The malware named NightClub possesses spyware and data-stealing capabilities. This program has at least four versions, with the earliest variant dating back to 2014.
A threat actor known as MoustachedBouncer utilizes the NightClub malware. This group has existed for nearly a decade and primarily targets foreign embassies in Belarus. The embassies of four countries have been subject to known attacks – two in Europe and one each in Africa and South Asia. Besides NightClub, this threat actor also employs another toolset referred to as Disco.
Overview of NightClub Malware
The base version of NightClub has two primary capabilities – it monitors files and exfiltrates data. Stolen content is sent to its Command and Control (C&C) server via email. Older versions were limited to downloading Microsoft Word (.doc, .docx), Microsoft Excel (.xls, .xlsx), and PDF (.pdf) documents.
However, versions from 2016 onwards have the ability to retrieve additional malicious modules from the C&C server. While theoretically capable of various types of infection, in practice, this software tends to operate within certain limitations.
Since 2020, NightClub attacks have incorporated a backdoor module, along with modules for keylogging (recording keystrokes/typed data), capturing screenshots, and recording audio through integrated or attached microphones.
The backdoor module can execute various commands, including but not limited to creating processes, copying and moving directories, and reading, moving, and removing files.
It’s important to note that malware developers frequently enhance their software and methodologies. Additionally, NightClub’s activities are linked to political and geopolitical attacks. These factors suggest that potential future NightClub campaigns may introduce different or additional functionalities and features.
| Name | NightClub Virus |
| Detection | Trojan:Win32/Malgent!MSR |
| Damage | The NightClub malware can cause extensive harm by stealing sensitive data, executing various commands, and enabling unauthorized access to compromised devices. |
| Fix Tool | See If Your System Has Been Affected by NightClub Virus |
In summary, the presence of malicious software like NightClub on devices can lead to severe privacy concerns, financial losses, and identity theft. Malware targeting highly sensitive targets poses even greater threats.
Malware in General
We have analyzed thousands of malware samples; our latest articles cover examples such as Jorik trojan, XWorm RAT, WikiLoader, RATRUN stealer, and Fruity trojan.
Malicious software can exhibit high versatility, with various functionalities combined in different ways. Regardless of its operation, the presence of malware on a system jeopardizes device integrity and user safety. Hence, it is crucial to promptly eliminate all threats upon detection.
How Did NightClub Infiltrate My Computer?
The techniques used to distribute NightClub are currently unknown. Generally, malware is spread through phishing and social engineering tactics.
Malicious programs are often disguised as or bundled with regular software/media files. These can take various formats, including archives (ZIP, RAR, etc.), executables (.exe, .run, etc.), documents (PDF, Microsoft Office, Microsoft OneNote, etc.), JavaScript, and more.
The most common distribution methods involve stealthy downloads, malicious attachments and links in spam emails/messages, questionable download sources (freeware sites, P2P networks, etc.), online scams, malvertising, illegal software activation tools, and fake updates.
Furthermore, malicious programs can self-propagate via local networks and removable storage devices (external hard drives, USB flash drives, etc.).
How to Avoid Malware Installation?
We strongly advise exercising caution with incoming emails and messages. Avoid opening attachments or links in suspicious or irrelevant emails, as they could be malicious. Be vigilant while browsing, as fraudulent online content often appears legitimate.
Download only from official and verified sources. Ensure all programs are activated and updated using genuine functions/tools, as third-party sources may contain malware.
Having a reputable antivirus installed and regularly updated is essential. Security software should conduct routine system scans to identify and eliminate threats. If you suspect your computer is infected, we recommend using Gridinsoft Anti-Malware to automatically remove infiltrated malware.
Remove NightClub with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Stealers as shown from our tests with the software, and we assure you that it can remove NightClub as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
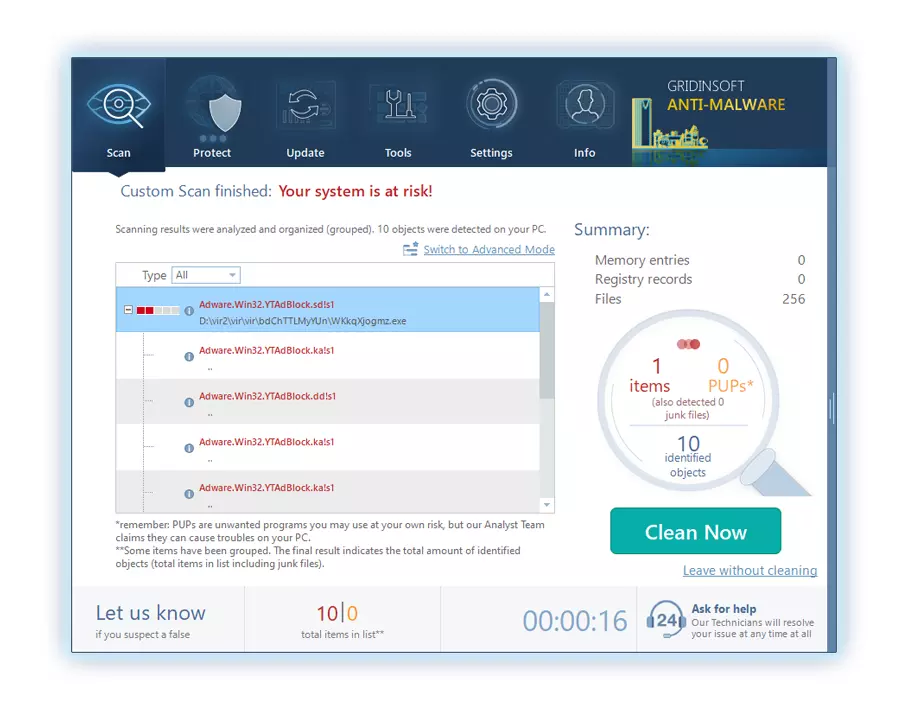
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
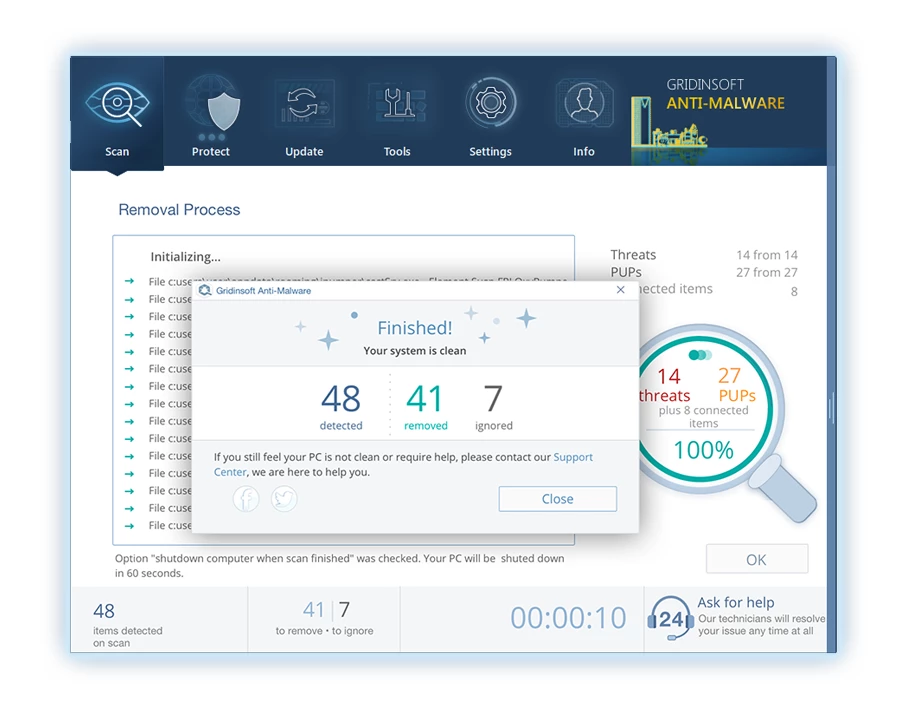
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “NightClub” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
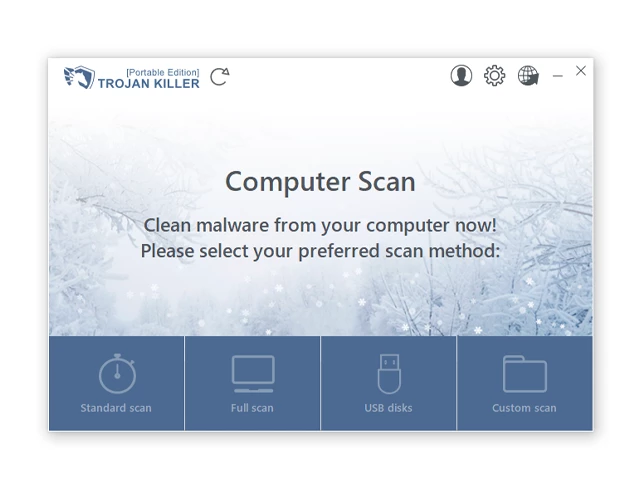
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
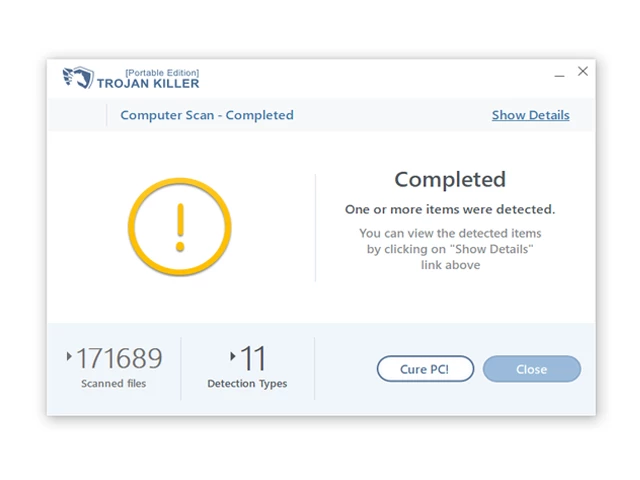
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
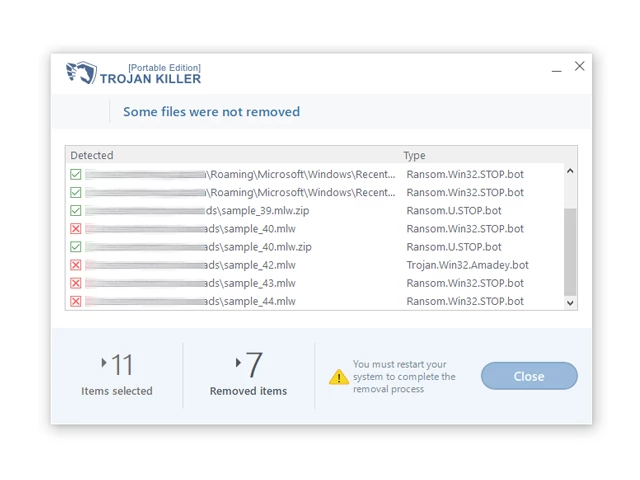
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing NightClub and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions (FAQ)
The NightClub malware is a sophisticated malicious program designed to perform data theft, monitoring files, and executing various commands on compromised devices.
The NightClub malware is attributed to a threat actor group known as MoustachedBouncer, which has been active for nearly a decade and primarily targets foreign embassies in Belarus.
NightClub malware is equipped with the ability to monitor files, exfiltrate data, download additional malicious modules, and execute commands on infected systems.
The exact distribution techniques used by NightClub malware are unknown, but malware in general is often spread through tactics like phishing emails, malicious attachments, deceptive downloads, and social engineering.
Older versions of NightClub malware targeted Microsoft Word (.doc, .docx), Microsoft Excel (.xls, .xlsx), and PDF (.pdf) documents. Newer versions, however, have more capabilities.
Versions of NightClub from 2016 onwards have the ability to retrieve and execute malicious modules from a Command and Control (C&C) server. These modules include keyloggers, screenshot capture, and audio recording.
The backdoor module allows the malware to execute various commands on the compromised system, such as creating processes, copying and moving directories, and reading, moving, and removing files.
NightClub malware itself does not typically self-propagate, but it can be distributed through various channels, including local networks and removable storage devices.
NightClub malware is associated with political and geopolitical attacks, indicating that its usage is likely driven by espionage and intelligence-gathering motives.
To safeguard against NightClub malware and similar threats, it’s crucial to maintain a strong security posture by employing reputable antivirus software, educating employees about phishing and social engineering, and keeping all software updated.
NightClub malware can lead to severe privacy breaches, financial losses, identity theft, and unauthorized access to sensitive information.
Upon detecting NightClub malware, immediate action is necessary. Quarantine the affected system, disconnect it from the network, and seek assistance from cybersecurity experts to analyze and remove the malware effectively.
Detection can be challenging due to the malware’s sophisticated nature, but regularly updated antivirus software, intrusion detection systems, and network monitoring can help identify signs of infection.
While specific efforts may not be detailed publicly, cybersecurity experts, researchers, and organizations are likely working to develop countermeasures and enhance security protocols to mitigate the threat of NightClub malware and similar malicious programs.
What is NightClub Malware?
Name: NightClub
Description: The NightClub Malware is a malicious software program that possesses advanced capabilities for data theft and surveillance. It is utilized by a threat actor group known as MoustachedBouncer. NightClub malware has multiple versions, with the earliest variant dating back to 2014. This malware is primarily associated with targeting foreign embassies in Belarus and is linked to political and geopolitical attacks. It is designed to monitor files, exfiltrate data, and execute various commands on compromised devices. The malware can also retrieve and execute additional malicious modules from a Command and Control (C&C) server, including keyloggers, screenshot capture, and audio recording functionalities. Its backdoor module enables unauthorized access and control over infected systems, allowing threat actors to carry out various operations. The NightClub Malware poses significant risks to privacy, data security, and system integrity, making it crucial for individuals and organizations to implement robust cybersecurity measures to prevent and detect its presence.
Operating System: Windows
Application Category: Malware


