Bleeping Computer reports that the sites and the entire infrastructure of the ransomware REvil (Sodinokibi) as a whole went offline without explanations.
The talk is about an entire network of conventional and darknet sites that are used for negotiating ransom, leaking data stolen from victims and the internal infrastructure of the ransomware. Now they all don’t work for some reason.
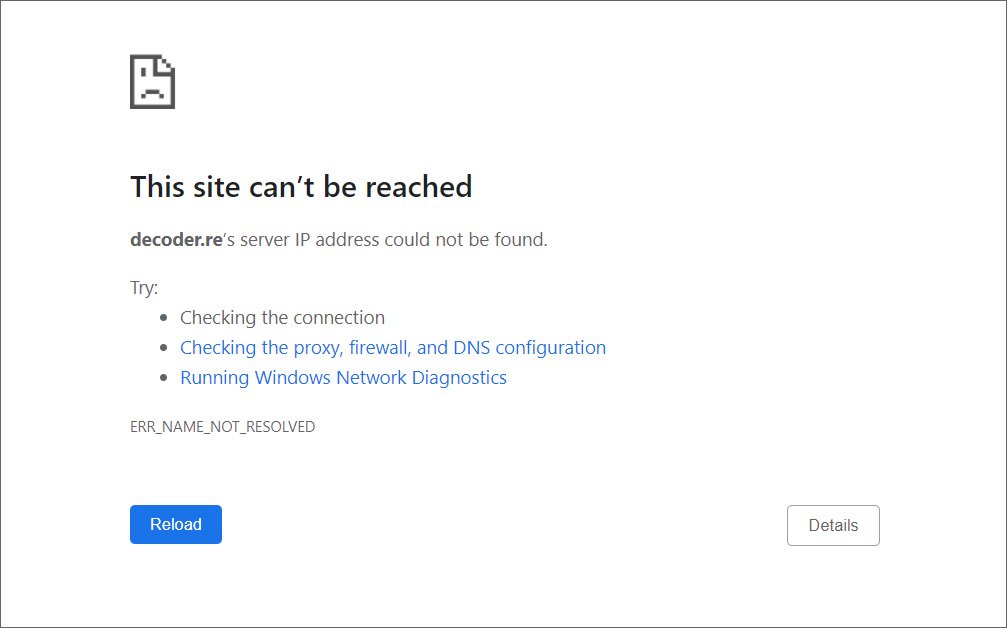
Journalists and information security experts write that a temporary “drop” of one or two resources is normal, but a complete shutdown of the entire infrastructure looks extremely strange. For example, the decoder [.] Re site is no longer resolved via DNS queries, which indicates that the entire DNS infrastructure on the backend is disabled or the domain’s DNS records are missing.
Let me remind you that in early July, REvil operators carried out a large-scale attack on the customers of the well-known MSP solution provider Kaseya. For the attack, the hackers used 0-day vulnerabilities in the company’s product (VSA).
The problem is that most of the affected VSA servers were used by MSP providers, that is, companies that manage the infrastructure of other customers. This means that the cybercriminals have deployed the ransomware in thousands of corporate networks. According to official figures, the compromise affected about 60 Kaseya clients, through whose infrastructure hackers were able to encrypt approximately 800-1500 corporate networks.
After this attack, the hackers demanded a ransom of $70 million, and then promised to publish a universal decryptor that can unlock all computers. The group soon “lowered the bar” to $50 million.
Last month, REvil also hit the front pages of many publications as it attacked JBS, the world’s largest supplier of beef and poultry, as well as the second largest producer of pork. The company operates in the USA, Australia, Canada, Great Britain and so on, serving clients from 190 countries around the world.
Since it has long been known that REvil is a Russian-speaking hack group, the other day US President Joe Biden in a telephone conversation called on Russian President Vladimir Putin to stop the attacks of ransomware hackers operating from the territory of the Russian Federation. Biden said that if Russia does not take action after that, the United States will be forced to take it on its own.
It is also worth noting that ransomware operators DarkSide and Babuk urgently stopped their activities under similar circumstances. The first group “closed” after a massive attack on the American pipeline operator Colonial Pipeline, as it attracted too much attention (including from law enforcement agencies). The second group announced it would stop working after a high-profile attack on the Washington Police Department.

