The researcher noticed that hackers are using a fake captcha to force users to bypass browser warnings and download the banking Trojan Gozi (aka Ursnif).
The problem was discovered by information security researcher MalwareHunterTeam, who shared his findings with Bleeping Computer journalists.It all started when an expert found a suspicious URL on the Internet, where, when trying to watch an embedded YouTube video about a women’s prison in New Jersey, the file console-play.exe was downloaded, and the site displayed a fake version of reCaptcha on the screen.
Since the file is executable, Google Chrome automatically warns that the file may be malicious and asks if the user wants to “Save” it or “Cancel” the download. To bypass this warning, attackers show the victim a fake reCAPTCHA, where the user is asked to press the B, S, Tab, A, F, and Enter keys on the keyboard, as shown in the screenshot below.
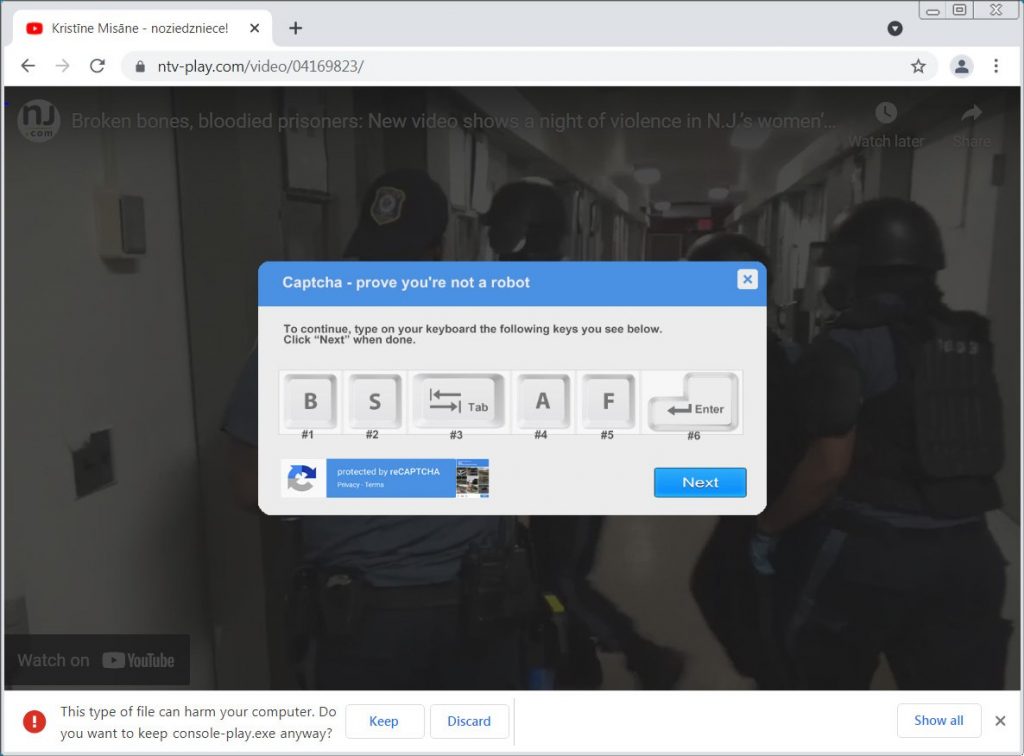
If nothing happens when you press the “B”, “S”, “A” and “F” keys, then pressing “Tab” will move the focus to the “Save” button, and then pressing the “Enter” key will work as a click on this button, forcing the browser to download and save the file to your computer.
Moreover, the video will eventually start playing automatically, that is, the user will decide that he entered the captcha successfully.
If the victim launches the mentioned executable file, it will create a folder in% AppData%\Bouncy for .NET Helper and install many files into it. All of these files are fake, with the exception of the executable file BouncyDotNet.exe.
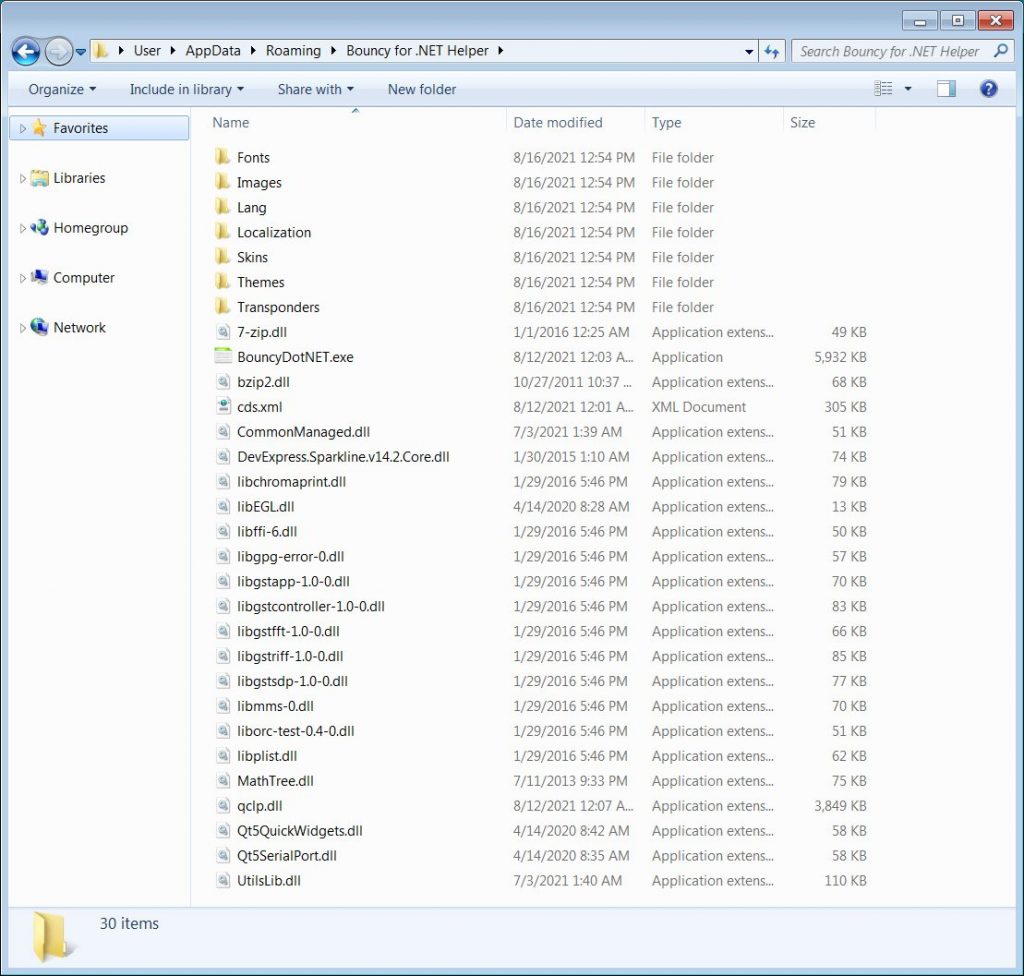
BouncyDotNet.exe will read various lines from the Windows registry used to run PowerShell commands. These commands will eventually compile the .NET application using the built-in compiler CSC.exe, which will run the Ursnif banking trojan DLL.
Once launched, the Gozi banker will steal the victim’s credentials, download additional malware to the computer, and execute any commands sent to it by remote attackers.
By the way, we recently reported that One of the developers of Gozi malware was arrested in Colombia, but the spread of malware did not stop it.
