Bleeping Computer journalists drew attention to an interesting utility recently created by information security expert Florian Roth. The utility is called Raccine (Ransomware vaccine) and it protects against the actions of ransomware, automatically eliminating any processes trying to delete shadow copies in Windows using vssadmin.exe.
The fact is that ransomware operators do not want their victims to use this OS feature to recover their files for free, so almost any ransomware malware first of all deletes all shadow copies from the infected machine.So, one way to remove them is to use the vssadmin.exe command: vssadmin delete shadows /all /quiet. Another way is to use the resize command to set the amount of storage that Windows allocates for shadow copies. This command will also erase existing snapshots: vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=401MB.
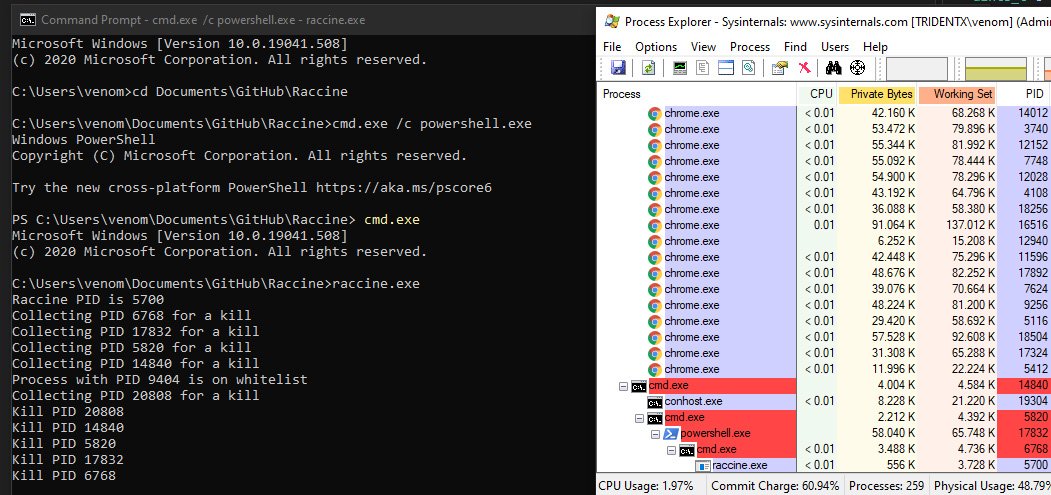
Raccine’s principle of work is simple: it registers raccine.exe as a debugger for vssadmin.exe through the Windows registry and the Windows Image File Execution Options key. After registering, each time vssadmin.exe is started, Raccine is also launched to check if vssadmin is trying to delete shadow copies.
If the utility detects that a process is using vssadmin delete or vssadmin resize shadowstorage, it automatically terminates it, thereby interfering with the operation of the ransomware.
Bleeping Computer reporters note that some modern ransomware removes shadow copies using other commands, including:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$ _.Delete();}
WMIC.exe shadowcopy delete /nointeractive
Alas, in such cases, Raccine cannot do anything, but Roth promises to expand the functionality of the utility over time so that it can recognize such methods.
Also in the future, Roth plans to add some programs to Raccine’s exceptions so that they would not be stopped with an error message.
Let me also remind you of some other useful utilities: EmoCheck utility detects Emotet infection, and, for example, a free utility from ESET finds BlueKeep vulnerabilities.

