Trojan Kovter: What is the Kovter Malware?
Kovter (also known as Trojan:Win32/Kovter.C, Mal/Kovter-Z, and Trojan.Kovter) is an adware-type trojan designed to generate traffic for various websites. Research shows that Kovter is typically proliferated using malicious Microsoft Office attachments (which are distributed using spam email campaigns) and another trojan.
Kovter has an exciting feature that enhances its ability to avoid detection. Unlike most infections, Kovter is not stored in any file. Instead, cybercriminals install this malware by creating some entries in Windows Registry. In this way, they can maintain Kovter in systems without storing detectable files.
The primary purpose of Kovter is to generate traffic for various websites. It runs several Internet Explorer instances in the background. These are used to visit websites and emulate clicks on advertising links/banners. In this way, cybercriminals can generate web traffic and revenue. However, the presence of these infections can cause many issues. System performance significantly diminishes since running Internet Explorer processes uses many resources.
Furthermore, Kovter might be used to visit malicious websites and, thus, its presence can lead to system infections. Kovter can be detected in various ways. It usually runs a randomly named process in Windows task manager. You should also be able to see multiple Internet Explorer processes. Kovter’s Windows Registry entries are named using unreadable characters, and thus the default Registry Editor cannot display them correctly. Fortunately, anti-virus/anti-spyware suites can detect such infections and eliminate them. Therefore, if you have noticed any of the symptoms mentioned earlier, immediately run a full system scan and eliminate all detected threats.
How did Kovter infect my computer?
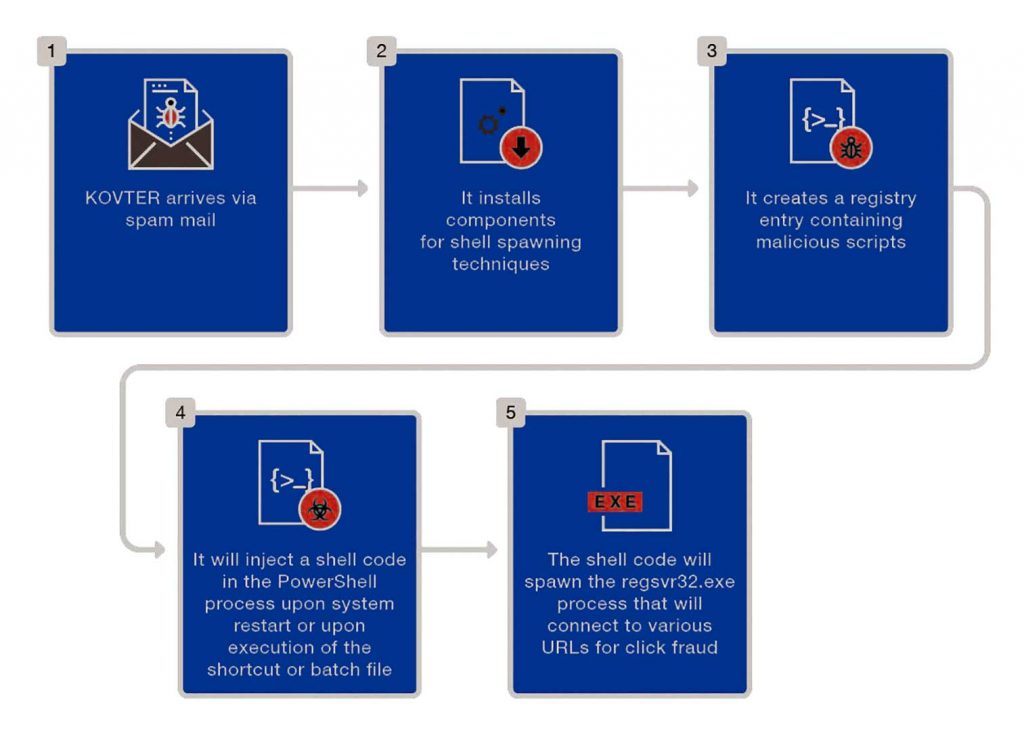
One of the most common infection methods for KOVTER is via attachments coming from macro-based malicious spam. Once the malicious attachment (usually compromised Microsoft Office files) is clicked, the malware installs a shortcut file, batch file, and a random file with a random file extension in a randomly named folder usually located in %Application Data% or %AppDataLocal%. Registry entries based on the random file extension are also installed in Classes Root to direct the execution of the arbitrary file into reading a registry entry. These components are used to perform the malware’s shell-spawning technique.
For the next part, the registry entry for the random file is created, containing malicious scripts that perform KOVTER’s processes. This means that the moment the infected machine restarts or either the shortcut or batch files are triggered, the malicious script in the registry entry is loaded into memory. The malicious script contains a shellcode that the malware injects into the PowerShell process. The shellcode will then decrypt a registry entry located in the same registry key. This registry entry is a binary file injected into a spawned process (usually regsvr32.exe). The spawned regsvr32.exe would then try to connect various URLs as a part of its click fraud activity.
Upon installation of all these file components and registry entries, the malware spawns a watchdog process that continuously monitors the existence of these components.

![What is the Win32:Evo-gen [Trj] virus?](https://howtofix.guide/wp-content/uploads/2019/11/trojan-ransom-1200x500.jpg)