The universal decryption key of REvil, which was at the disposal of the Kaseya company, whose clients have recently suffered from ransomware attacks, appeared on a Russian-language hacker forum.
Let me remind you that in early July, customers of the MSP solution provider Kaseya suffered from a large-scale attack by the ransomware REvil (Sodinokibi). Then the hackers used 0-day vulnerabilities in the company’s product (VSA) and through it attacked Kaseya’s customers. Currently, patches have already been released for these vulnerabilities.The main problem was that most of the affected VSA servers were used by MSP providers, companies that manage other customers’ infrastructure. This means that the cybercriminals have deployed the ransomware in thousands of corporate networks. According to official figures, the compromise affected about 60 Kaseya clients, through whose infrastructure hackers could encrypt approximately 800-1500 corporate networks.
After this attack, the REvil operators demanded a ransom of $ 70 million and then promised to publish a universal decryptor that can unlock all computers. However, the group soon “lowered the bar” to $50 million.
However, the hacker group completely “disappeared from the radar“, and the sites and the entire infrastructure of the REvil ransomware as a whole went offline without explanation. We are talking about a whole network of conventional and darknet sites used to negotiate a ransom, leaking data stolen from victims, and the internal infrastructure of the ransomware. From July 13, 2021, all of them, for some reason, do not work.
The appearance of the master key was announced by Kaseya representatives at the end of July. Then the company refused to disclose where this tool for decrypting data came from, limiting it to a vague explanation “from a trusted third party.” However, the company assured that it is universal and suitable for all affected MSPs and their clients. Before sharing the tool with clients, Kaseya required them to sign a nondisclosure agreement.
Someone posted a screenshot of the master decryption key for REvil on a hacker forum. The screenshot shows the REvil decryptor displaying the base64 hashed master_sk key:
OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s=
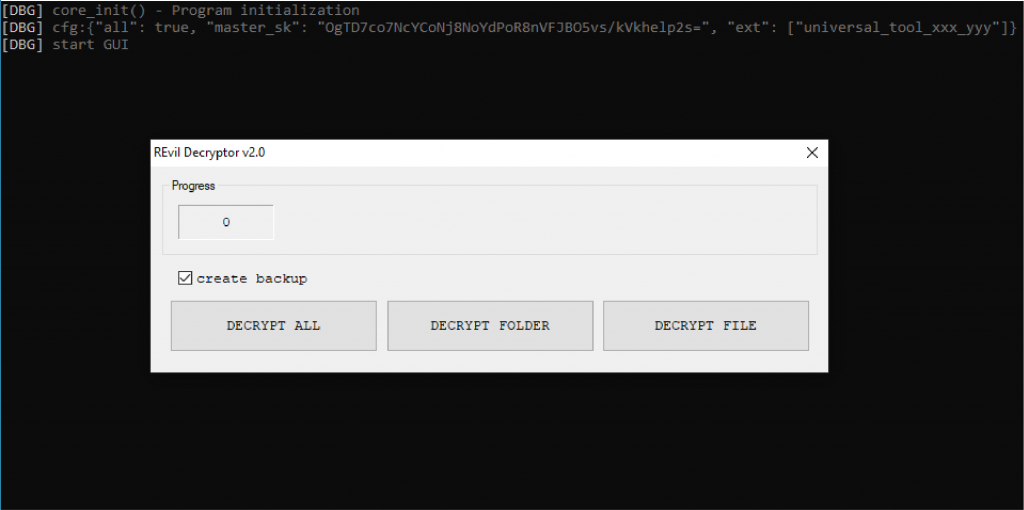
When REvil victims pay the ransom, they receive either a decryptor that works for one file extension or a universal decryptor that works for all extensions. For example, the above image shows a generic decryptor that can decrypt all extensions associated with the attack on Kaseya clients.
While it was originally speculated that the key in the screenshot might be a master key suitable for all REvil campaigns in general, Bleeping Computer says this is not the case. The master key works but only works for Kaseya customers. The head of Emsisoft Fabian Vosar, as well as specialists from Flashpoint, writes about this on Twitter.
It is unclear why the decryptor was posted on a hacker forum, where the victims would definitely not write. However, numerous security sources told Bleeping Computer that the key was most likely published by someone associated with the REvil operators and not by one of the victims.