Bleeping Computer reported that Italian company TG Soft has launched a new Have I Been Emotet service (similar to the well-known Have I Been Pwned), which checks if a specific domain or email address was used as a sender or recipient in Emotet spam campaigns.
TG Soft specialists say that their database contains chains of outgoing letters created by Emotet from August to September 23, 2020. During this time, researchers have collected more than 2,100,000 email addresses from approximately 700,000 outgoing emails, and the database continues to grow.For example, the service will warn user if an email account of the computer was hacked and used to send spam; will report if the email was stolen and used in spam campaigns; and will also notify you that you have received Emotet spam.
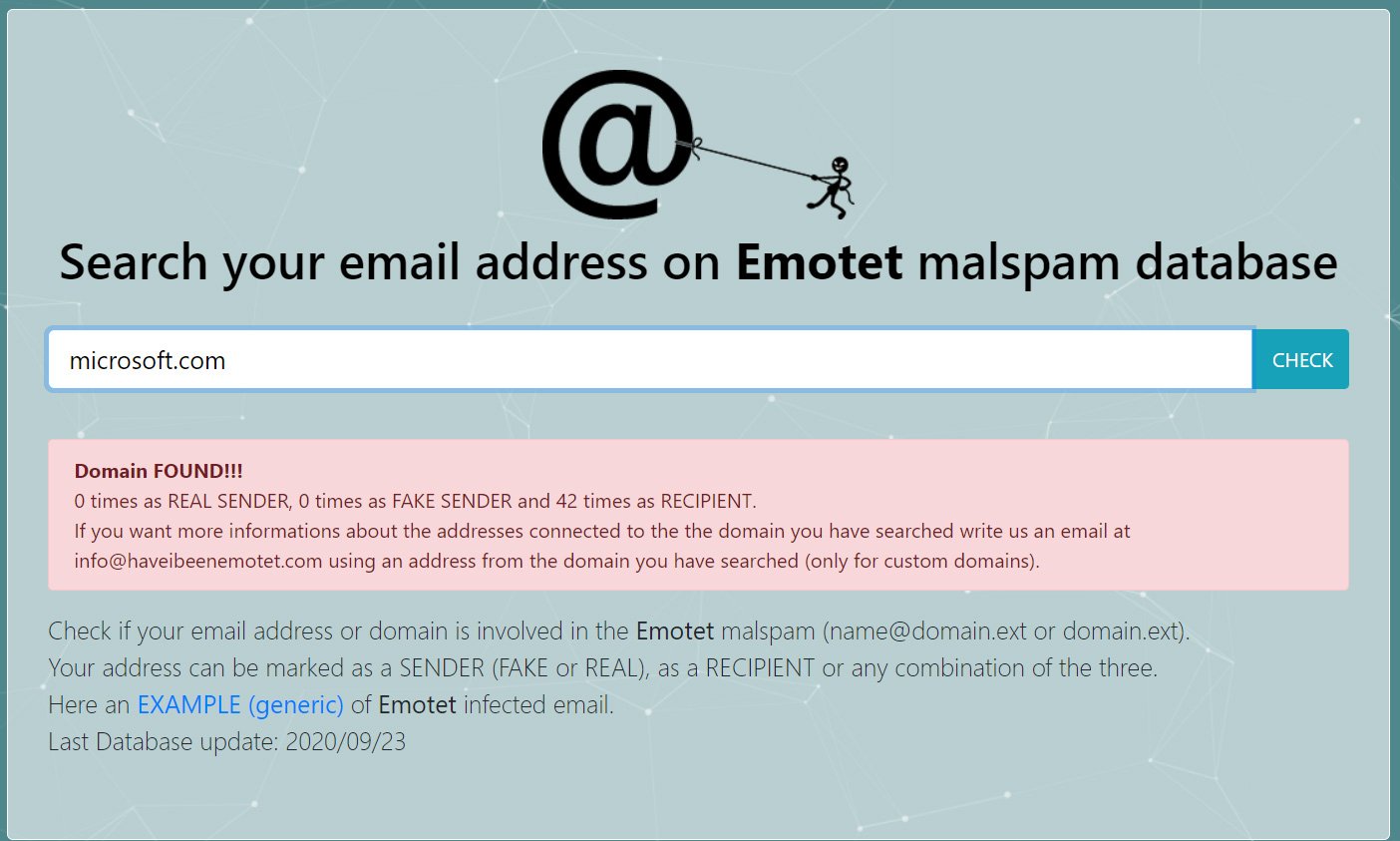
Below you can see the results of such a check: recently, Emotet attacked users in the microsoft.com domain 42 times.
Journalists note that the service can be useful as an auxiliary analytical platform: you can check whether the Emotet attacks targeted a specific company, and whether this ultimately led to the infection of the network by the ransomware. For example, ransomware Ryuk recently attacked health giant Universal Health Services (UHS).
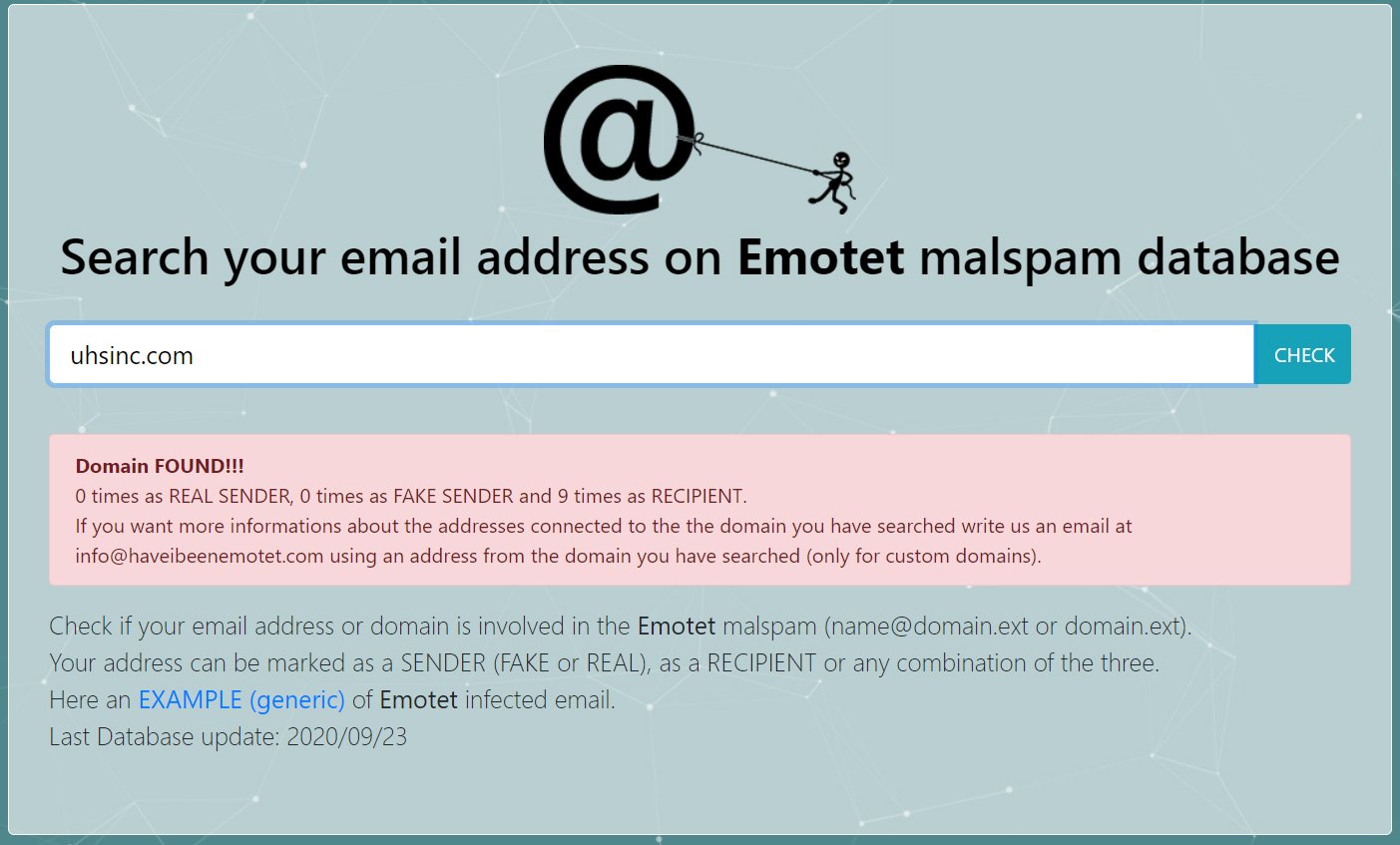
According to Have I Been Emotet, uhsinc.com has been attacked by Emotet campaigns at least nine times.
However, the fact of attacks and receiving malicious emails does not mean that a company or user has been compromised. To get infected, the user needs to open the attachment to the letter and allow macros to work.
Let me remind you that Italian developers are not the first who tried to “save the world” from the threat of Emotet. We wrote about a mysterious group of information security specialists who secretly vaccinate companies around the world against this infection.
Emotet appeared back in 2014 and now it is one of the most active threats among malware. The malware is distributed mainly via email spam, via malicious Word documents. Such letters can be disguised as invoices, waybills, account security warnings, party invitations, and even information about the spread of the coronavirus.
Although Emotet once started out as a classic banking Trojan, the threat has now changed dramatically, becoming a powerful downloader, and its operators have begun to actively cooperate with other criminal groups.
Today Emotet comes with many modules, which, in particular, allow malware to spread within the network. For lateral movement, for example, Emotet can even act like a Wi-Fi worm. Also recently, malware has been stealing attachments from its victims’ emails.
Having penetrated the victim’s system, Emotet uses the infected machine to send further spam, and also installs various additional malware on the device.
Read more about Emotet in our Threat Encyclopedia.
