Researchers from Check Point talked about critical bugs that they found on the world’s largest NFT marketplace OpenSea. To steal someone else’s cryptocurrency, the attacker simply had to force the user to click on the malicious NFT image.
OpenSea is the largest marketplace where you can buy and sell NFTs (non-fungible tokens) and other assets. The volume of its transactions in August 2021 alone amounted to 3.4 billion US dollars. Check Point experts decided to conduct a study on OpenSea, having noticed a lot of messages on the network about free NFTs that were allegedly distributed to users. Soon, the researchers managed to contact the victim of the scammers, who reported that her cryptocurrency wallet was hacked, and shortly before that she interacted with one of these free airdrops.The fact is that an OpenSea account requires a third-party cryptocurrency wallet from the list of supported by the platform. One of the most popular solutions is MetaMask, which the researchers chose. The connection with the wallet is established in almost any action: even if you just click on some NFT, this triggers a request to enter the wallet.
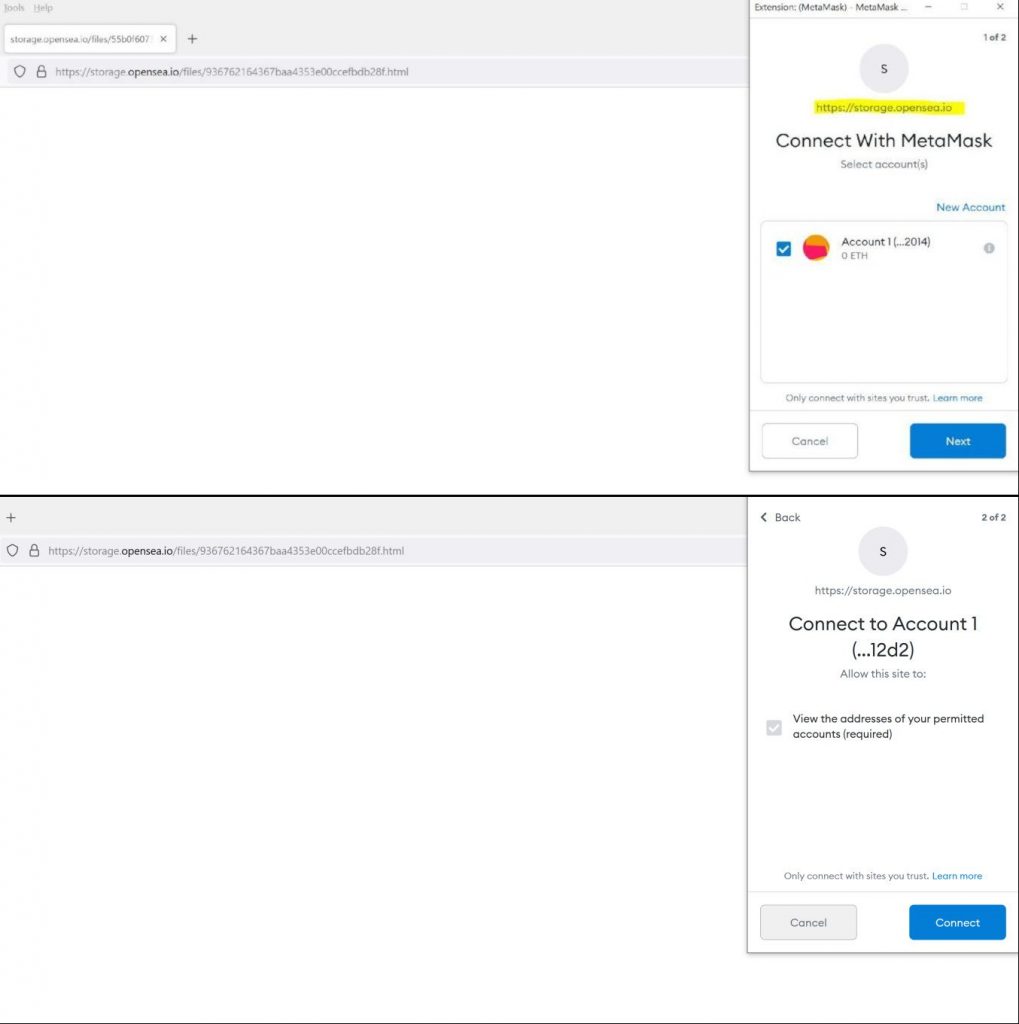
It is worth explaining that on OpenSea anyone can sell digital art as files up to 40MB in size with any of the following extensions: JPG, PNG, GIF, SVG, MP4, WEBM, MP3, WAV, OGG, GLB, GLTF. Knowing this, Check Point experts uploaded an SVG image containing malicious JavaScript to OpenSea. When I clicked on it to open it in a new tab, I found that the file was running in the storage.opensea.io subdomain. The researchers then added an iFrame to the image to load the HTML code that would inject the window.ethereum request needed to communicate with the victim’s Ethereum wallet.
As a result, after understanding the problem, experts were able to identify critical vulnerabilities in OpenSea, proving that malicious NFTs can be used to hack other people’s accounts and steal cryptocurrency. It turned out that the following simple steps were required to successfully exploit marketplace vulnerabilities.
- The hacker creates and presents the victim with a malicious NFT.
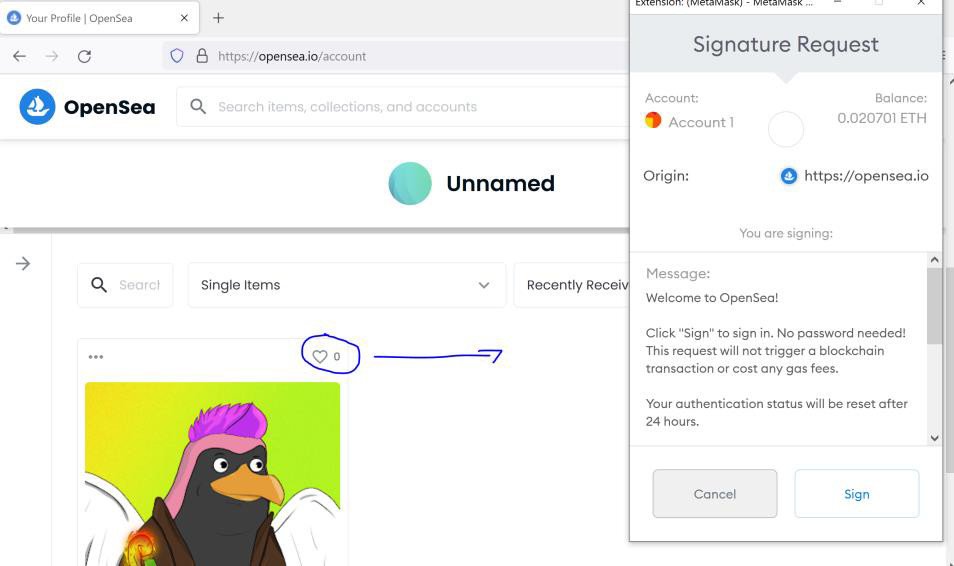
- The victim browses the malicious NFT and sees a pop-up window where he is asked to connect to a cryptocurrency wallet (such pop-ups are often found on the platform during various other actions);
- The victim clicks on the button to connect to his wallet to perform an action with the donated NFT, and as a result provides access to the wallet to the attacker;
- To steal funds, the hacker displays another pop-up window, which is also associated with the OpenSea storage domain.
- If the user does not notice the transaction note in this pop-up window in time and clicks on it, the attacker will be able to steal the cryptocurrency. Alas, such requests often appear as “system notification” and users are more likely to approve the transaction without even reading the message.
Researchers reported the issues to the OpenSea developers on September 26, 2021. In less than an hour, the issue was resolved and experts confirm that all attack vectors are now closed.
Let me remind you that we also talked about the fact that Fake OpenSea support steals NFTs and funds from cryptocurrency wallets.