Bitdefender experts have discovered a new Dark Nexus IoT botnet that is designed for on attacks Dasan Zhone, DLink and ASUS routers, as well as video recorders, cameras and other devices.
The botnet was detected three months ago, and currently it includes at least 1372 devices located in China, South Korea, Thailand, Brazil, and Russia, and often acting as reverse proxies.Although Dark Nexus has a lot in common with other botnets of this kind, features of some of its modules makes Dark Nexus more powerful and reliable than its competitors. For example, payloads are compiled for 12 different CPU architectures and dynamically delivered depending on the configuration of the victim,” – write the researchers.
Can be noted similarities between Dark Nexus and the Qbot banker and the Mirai malware (which recently made a fuss about ZyXel devices). During startup, the malware uses the same processes as Qbot, and later communicates with port 7630 like Mirai), Bitdefender researchers write that the main functions and modules of the malware are still “mostly original” and receive regular updates.
So, for the period from December 2019 to March 2020, were released more than 30 versions of Dark Nexus (versions 4.0 to 8.6).
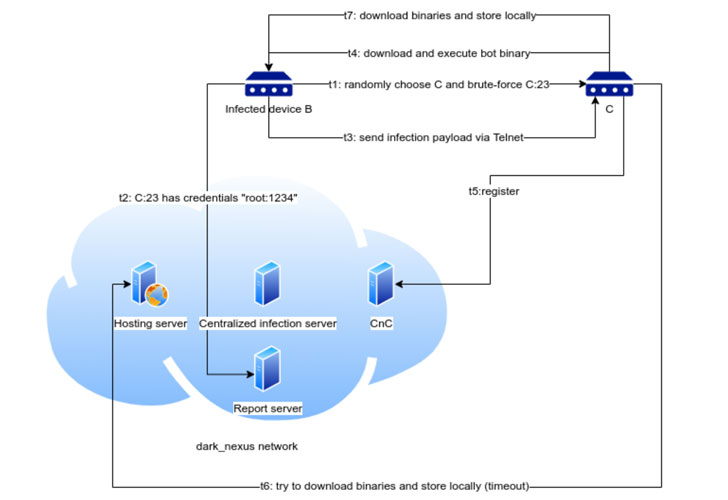
To compromise the device after detection, the botnet uses both ready-made credential lists and exploits. Two modules are used for this, one synchronous and one asynchronous, but both are trying to exploit Telnet and pre-compiled lists of credentials.
To gain a foothold on the device, Dark Nexus uses a rather interesting, according to researchers, approach: based on a list of processes, the malware performs a kind of risk assessment. So, the malicious code contains a white list of processes, including their identifiers, and based on this, Dark Nexus decides which processes are normal and which should be immediately stopped.
The attacks that carry out botnets are generally quite typical, with the exception of one command: browser_http_req. Bitdefender analysts write that this is a complex and customizable element, which is engaged in “masking traffic as harmless, similar to those that the browser could generate.”
Some versions of the malware have socks5 proxies, which has already been seen in botnets built on the basis of Mirai, TheMoon and Gwmndy. Probably, in the future, Dark Nexus operator plans to sell access to these proxies, but so far experts have not found such offers”, – noted Bitdefender experts.
The data collected by Bitdefender indicates that the developer of this malware is someone named greek.Helios. He offers his DDoS services on social networks, and advertises botnet capabilities on his own YouTube channel.
CONSIDER READING: Our recent article on how to protect an IoT device from a brute-force attack.