depending on the target. The malicious script is stored in macros embedded in MS Office files. It connects to the command and control server immediately after launch. The last thing left is to convince the victim to click the “Enable macro execution” button since this feature is disabled by default.
Another Raccoon delivery method, confirmed in the research, is redirected to exploit sites. However, this method requires page compromise to redirect users to a target site that injects the malware and causes the victim’s PC to execute it. The malicious script runs in a PowerShell environment and loads the payload from C2. It has essentially the same functionality as the script in macros but is implemented via PowerShell commands.
Unfortunately, the availability of Raccoon for anyone to buy involves the most unpredictable distribution methods. For example, spyware distribution through Google ads has recently been gaining popularity. This way, search results display an advertisement containing a link to a fake site imitating a page from a legitimate software developer. Although no cases of Raccoon using this approach have been reported, it begs the logical question of why the popular search engine does not filter the ads it displays to users.
Protective measures against Raccoon Stealer
It is best to take preventive measures to avoid unpleasant consequences caused by Raccoon Stealer. As with other malware, prevention is critical. The following tips will help keep the chances of getting problems from Raccoon Stealer to a minimum:
- Avoid interacting with suspicious emails, as Raccoon usually spreads through spam. Such emails often contain strange requests or notifications, making them easy to spot with proper attention. Always check the sender’s address, and do not open attachments or links in suspicious emails. For example, an official email from Coinbase will not have a sender address of “shanaazangin@tayu.cl”
- Be careful about the links you click; compromised websites or exploited landing pages are often used to spread more sophisticated malware. No matter how convincing an email from a colleague might be, we recommend that you ensure he sends the email before clicking on the links. In addition, avoid any links that lead to unfamiliar websites or shortened links.
- Consider purchasing advanced anti-malware tool. Using a reliable anti-malware program provides added security and eases the burden of manually checking emails and links. We recommend GridinSoft Anti-Malware because its advanced scanning system detects malware by signature and behavior, providing everyday security and protection during a malware attack.
Raccoon Stealer IoCs
URLs
maper[.]info
tgraph[.]io Telegram C&C
telegram[.]services Telegram C&C
tlgr[.]org Telegram C&C
tttttt[.]me Telegram C&C
C2 IP addresses
hxxp://45.9.74[.]36/
hxxp://34.90.238[.]61
hxxp://35.198.183[.]218
hxxp://195.201.225[.]248
hxxp://88.119.170[.]241
Hash
MD5: 09a5a11cc2f7333109e95b82b8f1de27
MD5: b53dc2fbd0b26a1617d2d6c08ca8b567
MD5: 8fc01fa9af99cf31ddc968c678fc8f63
MD5: d831d6c9a3a3ec4a024bf43994227aa0
MD5: 21465615bcd479755c4d02c2b5947b61
SHA256: 08fb068aae8bfbf4d88d57207312ef0767464f847c51c3794faa472407da1549
SHA256: 6e021131e08f2f2dc661ebedbc1ea0f6f720900e4cab861a0d272fe66e58c788
SHA256: e86cc9a1b1fd4ed40be3c27b1144f8c20471024ab50691bf0078b947239473c1
SHA256: 17bc587a969dc167ee18c17e26d94ec9ecf3652ba3b0051d5d8d14d51df22d3a
SHA256: 1b012d01c86be5d68959504d362c52170b27d726cf2943e2e0250506a29c765a

