Google specialists talked about an unknown hacker group that exploited at least 11 zero-day vulnerabilities in 2020, targeting Android, iOS and Windows users.
The group’s attacks took place in February and October 2020. In both cases, the hackers used a watering hole attack technique. Such attacks are named by analogy with the tactics of predators that hunt at a watering hole, waiting for prey – animals that have come to drink. This term refers to attacks in which cybercriminals inject malicious code onto legitimate sites, where it waits for victims.In all cases, watering hole sites redirected visitors to a sophisticated attacker infrastructure that used different exploits, depending on the victim’s devices and browsers. And if in February two hacker servers attacked only devices running Windows and Android, then in subsequent attacks, vulnerabilities in iOS were already involved. Principle of its work is shown in the diagram below.
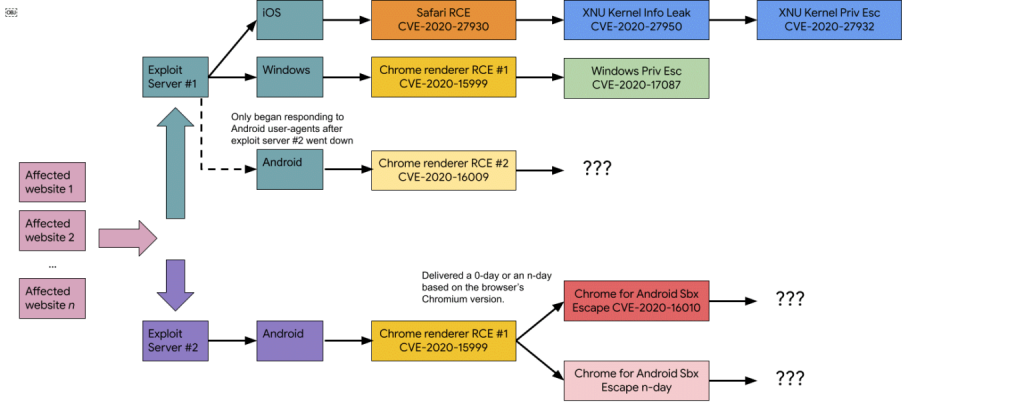
The hackers’ exploit servers used a chain of vulnerabilities that allowed them to penetrate the victim’s device, escape the browser sandbox, and then escalate privileges and gain a foothold in the system. At the same time, attackers did not always rely solely on 0-day vulnerabilities, combining such bugs with older and known problems, for which patches already exist.
As part of the February campaign, hackers used the following 0-day:
- CVE-2020-6418 – Chrome TurboFan vulnerability (fixed in February 2020);
- CVE-2020-0938 – Windows Font Vulnerability (Fixed April 2020);
- CVE-2020-1020 – Windows Font Vulnerability (Fixed April 2020);
- CVE-2020-1027 – Windows CSRSS Vulnerability (Fixed April 2020).
As part of the October campaign, there are more zero-day vulnerabilities:
- CVE-2020-15999 – Chrome Freetype heap buffer overflow (fixed October 2020)
- CVE-2020-17087 – cng.sys heap buffer overflow (fixed November 2020)
- CVE-2020-16009 – TurboFan type confusion bug (fixed in November 2020)
- CVE-2020-16010 – Chrome for Android heap buffer overflow (fixed November 2020)
- CVE-2020-27930 – Read / Write Safari Arbitrary Stack Using Type 1 Fonts (Revised November 2020)
- CVE-2020-27950 — iOS XNU Kernel Memory Exposure (revised November 2020)
- CVE-2020-27932– type confusion error in iOS kernel (fixed in November 2020).
Thus, the researchers were able to discover a complete chain of vulnerabilities targeting the fully patched Windows 10 and Google Chrome; two partial chains of vulnerabilities targeting two fully patched Android devices running Android 10 using Google Chrome and the Samsung browser; RCE exploits for iOS 11-13 and privilege escalation exploits for iOS 13.
So far, Google analysts have not released any details about the hack group responsible for these attacks. That is, it could be the work of both “government” hackers of a certain country, or the work of a certain private company.
Let me remind you that I also talked about the fact that Hackers made a mistake and Google indexed stolen credentials.
