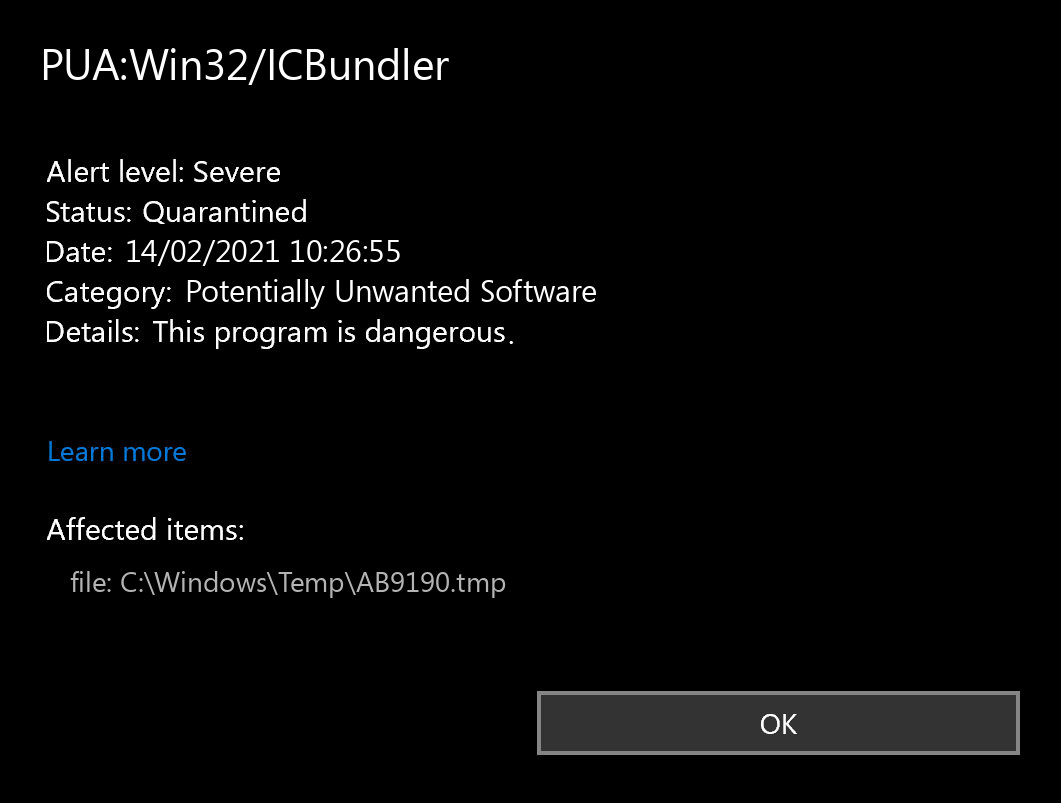
What is PUABundler:Win32/ICBundler?
PUABundler:Win32/ICBundler is a potentially unwanted application (PUA) detection used by antivirus software to identify a specific type of bundling software. It is categorized as a bundler because it bundles legitimate software installations with additional software or offers, often leading to unwanted or unexpected installations on the user’s system.
ICBundler refers to the specific bundler variant that has been identified and classified by antivirus vendors. Bundlers like PUABundler:Win32/ICBundler may be distributed through various channels, including freeware or shareware downloads, deceptive advertisements, or software bundles that lack transparency in disclosing the additional installations.
While not necessarily malicious, PUABundler:Win32/ICBundler can cause unwanted behaviors such as displaying intrusive advertisements, modifying browser settings, or collecting user data without explicit consent. It is generally recommended to exercise caution when downloading and installing software from unfamiliar sources and to carefully review the terms and conditions during installations to avoid inadvertently installing unwanted software.
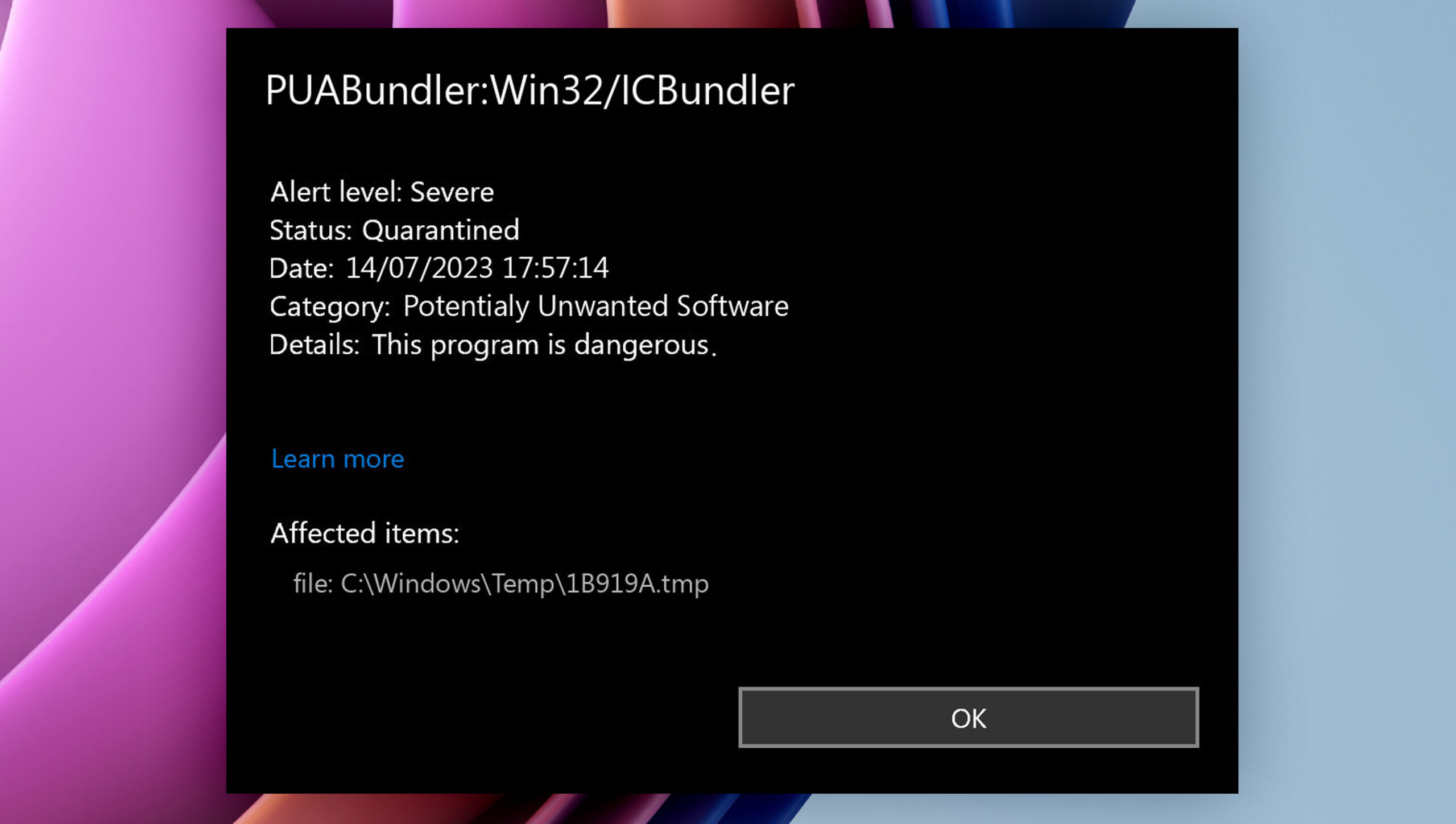
Microsoft Defender detects and flags PUABundler:Win32/ICBundler
Microsoft Defender detects and flags PUABundler:Win32/ICBundler to alert users about the potential risks associated with this type of bundling software, allowing them to make informed decisions and take appropriate actions to protect their systems.
Using reputable antivirus or anti-malware software can also help detect and block installations of potentially unwanted programs like ICBundler. Regular system scans and keeping your security software up to date are crucial for maintaining a secure and clean system.
ICBundler is a detection for BitTorrent
When you have a BitTorrent app installed on your computer, Microsoft Defender may detect PUABundler:Win32/ICBundler. BitTorrent is a client for peer-to-peer networking, allowing you to obtain various files from other computers over the internet by connecting to their IP addresses. P2P networks are frequently exploited for distributing viruses, which is why Defender identifies it and suggests blocking the “threat.”
It’s important to note that servers and IP addresses are often shared by multiple websites. While the files you download through BitTorrent may be safe, some of the sites hosted on the IP addresses connected to by BitTorrent could be malicious. Nevertheless, it’s crucial to understand that BitTorrent itself is not a threat.
File sharing involves utilizing technology that enables internet users to share files stored on their individual computers. Peer-to-peer (P2P) applications, such as those used for sharing music files, are among the most common types of file-sharing technology. However, P2P applications introduce security risks that can potentially endanger your PC.
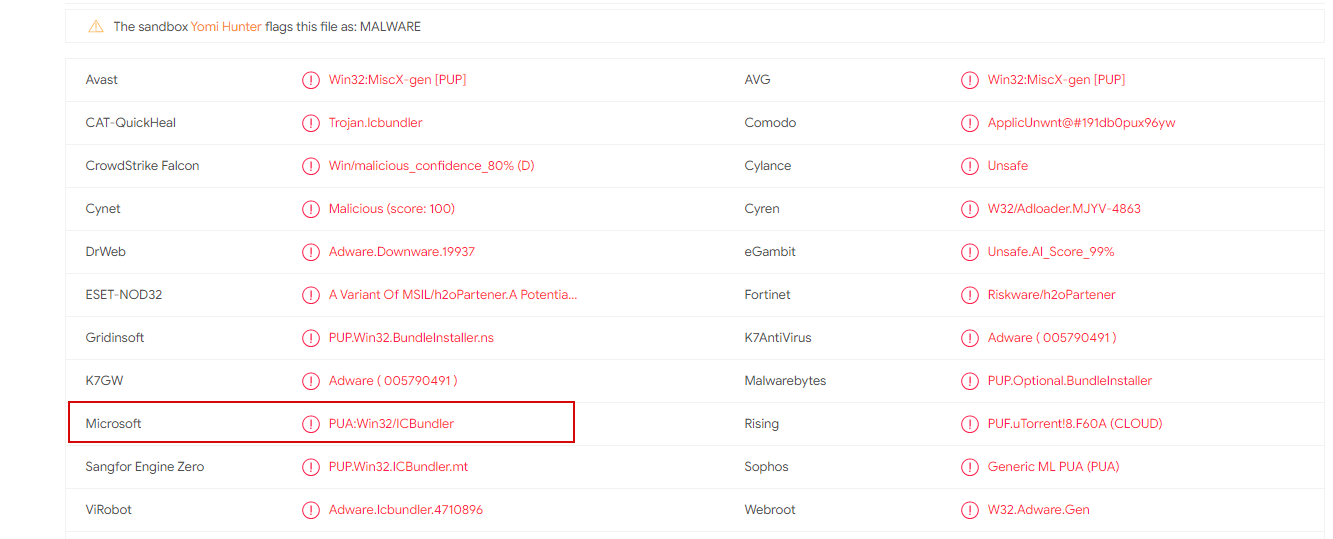
Microsoft Defender & PUABundler:Win32/ICBundler
If you have seen a message suggesting the “PUABundler:Win32/ICBundler found”, you have nothing to worry about. BitTorrent application cannot inject a virus of any sort into your computer. Such messages just alarm you that further usage of the BitTorrent app may be dangerous. And these words are not just rumors – a lot of ransomware attack cases in 2020 happened exactly after the use of malevolent P2P seeding.
There are several ways to terminate that risk. You can either delete the BitTorrent, or ignore that notification, but both of these ways will not guarantee you safety. Virus distributors are extremely sly, so it is important to secure your PC from any kind of attack. Microsoft Defender is not a thing you can rely on. That program is integrated into the system and can be stopped through the Group Policies in several clicks. Malware creators exploit that security breach heavily, hence, you will not be able to scan your device and remove the threats after the attack. To guarantee that PUABundler:Win32/ICBundler will not turn in something serious, and to provide you with invulnerable antivirus protection, you can use GridinSoft Anti-Malware.
How to scan for malware, spyware, ransomware, adware, and other threats.
If your computer exhibits exceptional slowness, the website opens peculiarly, or if you encounter unexpected advertisements, it is possible that PUABundler:Win32/ICBundler is more than just a daunting notification. The range of viruses you can acquire is extensive, and their symptoms are even more varied. Spyware will undoubtedly track all your activities or redirect your searches and web pages to unwanted destinations. Adware may infect your browser and the entire operating system, bombarding you with intrusive banners.
Regardless of the type of issue you are experiencing with your PC, the initial step is to examine it using Gridinsoft Anti-Malware. This highly effective tool is designed to detect and eradicate threats from your PC. However, it is not just a simple antivirus software application. Its mission is to combat modern threats. It is the only product in the market capable of cleansing your PC from spyware and other viruses that go undetected by regular antivirus programs. Download, install, and execute Gridinsoft Anti-Malware, and then perform a thorough scan of your PC. The software will expertly guide you through the system cleaning process.
How to scan your PC for viruses like ICBundler?
The main sign of malware injection, which you can spectate on your device, is the general slowdown. Malware activity can consume a lot of hardware capacity, especially if we are talking about coin miners. You must not ignore these signs, because, as I have mentioned before, the efficiency of malware depends on the time you give it for actions. Forehanded detection of malicious items is also the way to prevent the appearance of various other viruses.
Regardless of the exact symptoms, you need to scan your device with the proper anti-malware software. Besides the aforementioned disadvantages, Microsoft Defender also has a problem with database updates. That antivirus tool cannot update its detections as other tools do. To apply the new databases, you need to install all past detection database updates and get the newest ones, performing several reboots in the process. Because of such a long update cycle, Defender cannot provide the proper scanning functionality. GridinSoft Anti-Malware can detect viruses at any moment since its detection lists are updated every hour.
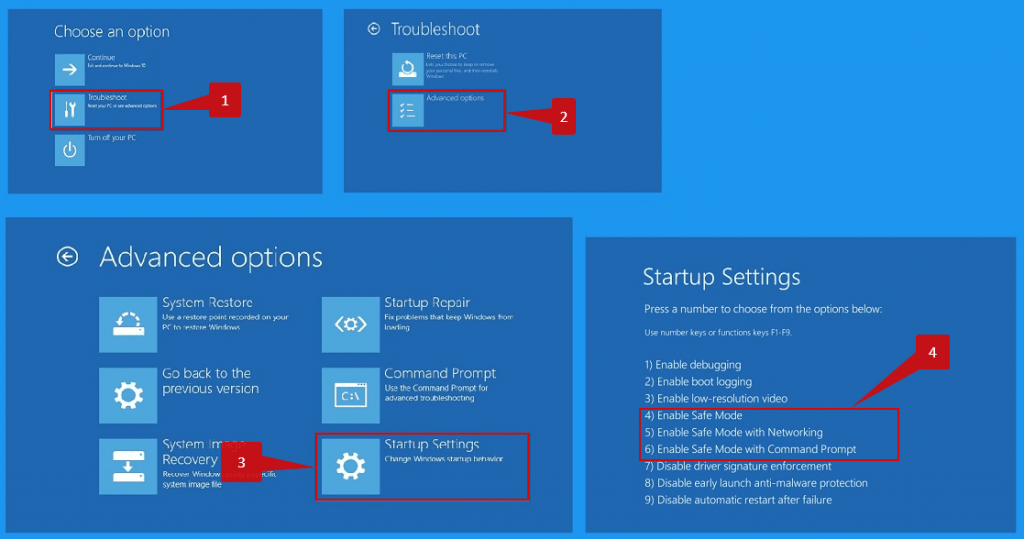
Use Safe Mode to prevent the virus launching.
If the PUABundler:Win32/ICBundler leads to severe malware installation, you need to avoid its launching before using any removal guides. For this objective, you need to start Windows in Safe Mode, thus avoiding the system from loading auto-startup items. The primary target for such a restriction is malware. Scan your system with Gridinsoft in Safe Mode. This will certainly aid you in discovering viruses that can not be tracked in the regular mode.
Remove PUABundler:Win32/ICBundler with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common PUAs as shown from our tests with the software, and we assure you that it can remove PUABundler:Win32/ICBundler as well as other malware hiding on your computer.
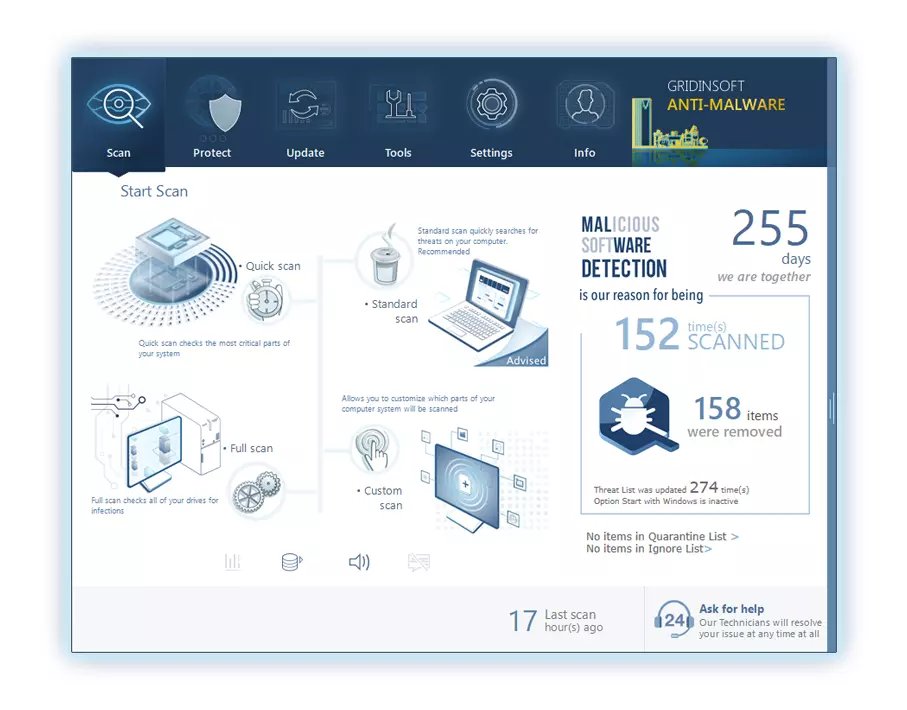
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
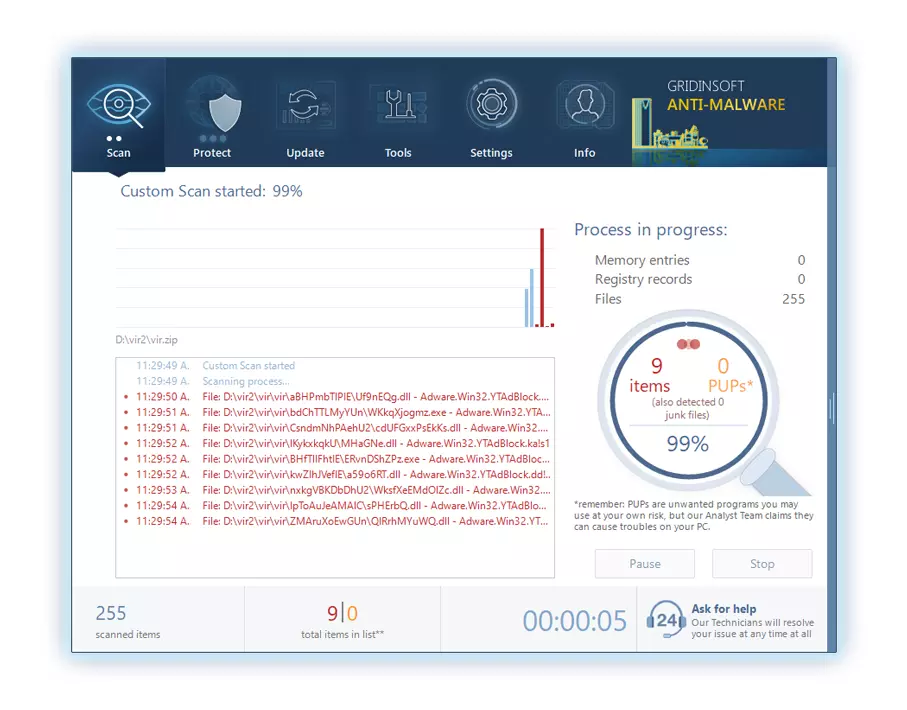
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
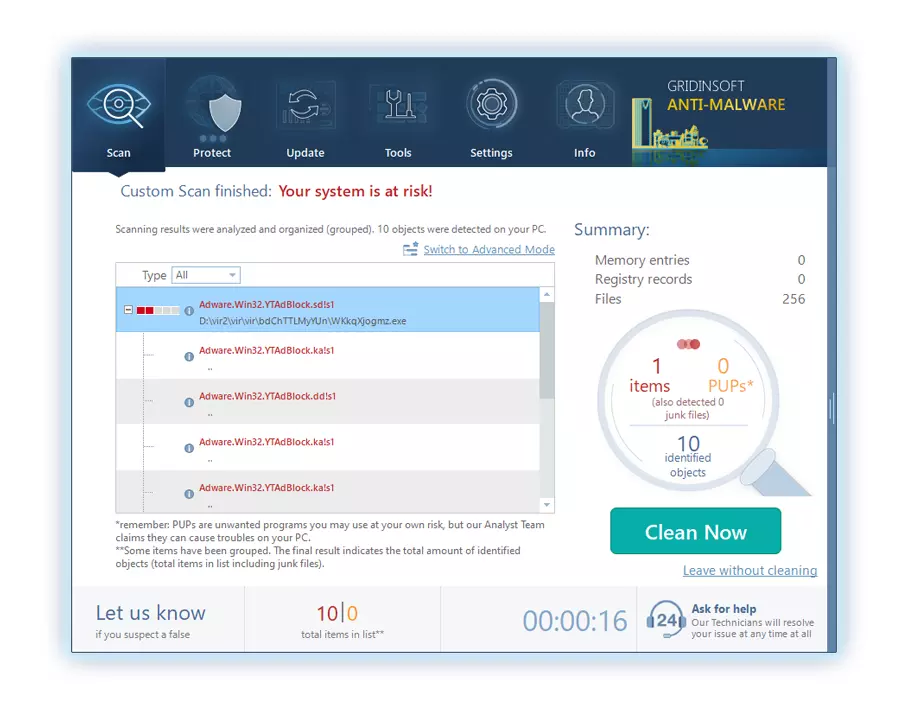
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
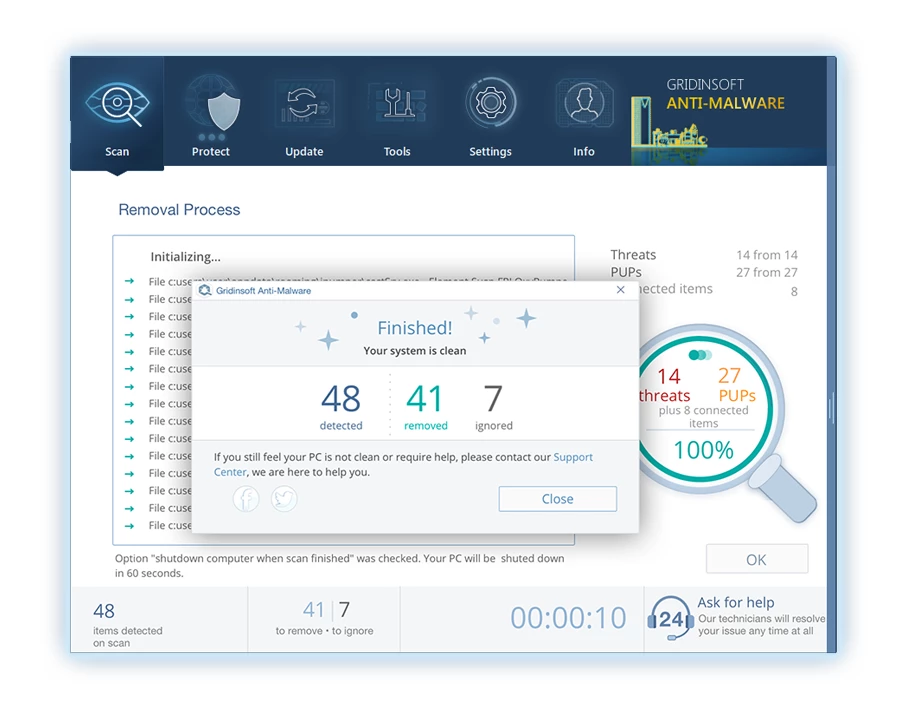
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “PUABundler:Win32/ICBundler” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
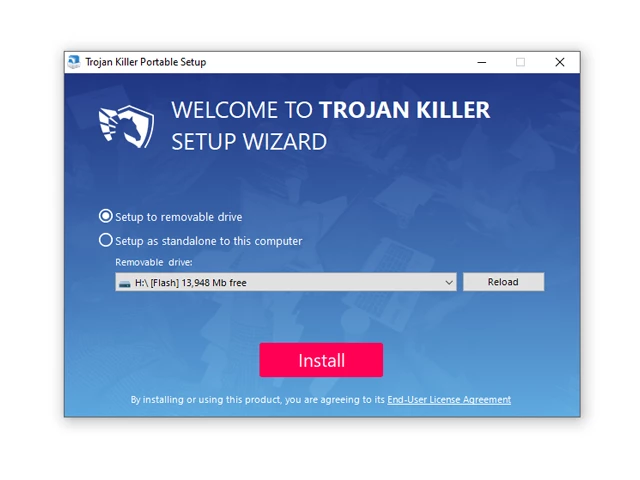
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
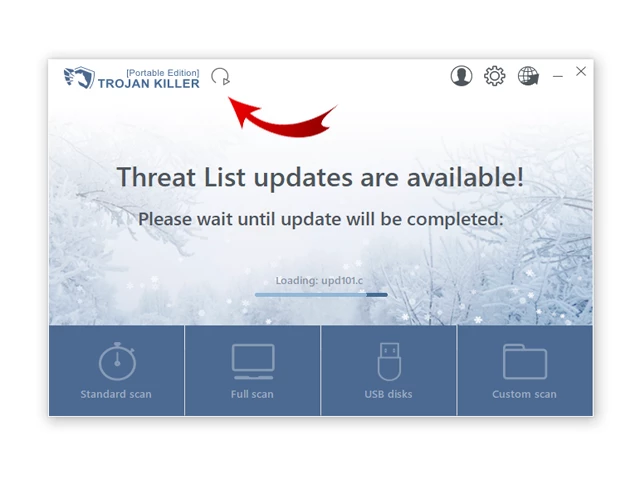
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
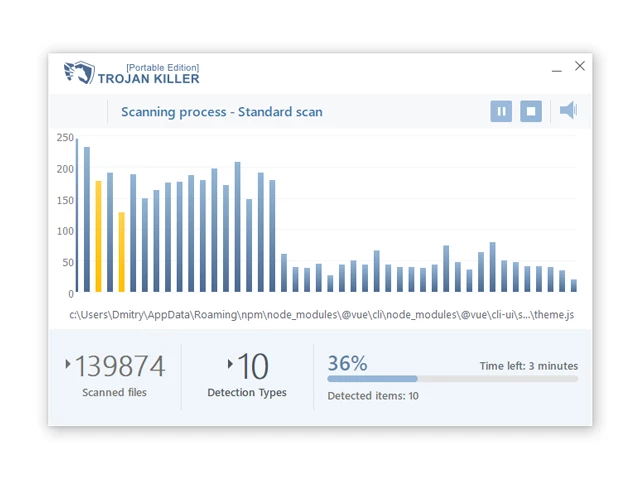
Step 4: Remove Found Threats:
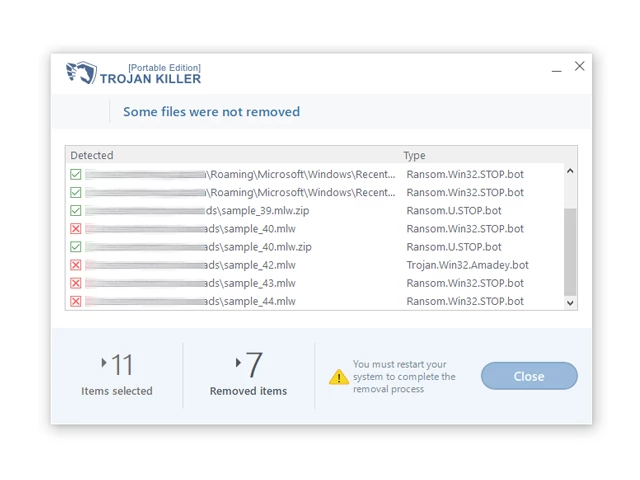
12. After the scan is complete, Trojan Killer will display a list of detected threats.
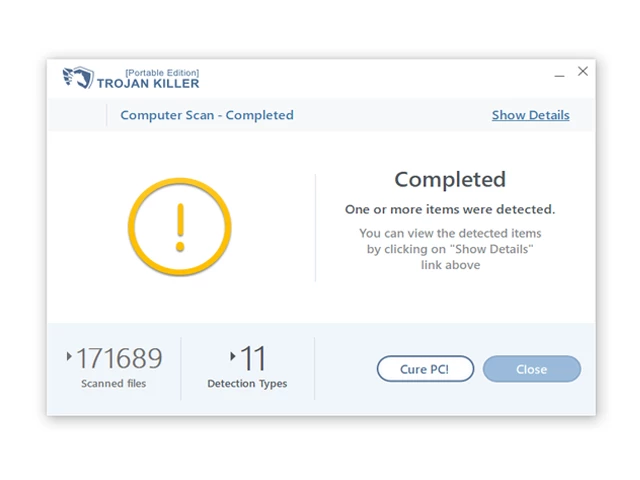
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing PUABundler:Win32/ICBundler and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
It’s not enough to use the antivirus for the security of your computer. It would help if you had much more extensive antivirus software. Not all malware can be detected by regular antivirus scanners that mainly look for virus-type dangers. Your system may teem with “trash”, for instance, toolbars, browser plugins, unwanted online search engines, bitcoin-miners, as well as various other sorts of unwanted software used for earning money on your inexperience. Beware while downloading and installing apps online to stop your tool from being filled with unwanted toolbars and various other junk applications.
However, if your system has already obtained a certain unwanted application, you will make up your mind to erase it. The majority of the antivirus programs are uncommitted regarding PUAs (potentially unwanted applications). To get rid of such programs, I suggest acquiring Gridinsoft Anti-Malware. If you use it regularly to scan your PC, it will certainly help you eliminate malware that was missed out on by your antivirus software.
Frequently Asked Questions
ICBundler is a detection name used by antivirus software to identify a potentially unwanted application associated with bundled software packages.
ICBundler refers to an installer or setup file that includes additional software or components that may be unwanted or potentially harmful.
It is not necessarily malicious, but it may include potentially unwanted programs (PUPs) or adware alongside the intended software.
It can be installed when downloading software from untrusted or unreliable sources that include bundled applications.
ICBundler can result in unwanted software being installed on your system, potentially leading to excessive advertisements, data collection, or unwanted modifications to your browser settings.
To prevent PUABundler:Win32/ICBundler and similar bundled applications, download software from trusted sources, carefully review installation prompts, and use reputable antivirus software to scan and remove any detected threats or potentially unwanted programs.
You can remove ICBundler by using reputable antivirus software to scan and remove any detected threats or potentially unwanted programs. Additionally, uninstalling any unwanted software through the Control Panel can help eliminate bundled applications.
It is recommended to exercise caution when using software that triggers PUABundler:Win32/ICBundler detection, as it may include potentially unwanted or harmful components. Consider using alternative software from trusted sources to ensure the security and integrity of your system.
If the guide doesn’t help you to remove PUABundler:Win32/ICBundler virus, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments to get help.
I need your help to share this article.
It is your turn to help other people. I have written this guide to help users like you. You can use the buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Daniel ZimmermanHow to Remove PUABundler:Win32/ICBundler Malware
Name: PUABundler:Win32/ICBundler
Description: ICBundler is a specific bundler that is known for including potentially unwanted programs (PUPs) or adware alongside the intended software. These bundled applications may display excessive advertisements, collect user data without consent, or modify browser settings to redirect web traffic. While not necessarily malicious, PUABundler:Win32/ICBundler is flagged because it can result in unwanted software being installed on the user's system without their explicit knowledge or consent. Users should exercise caution when downloading and installing software, paying attention to the installation process and opting for custom or advanced installation options to review and deselect any unwanted bundled applications.
Operating System: Windows
Application Category: Potentially Unwanted Software
User Review
( votes)