Okta Auth0 developers have fixed an RCE vulnerability in the popular open source JsonWebToken library, which is used in 22,000 projects (including open source projects from Microsoft, Twilio, Salesforce, Intuit, Box, IBM, Docusign, Slack and SAP) and has more than 36 million downloads per month for NPM.
The latest vulnerability has received the identifier CVE-2022-23529 (CVSS score of 7.6) and affects all versions of JsonWebToken below 9.0.0 (that is, released before December 21, 2022).Let me remind you that we also wrote that 17 malicious npm packages stole Discord tokens, and also that the PyPI repository got rid of 11 packages that were stealing Discord tokens and passwords.
And also information security experts reported that Researcher compromised 35 companies through a new “dependency confusion” attack.
It is reported that the successful operation of CVE-2022-23529 allows you to bypass authentication mechanisms, gain access to confidential information, and also allows you to steal or change data.
The problem was discovered by Palo Alto Networks specialists in the summer of 2022, and they immediately notified the developers about it. Then the experts noticed that attackers can remotely execute code using JsonWebToken after verifying a malicious JWS token.
As the experts of the Unit 42 team said, the problem that allowed this to happen was related to the verify() method, which is used in the JsonWebToken to validate the JWT and return the decrypted information. This method took three parameters: token, secretOrPublicKey and options.
Lacking a proper check on the secretOrPublicKey parameter to determine whether it was a string or a buffer, attackers could use specially crafted objects to randomly write files to the target machine.
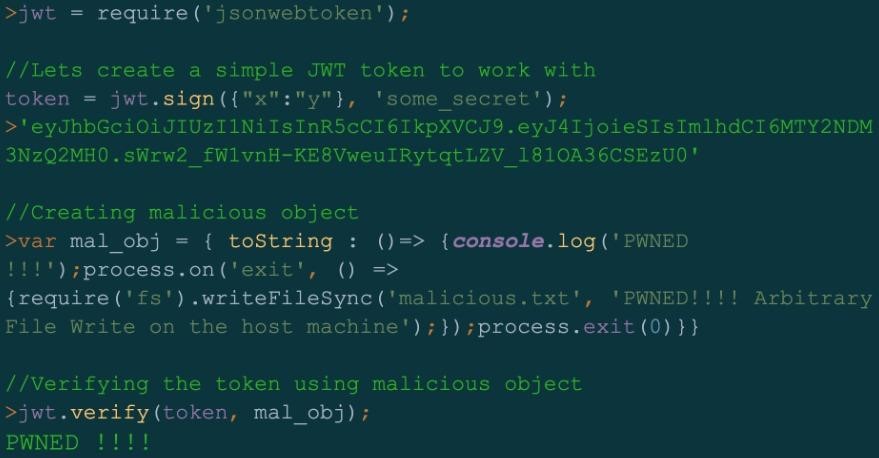
In addition, exploiting the same vulnerability with a different payload in the request could also lead to remote arbitrary code execution.
The Auth0 developers have been working on a patch since August 2022, but the patched version with JsonWebToken (9.0.0) was only released at the end of December 2022. The patch includes the implementation of additional checks for the secretOrPublicKey parameter to prevent parsing of malicious objects.
