IDP.ALEXA.54 is the detection of the heuristic engine of your antivirus (like Avast, AVG, or Avira), which may unexpectedly detect this virus. This detection means that it has found something that matches the characteristics of a known or suspected virus, malware, or potentially unwanted program (PUP).
IDP.ALEXA.54
In some cases, “IDP ALEXA 54” detections could be false positives, meaning that Avast or AVG has flagged a harmless file or application as suspicious. False positives can occur due to various reasons, such as outdated virus definitions, heuristics-based scanning, or similarities between the file and known malware patterns.
An Identity Protection Detection (IDP) component of Avast flags your files whenever they perform actions identical to malware that trigger the alert.
If Avast or AVG detects IDP.ALEXA.54, it is advisable to review the specific details provided by another antivirus program (as a second opinion) and adhere to any recommended actions, such as quarantining or removing the flagged files. Furthermore, conducting further research or seeking guidance from your antivirus provider can provide additional information and assistance regarding the handling of this detection.
Is IDP.ALEXA.54 a virus or a false positive detection?
Free versions of Avast, AVG, and Avira do not offer the users an automatic database update, as well as not able to remove viruses. Malware is constantly changing, so using an antivirus solution with the databases for 2017 in 2021 was pretty naive. Heuristic engines have this problem even more expressed. Without the updates, this element may falsely detect the elements of legit programs or files, claiming that they are suspicious. Such a “protection” is just a colander for possible viruses, but the danger of outdated bases is not over. Antiviruses with old detection databases often detect legitimate programs because a security tool thinks it is suspicious of its activity. And IDP.ALEXA.54 is one of such cases.
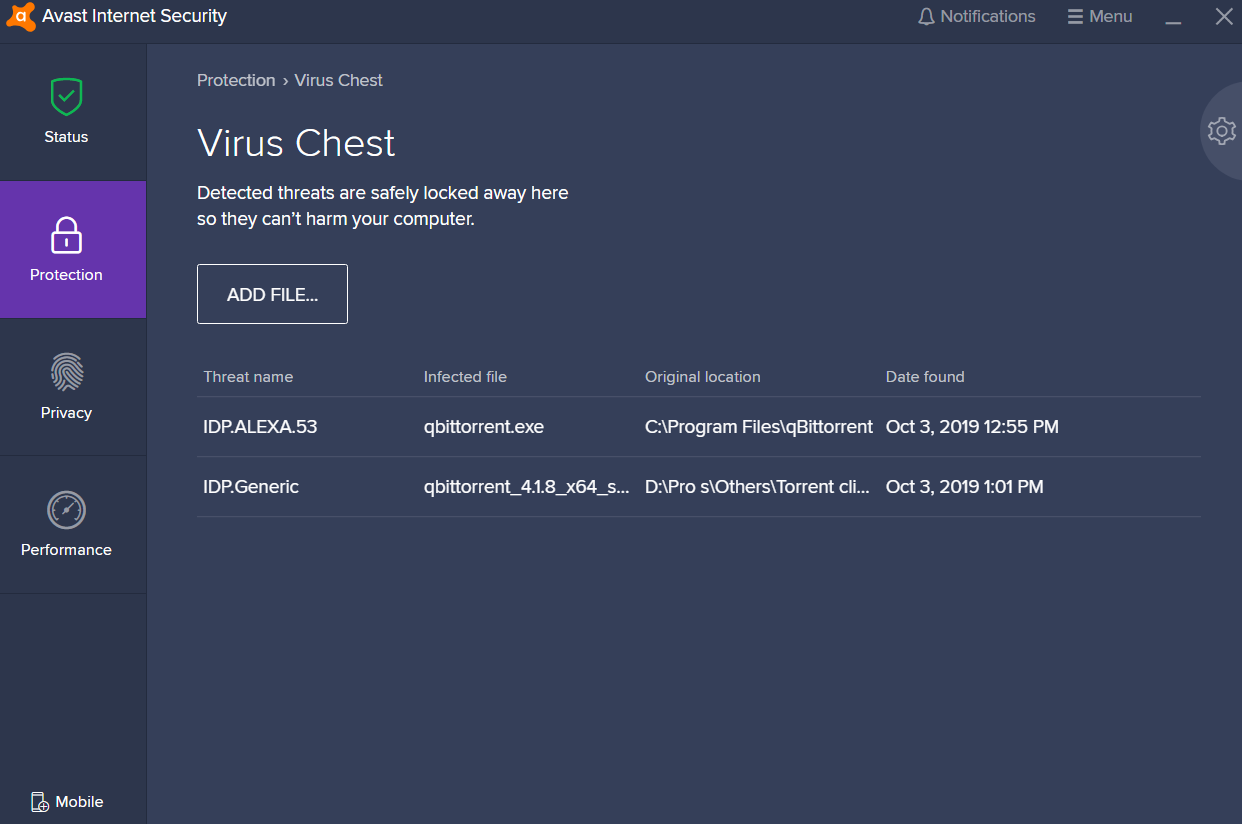
How to IDP.ALEXA.54 virus was detected by Avast
This “virus” may be a part of the program you use every day. It may also be a popular Flash game file called “Lovers” of all false positives. Most of the IDP.ALEXA.54 detections appear during the installation of SeaMonkey or Plants vs. Zombies. These games are 100% legit and do not carry any hazards to your PC. However, as I have already said, you need to be attentive because it is quite easy to miss a hazardous virus. Sometimes, the name ALEXA.54 is assigned to real viruses, usually – browser hijackers or adware.
How dangerous is it?
The list of viruses that can hide under this name is quite big. In most cases, they are browser hijackers and adware, which are not very dangerous if you remove them fast. But several reports are saying that there was spyware and coin miner under this name. Adware and browser hijackers are not very dangerous since they do not make any changes into system settings. You can easily detect that they are inside your PC. The symptoms are strange ads, popup banners, randomly opening browser windows, and search engine changes.
Here is the short review for this threat:
| Name | IDP.ALEXA.54 |
| Type | False detection, adware, browser hijacker, spyware, coin miner |
| Reason of appearance | Outdated detection databases of the antivirus tool |
| Possible source | Software bundles, email spam, malvertising |
| Removal method | To remove possible virus infections, try to scan your PC |
Spyware and coin miners are much more stealthy. Their efficiency depends on the time they were active without detection. Quite a straight motivation to leave no paths in your system, isn’t it? And the damage they may carry is much bigger than adware, even if you remove it as soon as possible. Spyware is just a nuke for your privacy since it collects and passes all possible data about you and your system and then transfers it to its control center. Coin miner is easier to detect since it consumes a huge amount of your computer’s resources. But many users ignore enormous CPU load, blaming the bad hardware or unoptimized Windows OS for the lags.
How did I get this virus?
If IDP.ALEXA.54 is a virus, it can spread differently. But these days, the biggest share of virus distribution is after software bundles, email spamming, and malvertising.
Email spamming became a viral malware distribution method since the users do not raise suspicion on notifications from DHL or Amazon about the incoming delivery. However, it is pretty easy to distinguish the nasty email from the original one. The sender’s email address is a perfect indicator of the “originality” of that letter.
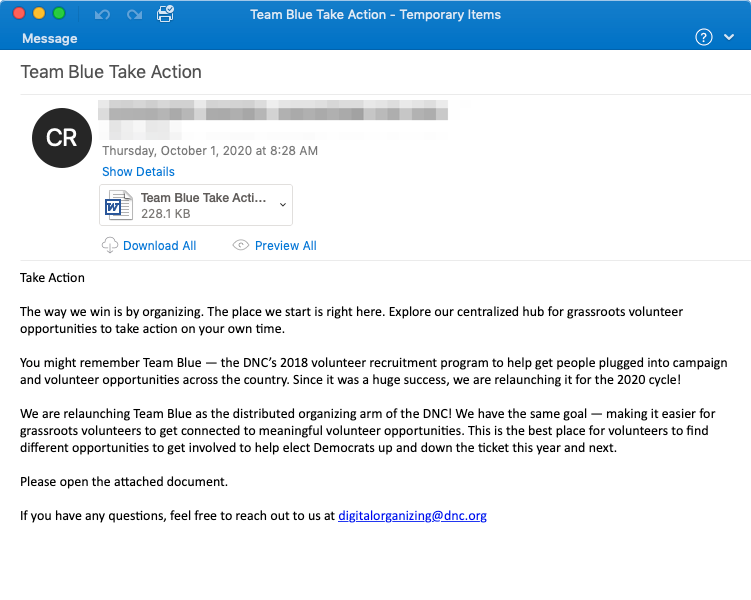
The example of email spam
Malicious advertisements on the web, however, are an old-timer of malware distribution. The advice to stop clicking the blinking advertisements on untrustworthy websites exists as long as the ads are on the Internet. You can also install ad-blocking plugins for your web browser – they will deal with any ads.
Software bundling is a widespread practice among virus developers. Users who hack the programs to make them usable without purchasing a license approve any offer to include another program in the pack because they are gaining money in such a way. Check precisely the installation window for signs like “Advanced installation settings” or so. The ability to switch off the malware installation often hides under such items.
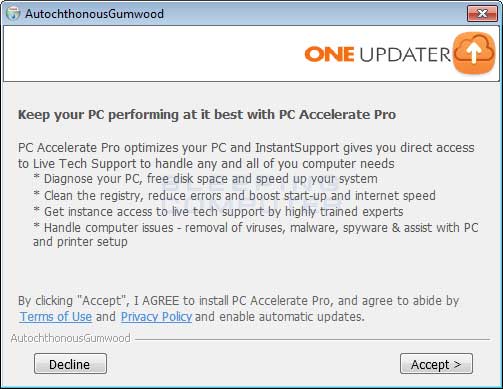
The example of bundle software installation
What to do with IDP.ALEXA.54?
Free AVG, Avast, and Avira variants are scanners that cannot remove viruses and perform proactive protection. As was mentioned several times, this detect name is typical for false positives, as well as for various viruses. If you have the symptoms I have described in previous paragraphs, check your computer with anti-malware software. My choice is GridinSoft Anti-Malware1. Its databases are constantly updating, and it has malware removal functions and proactive protection.
Remove IDP.ALEXA.54 with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Heuristic viruses as shown from our tests with the software, and we assure you that it can remove IDP.ALEXA.54 as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
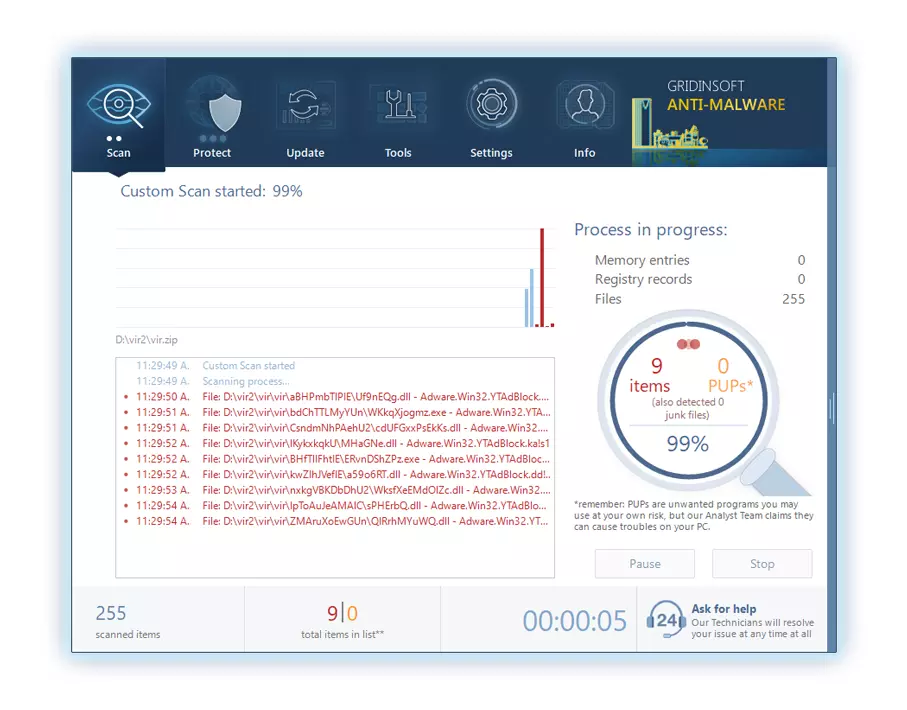
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
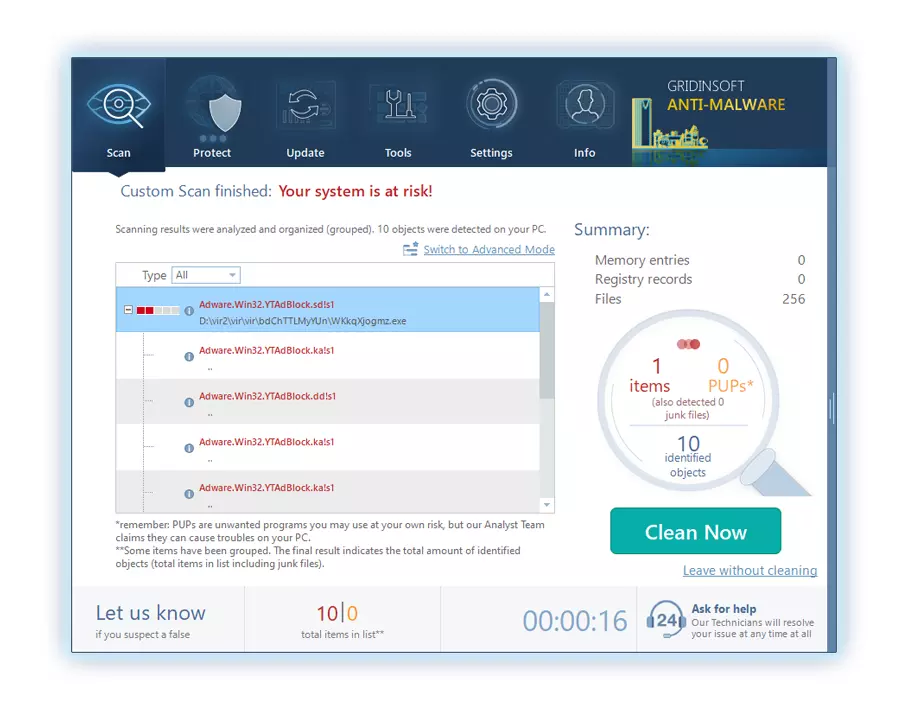
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
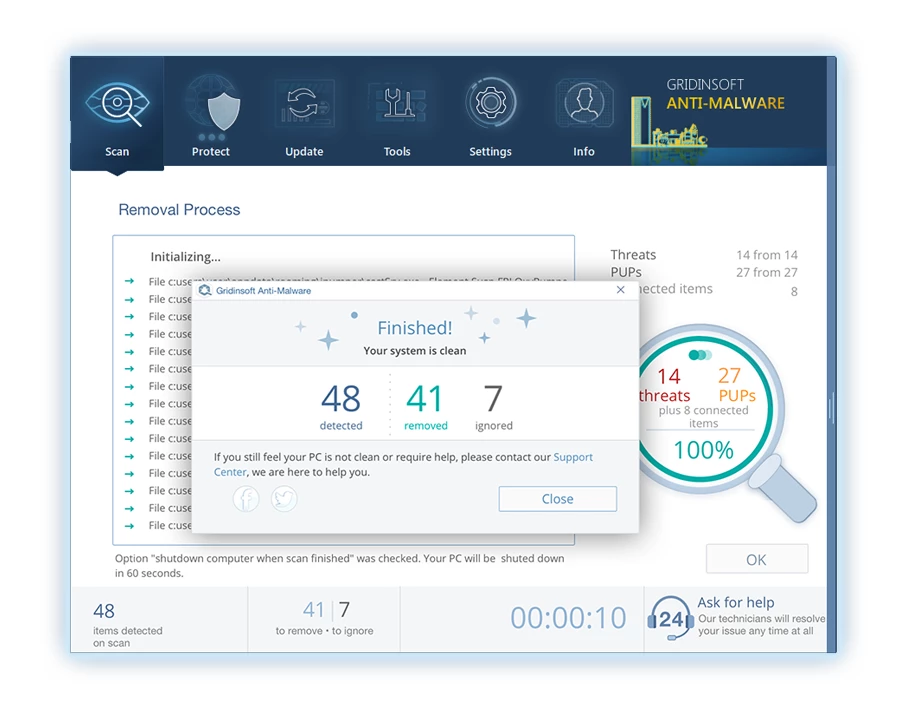
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “IDP.ALEXA.54” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
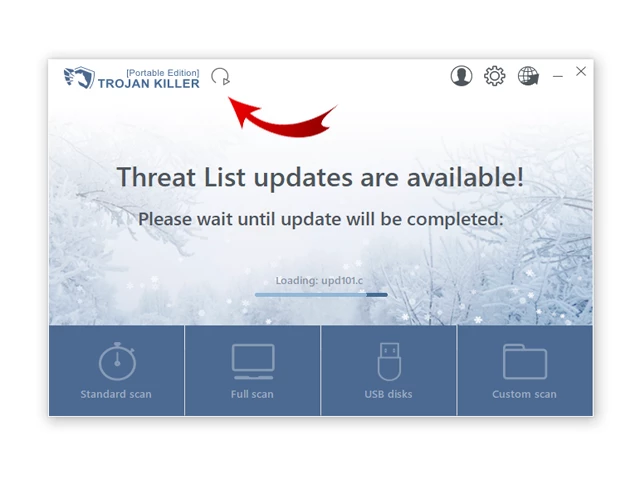
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
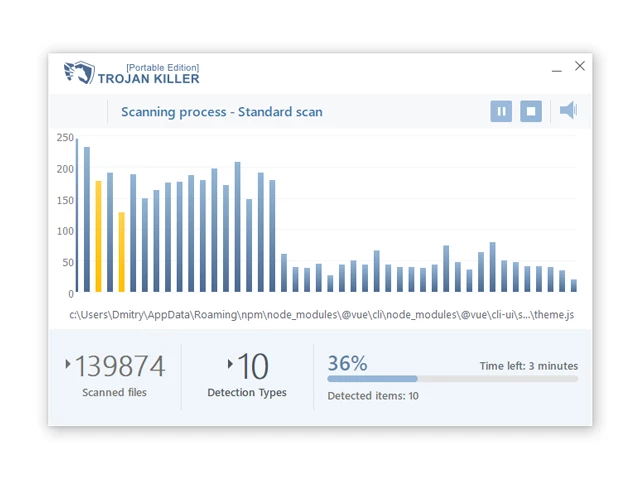
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
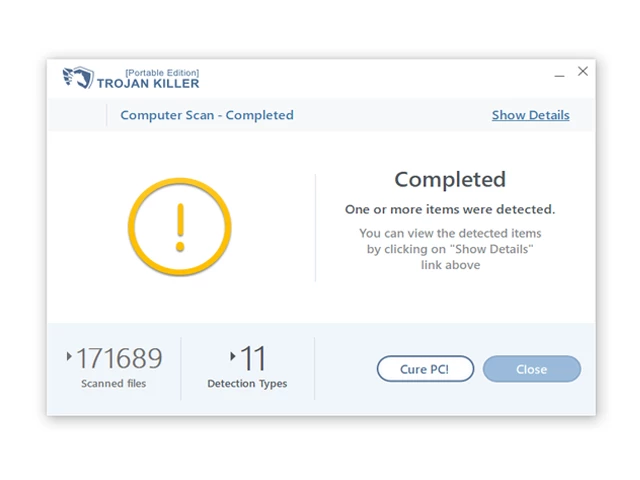
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
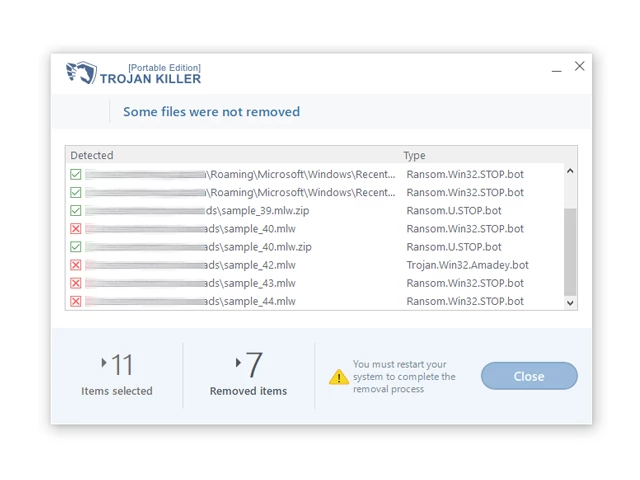
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing IDP.ALEXA.54 and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Avast Detections
- IDP.HEUR.26 Malware: A Complete Removal Guide
- URL:Scam
- IDP.ALEXA.54 Dangerous or Avast (AVG) False Positive?
- IDP.Generic Malware ✔️ Avast IDP Generic Detection
- Win32:BogEnt Virus (Avast Detection)
- Win32:Trojan-gen Avast Virus
- URL:Phishing Avast Virus Detection: What Is It?
- URL:TechScam Avast Virus (TechScam Detection)
- URL:Blacklist (Blacklisted URL) Avast Detection
- IDP.HEUR.24 Virus Detection by Avast
User Review
( votes)References
- Reasons why do I recommend you to use GridinSoft Anti-Malware.



