Check Point experts have discovered a new campaign by the Chinese hack group Tropic Trooper, which uses a new Nimbda downloader and a new variant of the Yahoyah trojan – which is hidden in a tool called SMS Bomber, designed for attackers-beginners.
Let me remind you that we also wrote that Chinese hack group APT10 attacks Taiwanese financial sector, and also that Chinese hackers attacked Ragnarok Online Developers.SMS Bomber, as the name implies, allows entering a phone number to bombard its owner with messages and potentially disable the device by performing a Denial of Service (DoS) attack. Usually such ready-made tools are intended for script-kiddies who want to attack someone, but they lack their own skills.
The attack on the unfortunate script-kiddie begins with downloading a malicious version of SMS Bomber (in Chinese), which contains not only the SMS bombing program itself, but also additional code that injects notepad.exe into the process.
The Check Point report states that the downloaded executable is actually a Nimbda loader, which has the forethought to use the SMS Bomber icon and even SMS Bomber itself as an embedded executable.
The loader injects shellcode into the notepad.exe process to access a GitHub or Gitee repository, get the obfuscated executable, decode it, and then run it using the dllhost.exe process.
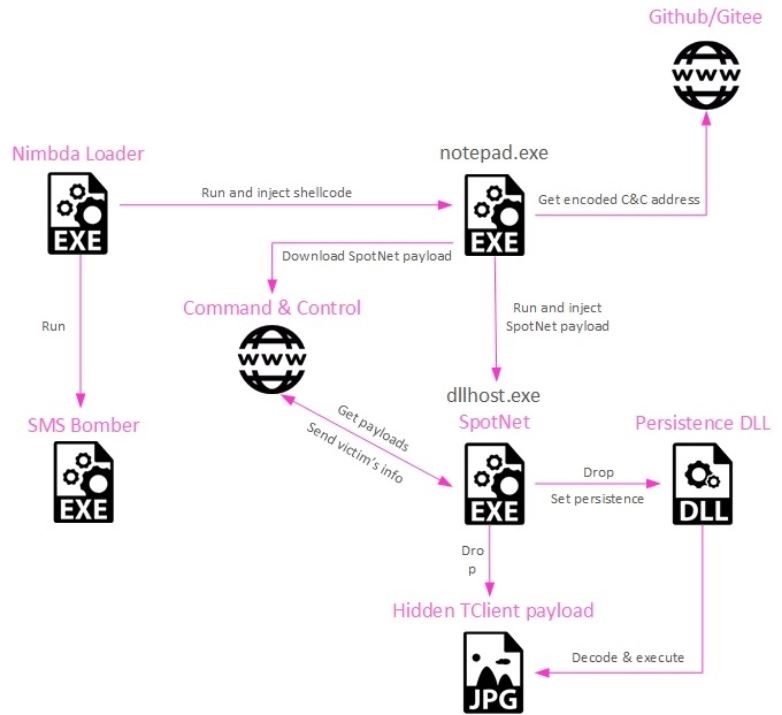
The payload is a new variant of the Yahoyah malware that collects host data and sends it to the command-and-control server. Information collected by Yahoo includes:
- SSID of the local wireless network;
- computer name;
- MAC address;
- OS version;
- information about installed anti-virus products;
- information about the presence of WeChat and Tencent files.
The final payload unfolded by Yahoyah is encoded into a JPG image using steganography. Check Point identifies this threat as TClient, a well-known Tropic Trooper backdoor that has been previously used by hackers in other campaigns.
Tropic Trooper, also known as Earth Centaur, KeyBoy and Pirate Panda, is known for its attacks on various targets in Taiwan, Hong Kong and the Philippines. The most common victims of these espionage attackers are government organizations, healthcare, transportation and high-tech industries.
The researchers write that the use of such an unusual tool as SMS Bomber for this campaign speaks of its narrow and very unusual focus. The choice of hackers is likely based on some data collected during previous spy campaigns.
