Users of the OpenSea NFT marketplace are exposed to phishing attacks from fake Discord support, the purpose of which is to steal funds in cryptocurrency and NFTs, says Bleeping Computer.
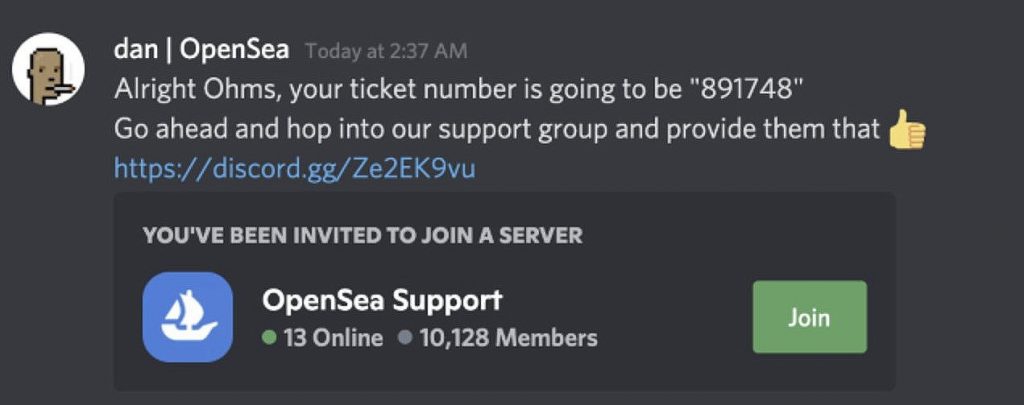
The attackers acted on the OpenSea Discord server, posing as official representatives of the site’s support service. Fraudsters offered help to OpenSea users, which invariably resulted in the loss of cryptocurrency and NFTs stored in victims’ MetaMask wallets.The point is, if an OpenSea user needs support, they can request help from the OpenSea Help Center or through the Discord site. When a user joined Discord and sent a request for help, the scammers began to send the victim private messages inviting them to a supposedly dedicated OpenSea Support server (fictitious, of course).
The artist Jeff Nicholas, who was the victim of this scam, told reporters that on a fake support server, scammers asked him to provide remote screen access so that they could help and provide recommendations on how to fix the problem.
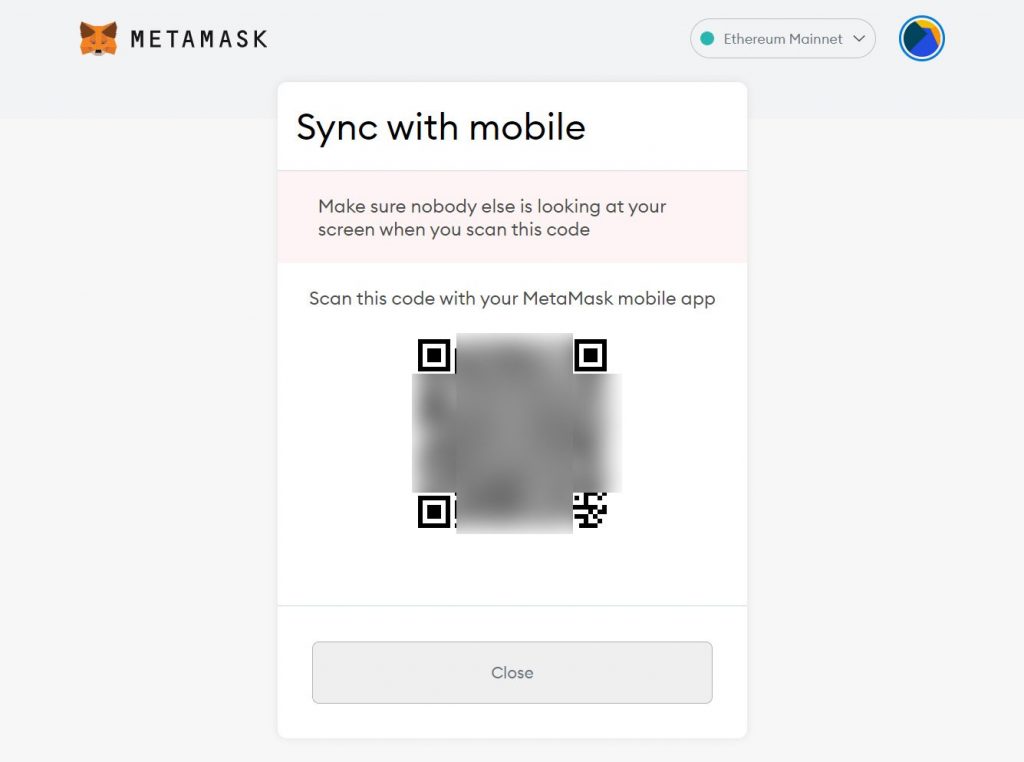
The victim was then informed that he needed to re-sync his MetaMask Chrome extension with the MetaMask mobile app. During this, a QR code is displayed on the user’s screen, which he must scan, but scammers use it. After the appearance of the QR code, the user almost immediately sees a message that the application is synchronized, because the code was used by criminals.
When scammers scan a victim’s QR code on their mobile app, they gain full access to the cryptocurrency and everything stored in the NFT wallet. Then the attackers simply transfer funds to their wallets.
OpenSea representatives say they are aware of these attacks and recommend that users contact support through the site’s help center.
Some users disagree with this position of the company and believe that OpenSea is also responsible for the incidents, as it sent users to its Discord server for support and did not control what was happening there.
Let me remind you that we also talked about the fact that Hackers are interested in NFT and hack Nifty Gateway users.