Dutch cyber security specialist Justin Perdok discovered that miners (at least one) can abuse the CI/CD function of GitHub Actions to force the company’s servers to mine cryptocurrency. It seems that such attacks do not harm user projects in any way, but they create a huge load on the GitHub infrastructure.
Interestingly, Perdock was not the first to notice such attacks, he only drew attention to the problem: they were first discovered by a French researcher known as Tib, who wrote that the attacks began in November 2020 and continue to this day.Perdock says that everything is based on creating a fork of the legitimate repository, adding malicious GitHub Actions to the source code, and then sending a Pull Request to merge the code back with the original.
At the same time, the hacker does not rely on luck, that is, the owner of the original project does not have to approve this malicious Pull Request at all.
As a result, after sending a malicious request, the GitHub systems process the attacker’s code and launch a virtual machine that downloads and launches cryptocurrency mining software in the GitHub infrastructure.
Bleeping Computer experts say that the miner disguises itself as npm.exe and communicates with the turtlecoin.herominers.com pool.
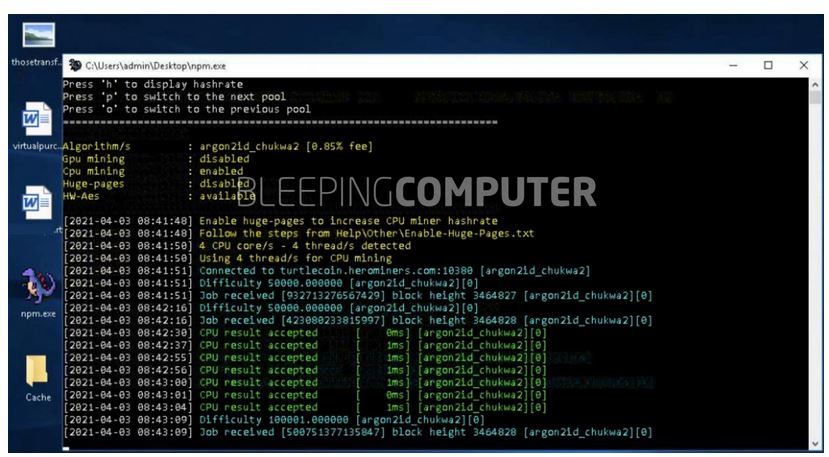
Perdock writes that he also became a victim of cybercriminals and watched as they used up to 100 miners in just one attack.
GitHub has already told the media that they are aware of what is happening and are actively investigating these mining abuses. However, the company gave the same answer to the French engineer last year.
Apparently, while the company is fighting the hacker by blocking his accounts, the attacker simply registers new ones as soon as the old ones are discovered and banned.
Even worse, Bleeping Computer reports that after the publication of these attacks, copycats have appeared on the network, abusing the same methods and using the GitHub infrastructure for mining. For example, one of the copycats sent over 50 malicious requests to legitimate repositories.
According to the publication, copycats use the open source XMRig miner and can download it directly from the official repository on GitHub.
Let me remind you that we talked about the fact that XMrig crypto miner switches from ARM devices to Intel servers.
