ZDNet, citing an unnamed cybersecurity researcher, reports that more than 85,000 SQL DBs for sale on the darknet, priced at around $550 apiece.
The site on which the sale is being made, is a part of a large ransomware scheme, and in operation since the beginning of 2020. Complaints about such database attacks can be found on Reddit, MySQL forums, support forums, Medium blogs, and private blogs.For example, hackers break into SQL databases, download them, delete the originals, and leave ransom notes to the owners if they want their data back.
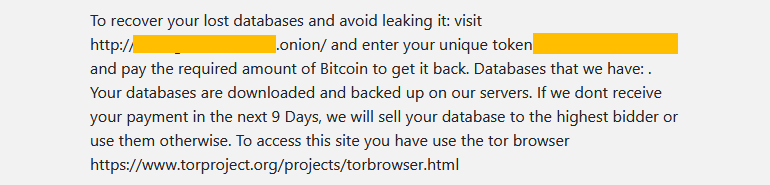
While the victims were initially offered to contact the attackers by email, over time, the hackers changed their tactics and automated their scheme using a site that was first hosted on sqldb.to and dbrestore.to, and then moved to the darknet.
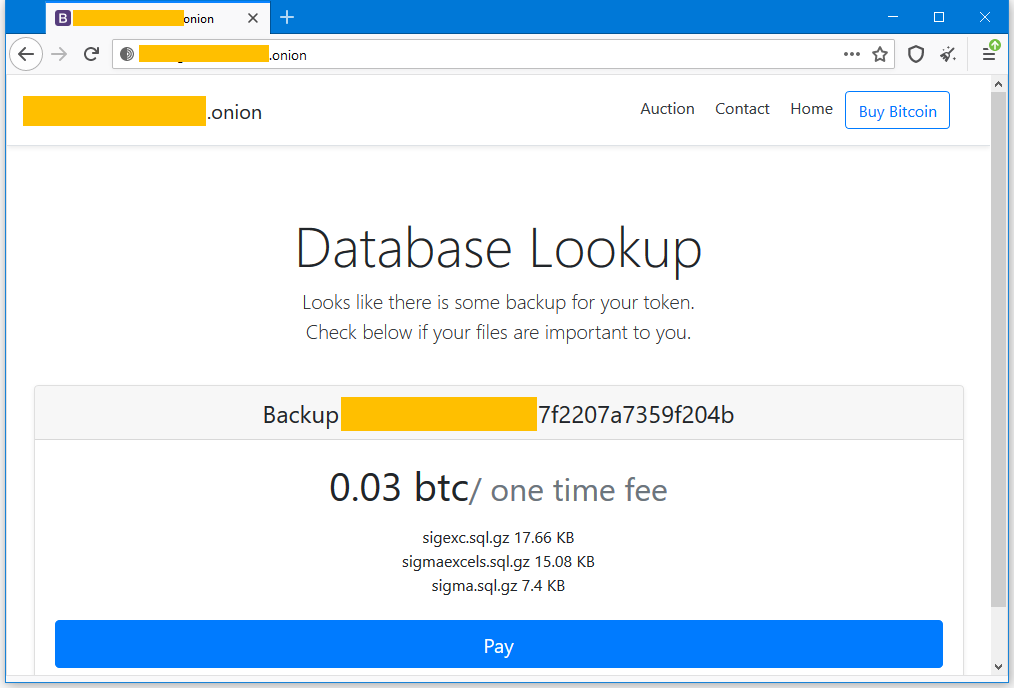
On the website, victims are asked to enter a unique identifier specified in the ransom note, after which the victim is taken to a page where his data is sold.
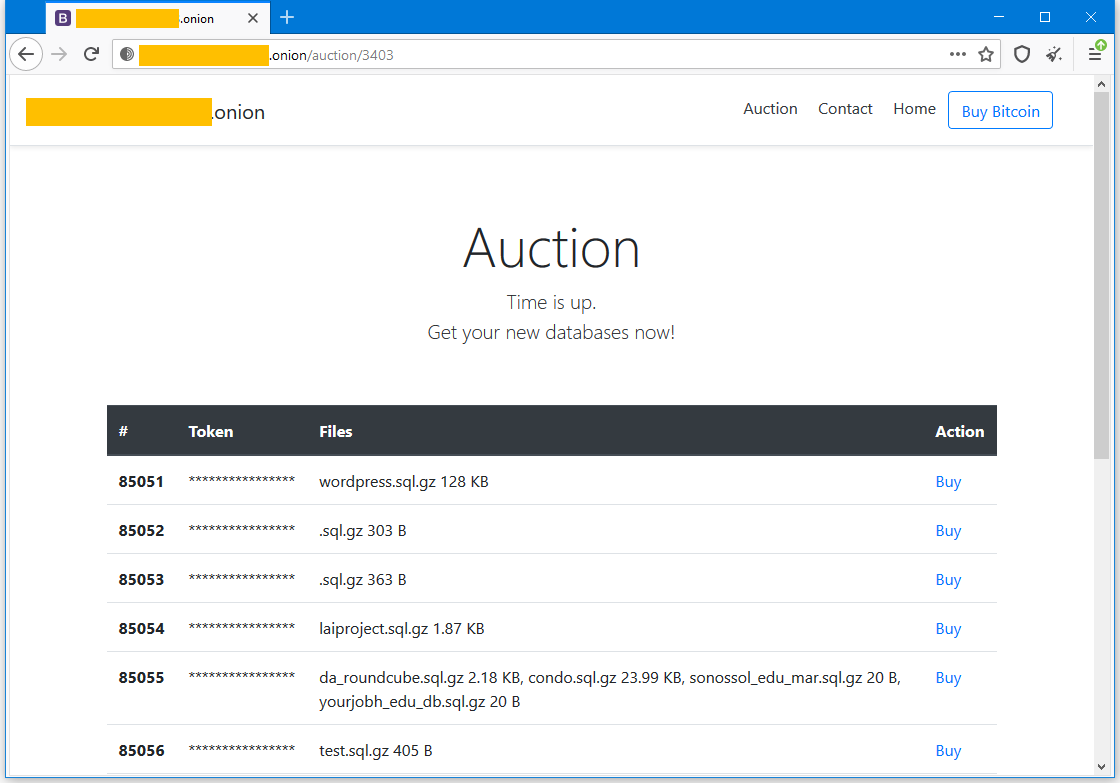
If victims do not pay within nine days, their data is put up for public sale, for auction in another section of the site.
The cost of restoring or buying a stolen database can vary slightly, as the bitcoin / dollar exchange rate often fluctuates. Typically, the ransom is about $ 500 in crypto, regardless of the content from the database and the affected site.
The Bitcoin addresses used by the groups are gradually accumulating on the BitcoinAbuse.com site. It is noted that the attacks of this group are easily recognizable, because usually hackers accompany their ransom demands with the heading “WARNING”.
Apparently, most of the databases compromised by cybercriminals originate from MySQL servers, but it cannot be ruled out that other systems, including PostgreSQL and MSSQL, could be affected.
Let me remind you that we talked about hackers selling data of 34 million users stolen from 17 companies.
