Last week, Conti ransomware attacked the Health Service Executive (HSE) of Ireland, as well as the country’s Ministry of Health. If the Ministry of Health managed to abandon the attack in time, the HSE was less fortunate.
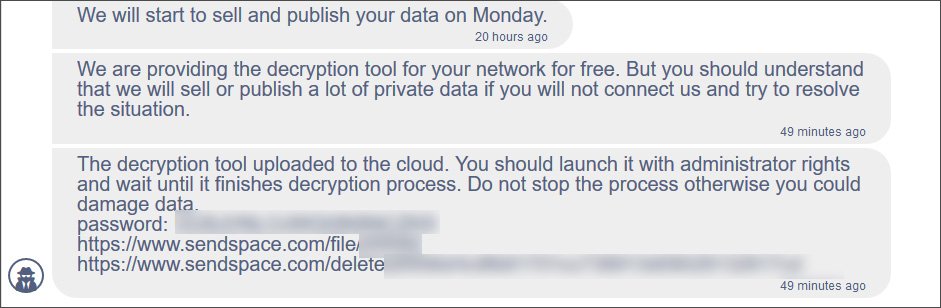
Although the attack did not affect the provision of emergency medical care, it was reported that some scheduled examinations and procedures could still be postponed or cancelled, as medical staff lost access to online systems, electronic patient records and other medical records.As Bleeping Computer now reports, the ransomware operators have posted a link to a free data decryptor on the page intended for negotiations with the HSE. The publication confirms that the tool works, but the Irish government has said that a technical analysis of the tool will be carried out for harmful properties before usage.
Despite the publication of the decryptor, the attackers warned that they still intend to sell or make publicly available the data stolen from the HSE (about 700 GB), if they are not paid a ransom in the amount of $19,999,000.
As a result, the Irish High Court has issued an injunction against the Conti operators, which states that data stolen from the HSE must be returned to the owner, but in no case sold or published. Government officials uploaded the restraining document to the hackers’ darknet site. The paper also says that attackers are required to identify themselves by providing their names, email addresses and physical addresses. Of course, the chances of Conti’s operators giving in to the authorities’ demands are negligible.
Meanwhile, the FBI reports that Conti has attacked 16 US healthcare facilities and first responders (including law enforcement, emergency medical services, 911 dispatch centres, and municipalities) over the past year.