Proofpoint specialists discovered a hack group, which was assigned the ID TA2541. The researchers believe that the attackers have been operating since 2017 from Nigeria, and their activity is focused on several industries, including aviation, defense and transportation in North America, Europe and the Middle East.
According to the researchers, the participants of TA2541 have very low qualifications, care little about the secrecy of their actions, and often use ready-made malware. The activity of the group has previously attracted the attention of other companies and fell into the reports of Cisco Talos, Mandiant, Microsoft, Morphisec and independent researchers.Typically, attackers rely on mass phishing emails, which are almost always written in English, to encourage victims to download malicious files (usually Microsoft Word documents) hosted in cloud storage, as hackers realize that such links are almost never blocked inside large companies. The mass character of such spam campaigns could vary from hundreds to several thousand letters.
After downloading and running such a file, malware is installed, namely a remote access trojan (RAT), which provides TA2541 participants with access to an infected computer.
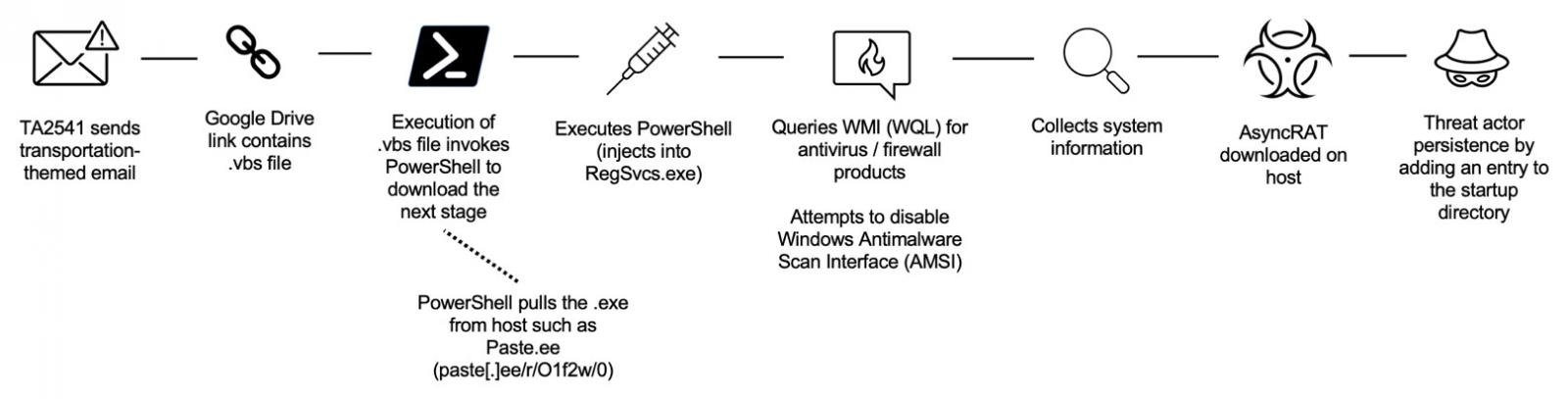
Proofpoint writes that over the years of its existence, the group has used a variety of RATs for these purposes, but almost always relied on the malware that can be purchased on hacker forums. The group’s favorites seem to be AsyncRAT, NetWire, WSH RAT, and Parallax, which are the most commonly used in attacks.
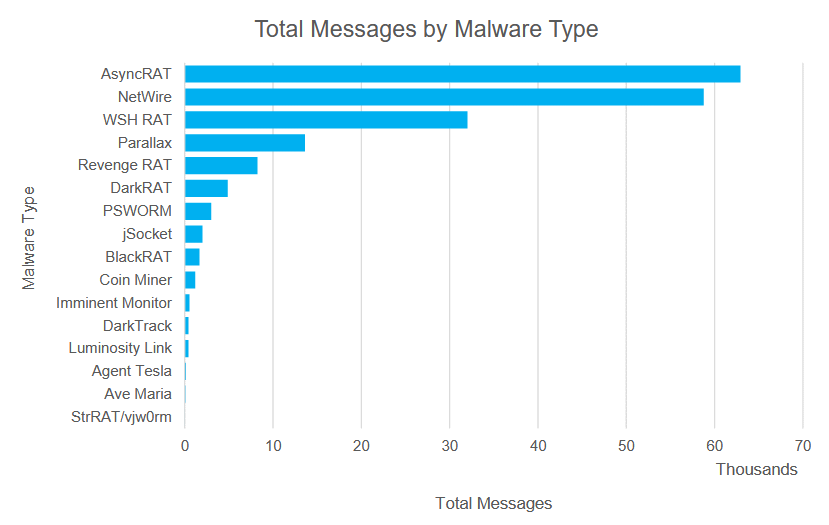
All the malware used by TA2541 can be used to collect information, but the ultimate goal of the attackers is still unknown.
Let me remind you that we also wrote that Hackers Send Anti-Capitalist Spam to Receipt Printers, and also that Spammer bombarded the Babuk ransomware forum gay porn.
