This spring, we talked in detail about the Cryptolaemus enthusiast group. It became known that specialists from Cryptolaemus for six months have been secretly vaccinating companies around the world from Emotet.
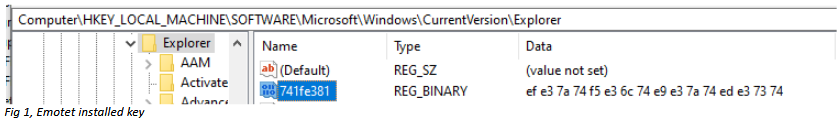
Cryptolaemus includes more than 20 cybersecurity specialists from all over the world, who in 2018 united for a common goal: the fight against Emotet malware. Back in February 2020, one of the team members, James Quinn from Binary Defense, discovered a vulnerability in the malware code.Then, studying the next Emotet updates, Quinn noticed a change in the code of one of the payloads. The change affected the so-called “resilience mechanism” of Emotet, which allows to malware to survive after rebooting of the infected device. It turned out that for this Emotet creates a special Windows registry key and saves an XOR key in it, the latter is used not only for stability, but also at the very beginning of infection.
Due to subsequent Emotet updates, which clarified how exactly worked the new resilience engine, Quinn was able to write a tiny PowerShell script called EmoCrash that used registry keys to cause Emotet to crash.
EmoCrash scanned the user’s computer and generated on the machine a correct registry key, though malicious for Emotet.
As a result, when a ‘clean’, but processed by EmoCrash computer was attacked, this registry key provoked a buffer overflow in the malware code, which ultimately caused Emotet to crash and prevented infection altogether”, – says James Quinn.
If EmoCrash was launched on already infected machines and replaced an existing registry key, the malware would also crash when it accessed the registry again. This effectively prevented communication between infected hosts and Emotet C&C servers.
Moreover, after that, crash logs containing event IDs 1000 and 1001 appeared on the machine. They could be used to identify endpoints with disabled and already “dead” Emotet binaries. This helped system administrators quickly detect that Emotet was trying to infect or had already infected their networks.
Binary Defense specialists understood that the news about this discovery must be kept secret, so that the authors of Emotet did not make corrections to their code. However, experts also understood that EmoCrash could help improve the protection of many companies around the world. As a result, the specialists joined forces with Team CYMRU, which for many years had been destroying botnets and at that time was watching Emotet.
Team CYMRU experts, in turn, contacted CERTs in many countries and tried to make EmoCrash secretly spread among various companies. The fact is that Team CYMRU maintains contact with 125 regional CERT teams, and also has its own mailing list, through which it regularly delivers useful and confidential information to more than 6,000 specialists.
Thus, over the past six months, the EmoCrash script has managed to spread widely among companies around the world.
We will never know how many companies ended up installing EmoCrash, but we have received many grateful messages from companies that have managed to prevent Emotet attacks or found themselves infected”, – say Binary Defense experts.
According to Binary Defense, their script significantly helped to reduce the number of infections and the number of bots.
Researchers believed that Emotet operators would never found out about their script and the fact that James Quinn discovered a bug in the malware code, but in early August 2020, six months after the vulnerability, hackers nevertheless changed work of resilience mechanism worked and eliminated the problem that EmoCrash relied on.
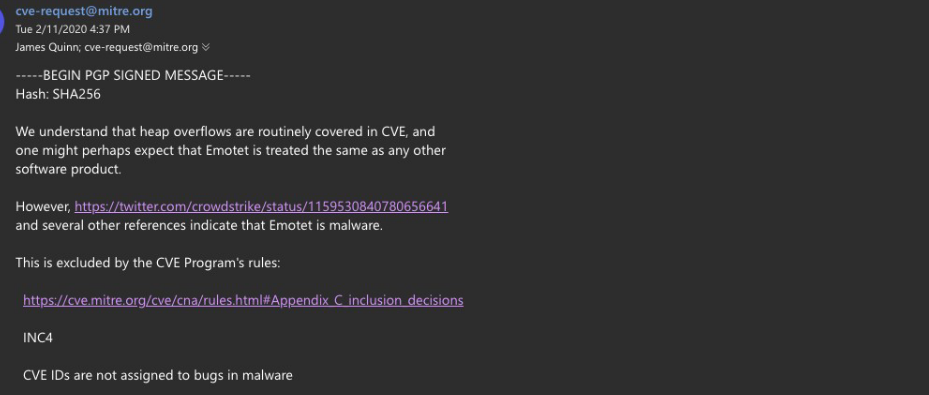
In a joke, James Quinn and his colleagues even turned to MITER and tried to get the CVE ID for the vulnerability they found in Emotet, like for any other vulnerability, but the organization noted that Emotet is malware and this goes against the rules of assigning CVE.
Reference:
Emotet appeared back in 2014 and now it is one of the most active threats among malware. The malware is distributed mainly via email spam and via malicious Word documents. Such letters can be masked as invoices, waybills, account security warnings, party invitations, and even information about the spread of the coronavirus. In short, hackers closely follow global trends and are constantly improving their decoy letters.
Read more about this malware in our encyclopedia of threats.