Hewlett Packard (HP) specialists have fixed a critical vulnerability by releasing patches to eliminate CVE-2021-39238, which affects more than 150 models of the company’s MFPs, including top HP products (such as LaserJet, PageWide and ScanJet).
The problem has the potential of a worm, which means it can spread to other vulnerable HP printers inside corporate networks or over the Internet.CVE-2021-39238 is the most serious of several vulnerabilities recently discovered by experts at F-Secure. According to them, the bugs appeared in the HP code back in 2013, and all this time the owners of vulnerable devices were at risk. On November 1, 2021, HP engineers released firmware updates for two of the most critical bugs found by researchers: CVE-2021-39237 and CVE-2021-39238.
The first vulnerability, CVE-2021-39237, relates to two open ports that provide full access to the device. Its operation requires physical access to the MFP, the attack itself takes up to five minutes and can lead to data disclosure.
The second vulnerability, CVE-2021-39238, is much more serious and received 9.3 points out of 10 on the CVSS scale. It is associated with a buffer overflow in the font parser and provides attackers with the ability to remotely execute code. Worse, as mentioned above, the bug has the potential of a worm, that is, it can quickly spread from one printer to the next.
The researchers write that the discovered problems can be attacked using a variety of attack scenarios. For example:
- printing from USB drives, which the experts themselves practiced during the tests (in new firmware versions, printing from USB is disabled by default);
- using social engineering to print a malicious document: an exploit for CVE-2021-39238 can be embedded in a PDF file;
- printing via direct connection to a physical LAN port;
- printing from another device on the same network that is under the control of an attacker;
- XSP: Sends the exploit to the printer directly from the browser using a POST request on JetDirect port 9100 / TCP;
- direct attack on open UART ports if an attacker has physical access to the device.
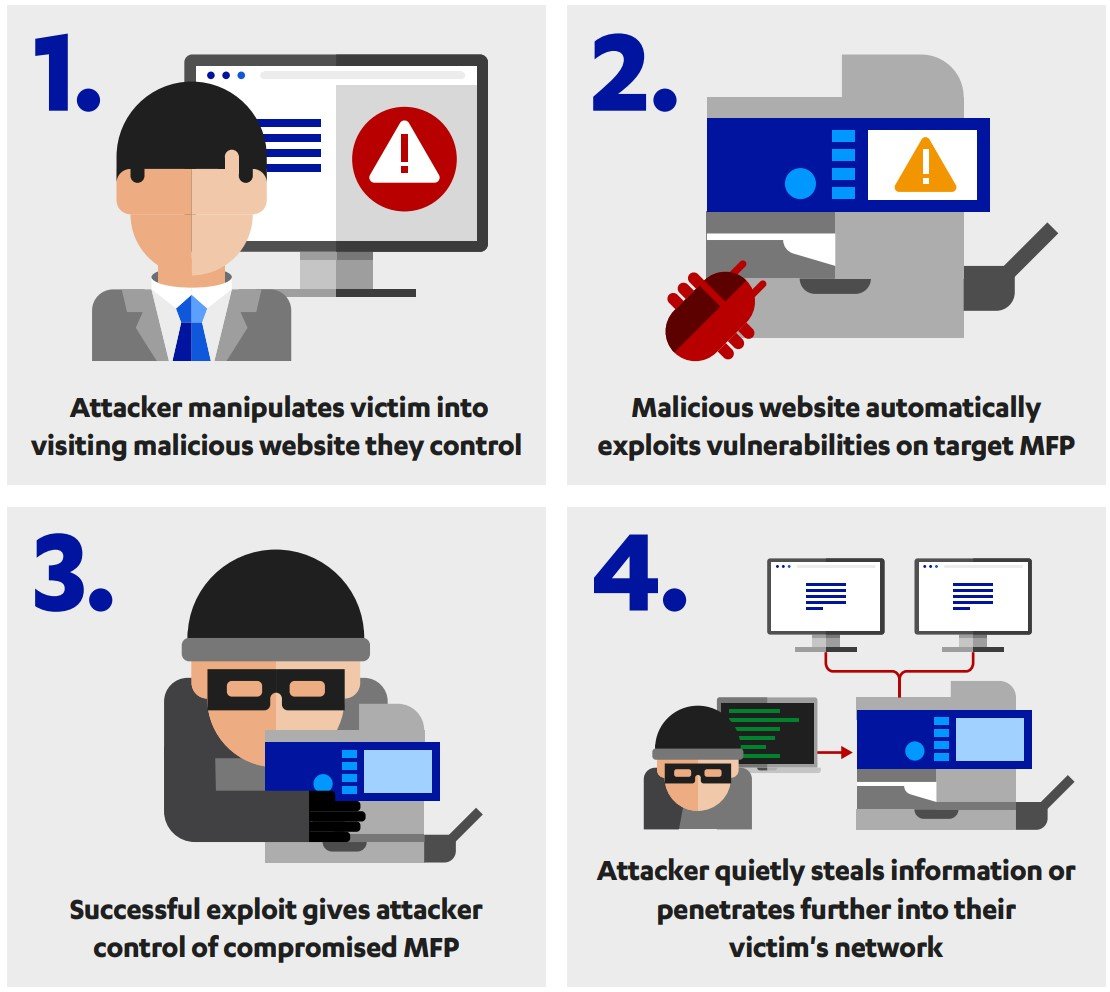
In addition to updating the firmware of vulnerable devices, the researchers advise administrators to take the following actions to mitigate the risks: disable USB printing; put the printer in a VLAN behind a firewall; allow outgoing connections from the printer only to a specific list of addresses; set up a dedicated print server for communication between workstations and printers.
Let me also remind you that we wrote that Brother printers may not work in Windows 11.
