Check Point and Otorio analysts discovered that an unnamed hack group accidentally left their catch in the public domain, and Google indexed the stolen credentials.
The[.dropcap] phishing campaign by an unnamed hack group has been active for over six months and uses dozens of domains that host phishing pages. These pages receive regular updates to make fraudulent Microsoft Office 365 sign-in requests appear as realistic as possible.The scheme was simple: hackers sent phishing emails to potential victims, allegedly from Xerox devices, which notified them of scanning an HTML document.
If to open such attachments, can be seen only a blurry image with a fake Microsoft Office 365 login form superimposed on it. Moreover, the username field is already filled in with the victim’s email address.
When a user fell for a scammer, JavaScript running in the background validated their credentials, sent the information to the hacker’s server, and then redirected the user to the real Office 365 sign-in page.
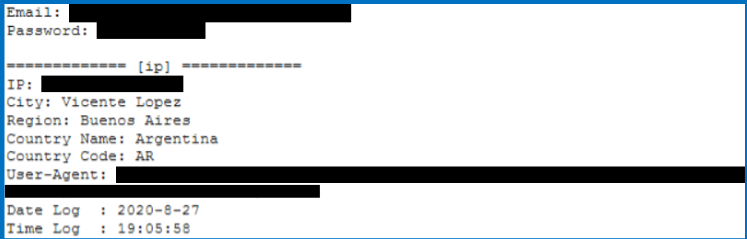
The cybercriminals got through only with the storage of stolen data. The fact is that hackers forwarded the collected information to domains specially registered for this task. However, the credentials were placed in a public file, which was eventually indexed by Google.
As a result, a search for stolen email addresses or passwords returned results as in the screenshot below.
It is also noted that the attackers hacked into WordPress servers, where they hosted malicious PHP pages for their victims.
After examining about 500 records, the researchers determined that building companies, and enterprises in the energy and IT sectors were most often the victims of phishing attacks by this group.
Let me remind you that we also talked about the fact that Mimecast, an international cloud-based email management company for Microsoft Exchange and Microsoft Office 365, said hackers had stolen a digital certificate provided to customers to securely connect Microsoft 365 Exchange accounts to Mimecast services.