Bleeping Computer reports that the well-known ransomware Maze, which has existed since May 2019, terminates its activity. It seems that the authors of Maze have decided to follow an example of their “colleagues”, GandCrab malware creators that closed development of their product in the middle of last year.
Journalists remind that Maze operators set a new trend among cybercriminals and firstly used “double extortion”. So hackers began not only to encrypt the data of their victims, but also began to publish files stolen from the attacked companies, if they refused to pay.Maze operators set up a special website for such “leaks”, and soon other groups, including Sodinokibi, DopplePaymer, Clop, Sekhmet, Nephilim, Mespinoza, and Netwalker, followed Mase’s example, using stolen data as additional leverage on victims.
Rumors about the discontinuation of Maze’s work began to reach journalists back in September 2020. So, some time ago, an attacker, which participated in the recent Barnes & Noble hack contacted Bleeping Computer.
The criminal said that he was engaged in ransomware attacks: hacking into company networks and stealing Windows domain credentials.
In a conversation with Bleeping Computer, the hacker also said that Maze is stopping its work, and the creators of the did not encrypt files of any new victims since September 2020, currently trying to get the remnants of ransoms from the companies affected by earlier.
When journalists tried to contact the developers of Maze themselves, they replied that they would not comment on these rumors and advised them to “wait for the official press release”.
However, the publication notes that this week, Maze operators began to clean up their “site for leaks”, and currently there is only information about two victims of hackers, as well as published earlier data from companies.
Often, after the completion of all operations, ransomware operators publish in the public domain all the keys necessary to decrypt data (for example, the creators of the malware Crysis, TeslaCrypt and Shade did this).
Therefore, Bleeping Computer journalists asked the authors of Maze if they were going to do the same, but did not receive an answer.
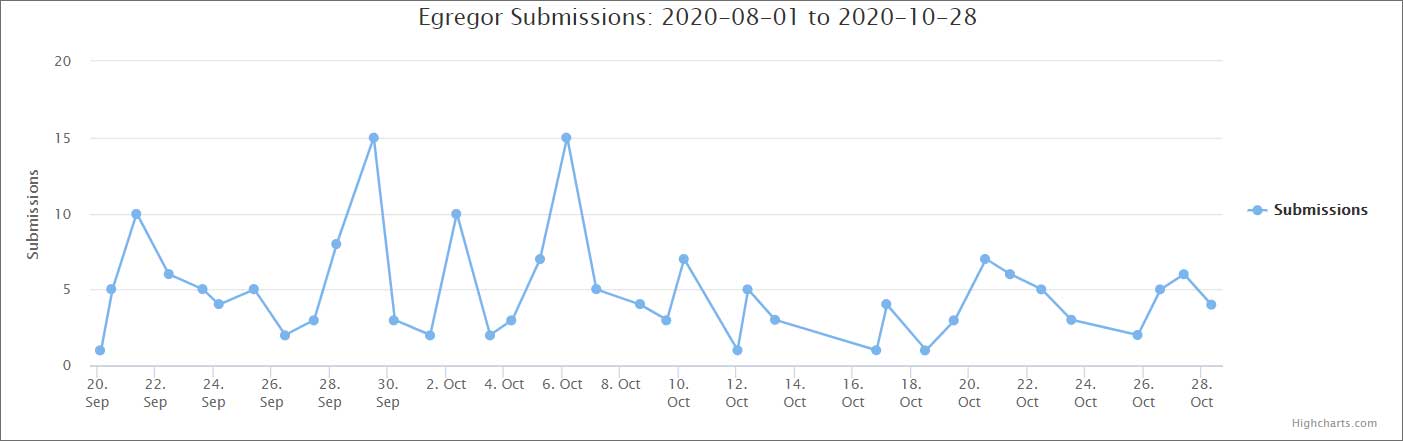
Interestingly, many Maze “partners” have already switched to using the ransomware Egregor, whose activity began in September 2020, just as the authors of Maze began to scale back their operations.
Security experts believe that Egregor is based on the same code on which the ransomware Maze and Sekhmet were previously built.The hacker who spoke to reporters also confirmed that Maze, Sekhmet and Egregor are essentially the same thing. In turn, information security specialist Michael Gillespie, who studied Sekhmet and Egregor, found that users who suffered from Egregor, and who paid the ransom, were sent a decryption software called Sekhmet Decryptor.
The journalists of the magazine summarize that the termination of the work of a particular ransomware does not mean “retirement” of its authors. Often hackers simply switch to new software and continue their ransomware operations.