Analyst1 security researchers have calculated that the hackers behind the Maze and Egregor ransomware have already earned more than $75 million in ransoms from their victims. The company’s data is based on transactions that researchers were able to trace on public blockchains.
Interestingly, the experts’ conclusions are fully consistent with a similar report from Chainalysis, whose analysts believe that Maze ransomware is the third most profitable after Ryuk and Doppelpaymer.The hack group Maze firstly became famous in May 2019, offering other cybercriminals malware using the RaaS (Ransomware-as-a-Service) scheme.
Although many ransomware groups acted in a similar mode at the time, Maze made a name by creating a “leak site” where hackers listed infected companies and published data stolen from them. This tactic is still being used by ransomware as leverage on victims.
For unknown reasons, in the fall of 2020, the group stopped the work of the Maze ransomware, and his place was taken by Egregor, working on the same RaaS model.
For example, let me remind you that Egregor stool behind a campaign that I wrote about: Operators of the Egregor ransomware “leaked” data stolen from Ubisoft and Crytek into the network.
Soon after, many researchers began calling the faction behind Maze and Egregor Twisted Spider.
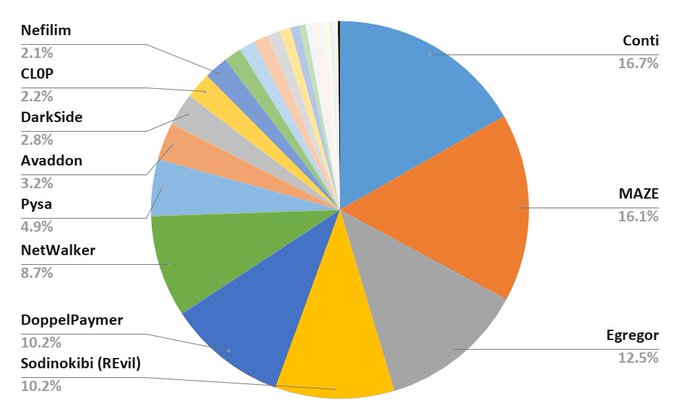
Currently, Maze and Egregor occupy the second and third places in terms of RaaS services activity, that is, they attacked a quarter of all victims appearing on “leak sites” over the past year.
The criminals are currently inactive: the group ceased its activities after three of its members were arrested by French and Ukrainian authorities in mid-February.
Then the Record, citing a high-ranking French police officer, reported that one of the key members of the group was among arrested criminals.
