It turns out that people still need to hear some of the most basic digital security rules again and again, and that’s alright. As we always say, it is hard to second-guess criminals’ actions if you are not a criminal. Here we explain the necessity to change any network device’s default password to a hard-to-break one.
We will also clarify the dangers of leaving the default credentials and provide default passwords to a number of widely used devices like printers and routers based on popular queries.
What is Internet of Things?
The Internet of Things (IoT) is the concept of the network, wherein not only computers and phones are the digital vehicles for humans, but virtually any device could have a powerful processor and an operating system, be connected to the Internet, feature an interface, etc. All the devices that satisfy this principle, at least partly, are called IoT devices.
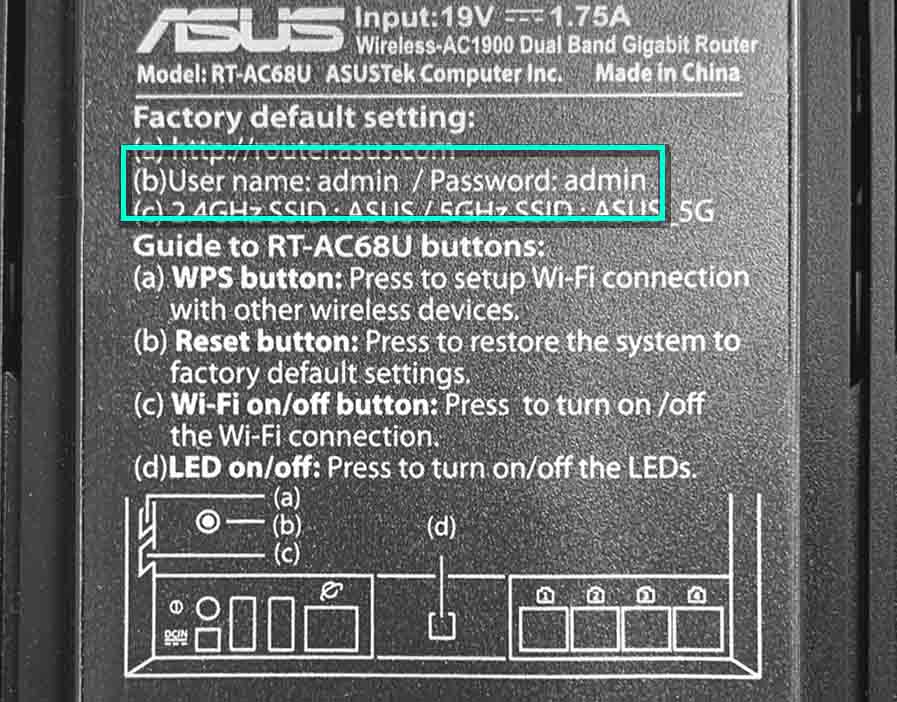
All web-compatible devices surely have an interface and can be connected to. Upon purchase, Netgear, TP-Link, Arris, Hikvision, Linksys, Brother, Raspberry, HP, UniFi, Axis, QNAP, SonicWall, Yealink, Cisco, ASUS, Kyocera, Reolink, Wisenet, Polycom, Lorex, Canon, and other devices are given default password (and login) values so that the users can access them. Manufacturers strongly suggest that users change these passwords and logins as soon as possible. Unfortunately, users neglect this advice more often than not. Such indiscretion often leads to infliction of irreparable harm.
What threat is there, you might ask. Of course, it is hard to imagine anything critical happening if anyone hacks your coffee machine (though that is also unwanted), but imagine a tamperer getting into your security camera, garage door, Internet router, etc. What about a car?
What may go wrong if you keep default password?
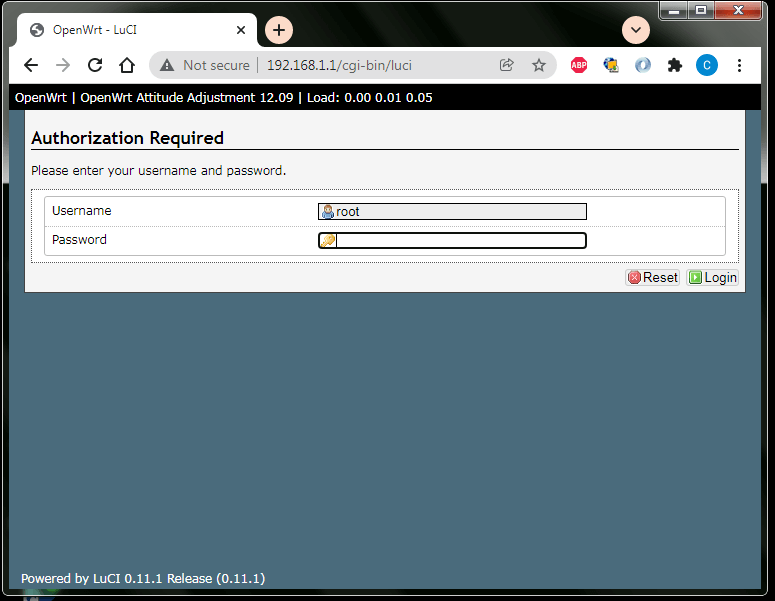
Do you think your wi-fi network is protected enough by the password? If your router remains protected by its default password – it is not protected at all. Anyone can pick a needed login/password pair using lists of them, vastly present on the web, and make your wi-fi absolutely free. Later on, unbeknownst to you, the hackers can use your IP, for which read – your digital passport, and conduct any outlaw activity on behalf of your name.
And that is only a quick sketch of what can happen. To connect your device to your PC is the same thing as installing a program. Consider reading this article on Wired about sex toys being hacked to get a mere glimpse of the weird world we’re sailing into. And to shift the tone of the story from joking to eerie, take a look at this article about a hacked wifi router granting criminals access to a lot of smart home devices.
And there are dozens or even hundreds of websites that provide users with immense sheets of default passwords for all sorts of IoT devices. It is needless to say that all gadgets “protected” by default passwords are, in fact, bare. Hackers need no effort taken to gain control over these gadgets.
Can hackers break a password?
Presume we have changed default passwords on our devices for our thought up passwords. But we know that machines can pick passwords by so-called brute force. This attack implies trying one password after another until the entered password turns out to be correct. And how do we protect our IoT devices from brute force code-breaking?
Don’t worry! Brute force attacks are not omnipotent. Naturally, long passwords are harder to beat. Therefore, you know what to do. What you should care about is whether your password remains unknown to anyone except you. Tamperers very often use social engineering, which means that before using brute force, they’d use all possible ways to learn your password or get any hints on what it could be.
Default passwords to some popular devices
We list default logins and passwords in the table below. This article is not devoted to providing these credentials. However, if you find what you need here, we will partly accomplish our task, as you will get a quick insight into how easy one can gain access to an unprotected device. In some cases, you might need to pick the right login/password pair out of the offered options, but this selection will hopefully spare a lot of your time anyway. We give a device’s default IP address (if available) in the fourth column of the table. You might find it handy if you prefer using a web browser to connect to your device.
| Device | Login | Default Password | Device IP |
| netgear | admin | password | 192.168.1.1 / 192.168.0.1 |
| tp link | admin | admin | 192.168.1.1 |
| arris | admin | password | 192.168.100.1 |
| hikvision | admin | 12345 | 192.168.1.64 / 192.0.0.64 |
| linksys | admin | admin | 192.168.1.1 |
| brother | admin / (none) | access | 192.168.43.172 |
| raspberry pi | pi | raspberry | 192.168.1.179 / 192.168.0.174 |
| pfsense | admin | pfsense | 192.168.1.1 |
| brother printer | admin / (none) | access | 192.168.43.172 |
| hp printer | admin / administrator | admin / 1234567 / admin123 / (none) | 169.254.X.X |
| unifi | ubnt | ubnt | 192.168.1.1 |
| axis camera | root | pass | 192.168.0.90 |
| netgear router | admin | password | 192.168.1.1 |
| qnap | admin | admin (or device’s MAC1 address) | 169.254.100.100:8080 |
| sonicwall | admin | password | 192.168.168.168 |
| yealink | admin | admin | 192.168.0.10 |
| cisco switch | admin / cisco / (none) | admin / cisco / (none) | 192.168.1.254 |
| asus router | admin / root / (none) | admin / root | 192.168.1.1 |
| kyocera | admin / (none) / root | admin / PASSWORD / root | 192.168.0.1 |
| reolink | admin | (none) | 192.168.X.X |
| wisenet | (none) | (blank) | 192.168.1.100 |
| polycom | Polycom / admin | 123 / 456 / 789 / 72227 / (none) | 192.168.X.X |
| lorex | admin | 000000 / admin | To be defined |
| canon | admin / administrator | (none) / canon / printer serial number /7654321 | 192.168.X.X |
| netgear nighthawk | admin | password | 192.168.1.1 / 192.168.0.1 |
| orbi | admin | password | 192.168.1.1 |
| nzbget | nzbget | tegbzn6789 | 192.168.XX.XXX:6789 |
If this table helped you – we’re glad, and we hope that you will use this gained access to your device to set a hundred-proof long password that includes many types of symbols, just as all websites suggest. Besides, a personal password, be it even longer than a device’s default one, is much easier to memorize than the latter.
And one last piece of advice: have a good antivirus. Even if you have a device where you’ve forgotten to change a default password for a strong one, a decent security program will substantially limit the actions latitude for potential trespassers. That is because they use special IoT malware. We suggest GridinSoft Anti-Malware. It is a versatile, efficient, and economically beneficial solution. You can conduct your research, but may our review of this program be its part.